Home → LOGbinder for SP KB → Printer Friendly Version
LOGbinder for SP KB
- 1. Most Used
- 2. Getting Started Guide
- 2.1. Installing LOGbinder for SharePoint
- 2.2. Configuring LOGbinder for SharePoint
- 2.3. Monitoring LOGbinder for SharePoint
- 2.4. Appendix A: Assigning Permissions
- 2.5. Appendix B: LOGbinder Event List
- 2.6. Appendix C: Diagnostic Events
- 2.7. Appendix D: Configuring auditing on a SharePoint list or document library
- 3. How To
- 3.1. How does LOGbinder for SharePoint detect log tampering?
- 3.2. How to reduce the number of audit events
- 3.3. Why are User ID's prefixed with "i:0#.w" in LOGbinder for SharePoint?
- 3.4. LOGbinder SP use of SQL Privileges
- 3.5. Workaround if LOGbinder for SharePoint is having SQL database issues
- 3.6. How To Set SPDataAccess on Large Number of Content Databases
- 3.7. Impact of Restricted Lookups
- 3.8. Can't connect to SQL database WSS_Content?
- 3.9. Default Audit Policy Options
- 3.10. LOGbinder for SharePoint Restricted Lookups Option
- 3.11. Audit log truncation and audit integrity
- 3.12. FIPS Mode and LOGbinder software
- 3.13. New technical updates posted and available for customers with current maintenance and support contracts - July 2015
- 3.14. “Run as Administrator” may be needed to initialize LOGbinder for SharePoint
- 3.15. Tech Tip: Manage the audit performance by tweaking the amount of excess information attached to the audit
- 3.16. Where to find information about LOGbinder events
- 3.17. You want to run audit reports in SharePoint but LOGbinder for SharePoint purges the audit log
- 3.18. Why There's No Event for List Item Views
- 3.19. How to change the LOGbinder service account password
- 3.20. Diagnostic logs – Use them and let them go
- 3.21. LOGbinder troubleshooting tip: Use the Diagnostic Logs
- 3.22. LOGbinder for SharePoint 6 Features
- 3.23. How to Audit an Individual Library or List in SharePoint
- 3.24. Recovery options for LOGbinder service
- 3.25. New Syslog Features in LOGbinder SP 4.0.5
- 4. Resources
1. Most Used
1.1. Download LOGbinder for SharePoint
Click here to download LOGbinder for SharePoint.
1.2. LOGbinder Newsletter
Click here to subscribe to one of our newsletters.
2. Getting Started Guide
2.1. Installing LOGbinder for SharePoint
LOGbinder for SharePoint runs as a Windows service on a SharePoint server. It translates audit log entries in SharePoint, and outputs them to the LOGbinder SP event log, the Windows Security Log, a Syslog server or Syslog files.
| For more information, please visit our web site https://www.logbinder.com/Products/LOGbinderSP/#tabs-Resources. There you will find a rich set of resources to guide you in setting audit policy, setting up audit log reporting and archiving, and so forth. |
Installing LOGbinder for SharePoint involves 3 simple steps:
- Step 1 – Select Server and Check Software Requirements
- Step 2 – Check User Accounts and Authority
- Step 3 – Run the Installer
Subsequent sections cover:
- Configuring LOGbinder for SharePoint
- Monitoring LOGbinder for SharePoint
Step 1 – Select Server and Check Software Requirements
Select Server
If SharePoint is installed in a server farm environment, then LOGbinder for SharePoint would be installed on a single application, web front end or central admin server. Do not install LOGbinder for SharePoint on dedicated SharePoint database servers because the necessary SharePoint components are not present.
Software Requirements
- Microsoft Windows Server 2012 or later 64-bit versions
- Microsoft .NET Framework 4.8 or later
- Microsoft SharePoint (one of the following):
- Microsoft SharePoint Server 2013 (including SharePoint Services/Foundation)
- Microsoft SharePoint Server 2016
- Microsoft SharePoint Server 2019 (including Subscription Edition)
Step 2 – Check User Accounts and Authority
Two user accounts are involved with LOGbinder for SharePoint.
- Your account
- The account you are logged on as when you install and configure LOGbinder for SharePoint.
- Authority Required:
- Member of the local Administrators group
- Windows UAC sometimes interferes with this setting. It is recommended that you use the “Run as Administrator” option when running LOGbinder. You may also need to give your account as well as the service account modify permissions to the C:\ProgramData folder as described in the fourth bullet point below.
- SharePoint farm administrator
- Member of the local Administrators group
- Service account
- The account that the LOGbinder for SharePoint (LOGbinder SP) service will run as. This domain account must be created before installing LOGbinder for SharePoint. This account does not need to be a local or domain administrator; the LOGbinder for SharePoint (LOGbinder SP) service can run in a least-privilege environment.
- Authority Required: (See Appendix A: Assigning Permissions for details on granting these permissions)
- SharePoint farm administrator
- Member of the WSS_ADMIN_WPG group (not required for SharePoint 2010 installations, only for SharePoint 2013 and later)
- Site collection administrator on each SharePoint site collection being monitored (LOGbinder will set this when the service is started.)
- Privilege “log on as a service” (The installer will set this prerequisite.)
- Permission to create, read, modify files in C:\ProgramData\LOGbinder SP (The installer will set this prerequisite.)
- Please note that the ProgramData folder is a hidden folder, and it is not the same as the Program Files folder.
- This LOGbinder SP folder will be created after LOGbinder is installed and the LOGbinder control panel is first started.
- Note: LOGbinder for SharePoint uses the standard SharePoint API to access audit information. (See article LOGbinder SP use of SQL Privileges.) However, in some rare occasions, SharePoint requires more authority than is normally necessary. In these unusual cases, the user account as well as the service account needs additional privileges to the SharePoint databases. For further details on why, what, and how, see the article on Workaround if LOGbinder SP is having SQL database issues.
If outputting to Windows Security log
- Privilege "Generate Security Audit" (SeAuditPrivilege)
- Setting audit policy
- Windows 2003:
- Enable “Audit object access”
- Windows 2008 or later:
- Enable “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings” security option
- Enable “Audit Application Generated” audit subcategory
- Windows 2003:
Step 3 – Run the Installer
Download and run the installation package:
- For SharePoint 2013 and above, run the 2013 installer.
- For SharePoint 2010, run the 2010 installer.
On the page "Specify User Account," enter the username, domain and password of the service account (the user account that will run the LOGbinder for SharePoint (LOGbinder SP) service). The rights outlined above must be granted to the account before running the installer, or else LOGbinder for SharePoint will not install properly.
On the page "Select Installation Folder," it is recommended that you use the default setting, “C:\Program Files\LOGbndSP”.
If a dialog box "Set Service Login" appears, then the user account information entered previously was not valid. Confirm the account name and password, and re-enter the information.
Transferring settings to a new server
If LOGbinder was running in your environment before, but it now has to be installed on a different server, the following steps can be followed to transfer the settings to the new server. (Please note that LOGbinder is not recommended to be run on two servers at the same time in the same environment.) This not only saves setup time and reduces setup problems, but this will ensure audit log collection to be continued where LOGbinder left off so as to preserve a complete audit trail:
- Make sure that on both the source (where LOGbinder was run before) and target (the new LOGbinder server) servers, the LOGbinder service is not running and the LOGbinder control panel is not open.
- Go to the C:\ProgramData\LOGbinder SP folder on the source server.
- Please note that the ProgramData folder is a hidden folder, and it is not the same as the Program Files folder.
- Copy all *.stg and *.xml files to the same folder on the target server.
2.2. Configuring LOGbinder for SharePoint
Configuring LOGbinder for SharePoint
Open the "LOGbinder for SharePoint" link in the Windows start menu, which appears by default in the “LOGbinder” folder.
To use LOGbinder for SharePoint, adjust the settings in the three views: Input, Output, and Service. Settings can be changed while the service is running, but changes will be applied only when the service is restarted. If the LOGbinder for SharePoint control panel is closed before restarting the service, the changes will be discarded. On the other hand, if the service is already stopped, the changes are saved automatically.
Configure Input
LOGbinder for SharePoint examines the local SharePoint server farm; the site collections that exist on the farm are shown in the view. Only the sites with a check mark in the Monitored column will be processed by LOGbinder.
| What do I do if the site collection list is empty? If the site collection list is empty (that is, apart from the <Default Audit Policy> entry), you are not properly connected to a SharePoint farm. It may be that (1) LOGbinder for SharePoint is not installed on a valid SharePoint server, (2) your account is not a SharePoint Farm Administrator, or (3) your account needs to run with elevated privileges (i.e. run as administrator) in order to access the farm. |
The first item listed is <Default Audit Policy>. LOGbinder for SharePoint allows you to set a default audit policy, which can then be applied to site collections you specify. If you later change the default audit policy, the site collections to which you have applied it will automatically have their policy changed.
To adjust the default audit policy, select that item in the list, and use the menu Action\Properties (or double-click on it). Select one or more event types to be monitored. If you wish to apply the default policy to newly created site collections, check the box “Apply default audit policy to new site collections.”
Figure 1: A typical Input list
To adjust the properties of a site collection, use the menu Action\Properties or double-click on it. To adjust the audit policy of multiple site collections at once, use the Shift+Click, CTRL-A, or mouse scrolling while selecting.
For site collections you wish to monitor, you have three ways to specify the audit policy:
- “Allow Site Collection Administrator to configure audit policy using SharePoint’s administration page”: This allows you to set the audit policy in SharePoint. To see what the current audit policy is for the site collection, click the “View” link, and a list of the current policy will be shown. (See Appendix D: Configuring auditing on a SharePoint list or document library)
- “Use LOGbinder’s default audit policy”: To view the default audit policy, you may click the “View” link. If this option is disabled, it means that you have not yet set the default audit policy.
- “Custom audit policy”: If this option is selected, then select one or more event types to be audited in the box. At least one audit type must be selected in order for the site collection to be processed by LOGbinder.
Figure 2: Input properties window
The "Last Processed" box shows the date and time audit events were last retrieved from SharePoint. After installing LOGbinder the first time, it starts processing audit logs from the time of the installation onward.* If some of the backlog events are also to be processed, the start date can be set here. It is recommended that once LOGbinder is in operation, this date not be changed manually, as it could result in skipping some audit events in SharePoint, or double-handling, resulting in events appearing twice in the event log. If the date needs to be adjusted, check the box next to the date, and then the date can be adjusted.
This window also has a link to SharePoint Farm Properties, which displays basic information about the SharePoint farm.
* If this is not the first installation of LOGbinder on the same server, it will continue audit log processing from the date and time it finished its last run with the previous installation. If LOGbinder was installed on another server in the same environment before, you might want to refer to the section here about Transferring settings to a new server.
Configure Output
LOGbinder supports multiple output formats. LOGbinder for SharePoint allows output to go to
- LOGbinder SP Event Log: a custom event log under Applications and Services Logs.
- Security Log: the Windows Security log. (Please remember to set the additional privileges as described in section Step 2 – Check User Accounts and Authority when using this feature.)
- Syslog-CEF: a Syslog server using ArcSight’s Common Event Format.
- Syslog-LEEF: a Syslog server using IBM Security QRadar’s Log Event Extended Format.
- Syslog-Generic: a Syslog server using the generic Syslog format.
- Syslog-CEF (File): a Syslog file using ArcSight’s Common Event Format.
- Syslog-LEEF (File): a Syslog file using IBM Security QRadar’s Log Event Extended Format.
- Syslog-Generic (File): a Syslog file using the generic Syslog format.
At least one of these must be enabled in order for the LOGbinder service to start.
To enable an output and adjust the settings, select it and use the menu Action\Properties, or double-click on the item. To enable it, check the box "Send output to [name of output format]."
Select the "Include noise events" if you want to include these in the event log. A “noise event” is a log entry generated from the input (SharePoint) that contains only misleading information. This option is included in case it is essential to preserve a complete audit trail; by default this option is not selected.
Figure 3: Output properties window
For some output formats, LOGbinder for SharePoint can preserve the original data extracted from SharePoint, along with details as to how the entry was translated by LOGbinder. Check the option “Include XML data” in order to include these details in the event log. Including this data will make the size of the log grow more quickly. If the option does not appear, then it is not supported for that output format.
For the output format "LOGbinder SP Event Log," the entries are placed in a custom log named “LOGbinder SP.” When the log is created by LOGbinder, by default the maximum log size is set to 16MB, and it will overwrite events as needed. If changing these settings, balance the log size settings with the needs of your log management software as well as the setting for “Include XML Data.” In this way you will ensure that your audit trail is complete.
For file based outputs, such as Syslog (File), the output file is stored, by default, in the "C:\ProgramData\LOGbinder SP" folder, or in the folder specified by the “Alternate Output Data Folder” option under File\Options. (See section below on Configure Options.)
Configure Service
To start, stop, and restart the LOGbinder for SharePoint (LOGbinder SP) service, use the buttons on this panel. You may also use the items in the Action menu, or the toolbar.
Figure 4: Message indicating outputs not configured
Although you can use the Services window in the Windows Control Panel to start and stop the service, it is recommended that you use LOGbinder's user interface to control the service. Before starting the service, LOGbinder will confirm that (a) at least one site collection has been selected for monitoring and (b) at least one output (i.e. LOGbinder SP Event Log, Windows Security Log) has been selected.
While attempting to start the LOGbinder for SharePoint (LOGbinder SP) service, a problem may be encountered—perhaps that the service account does not have sufficient authority. The details of the problem are written to the Application Event Log. These events can also be viewed inside of the LOGbinder control panel, by selecting the “LOGbinder Diagnostic Events” view.
See the section “Monitoring LOGbinder for SharePoint” for more information on how to handle issues that may arise when starting the LOGbinder for SharePoint (LOGbinder SP) service.
Configure Options
Use buttons on the panel, or the menu File\Options, to change LOGbinder's options.
LOGbinder for SharePoint allows the control of how much lookups it should perform in order to obtain additional information while translating raw audit event to easy-to-understand audit entries. Examples of this could be resolving a user ID to user name or an object GUID to the actual name of the object. The available levels of lookups are as follows:
- Exclude none: All lookups will be done. This may result in slower processing for larger farms.
- Exclude highest-cost lookups: All lookups will be done except lookups that use the highest amount of resources. It can affect all events, where details for any main item, where it is an item in a list, will not be looked up. Details such as ‘Title’ and ‘Description’ will not have values.
- Exclude high-cost lookups: Do not do lookups that use a high amount of resources. (Recommended setting for large farms.) It can affect all events, where details for any main item will not be looked up. Details such as ‘Title’ and ‘Description’ will not have values.
- Exclude high/medium-cost lookups: Do not do lookups that use high or medium amount of resources. It will affect events 16, 29, 31, 32, where details of related items will not be looked up. The event will be included in the audit trail, but much of the detail will be missing for these events
- Restrict all: Do not do any lookups. IDs will be resolved that do not require querying SharePoint. (Not recommended.) It will affect all events, where user, group, and role IDs are not resolved.
Figure 5: Options windows
The levels are inclusive, that is, if you choose ‘high’, it includes ‘highest’. If you choose ‘medium’ it includes ‘highest’, and ‘high’.
Please note that when lowering the lookup level, some details in certain events will be omitted. Therefore, we recommend that depending on the acceptable performance, the highest possible level is selected. Recommendations:
- If site collections are not being processed in a timely manner, choosing ‘highest’ or ‘high’ is a good option. The details that are excluded do not significantly affect the integrity of the audit trail.
- If site collections are still not being processed in a timely way, and there are a significant number of the events that are listed above, then dropping to ‘medium’ is suggested.
- For very large sites, and where close to real-time processing is needed, choose ‘restrict all’. The events will appear closer to the “raw” format they appear in SharePoint.
If the box “Purge entries from SharePoint after processing” is checked, then audit entries will be purged automatically from SharePoint on a daily basis at 1:00 AM. A buffer is maintained, in that only entries older than 24 hours are purged. (For example, when entries are purged on 11/16/2009 1:00 AM, it purges entries older than 11/15/2009 1:00 AM.) If this option is checked, then SharePoint’s audit log trimming feature will be disabled automatically.
If the box "Trim claims encoding from user name" is checked, LOGbinder will trim the claims encoding characters from the username before sending the log data to the output. For example, instead of "i:0#.w"|test\jsmith" displayed it will display "test\jsmith".
The “Service Account” lists the user account that runs the LOGbinder for SharePoint (LOGbinder SP) service. This is the account you specified when installing LOGbinder for SharePoint. If it is necessary to change the account, use the Services management tool (in Windows Administrative Tools).
If the box “Do not write informational messages to the Application log” is checked, then event “551 – LOGbinder agent successful” (see Appendix C: Diagnostic Events) will not be written to the Application log.
The “Logging” options can be utilized for diagnostic purposes if experiencing problems with LOGbinder. By default, the “Logging Level” is set to None. If necessary, the Logging Level can be set to Level 1 or Level 2. Level 1 generates standard level of detail of logging. Level 2 will generate more detailed logging. Level 2 should be selected only if specifically requested by LOGbinder support; otherwise performance will be adversely affected. Both Level 1 and Level 2 logging options will generate log files named Control Panel.log, Service.log, Service Controller.log and Service Processor.log in the Log location folder.
“Alternate Output Data Folder” specifies the data folder used for the output data. This is the folder where LOGbinder stores output that are written in files, such as the Syslog-Generic (File), as well as the above mentioned diagnostic files. The folder path can be set using drive letter or UNC, if it is a network location. The default folder is {Common Application Data}\LOGbinder SP (i.e. C:\ProgramData\LOGbinder SP). Please note that the Alternate Output Data Folder needs the same permissions as the Common Application Data folder as specified above in section Step 2 – Check User Accounts and Authority.
"Memory Threshold" specifies how much memory LOGbinder can use before restarting the service. This can be useful due to memory leaks in the .NET Framework.
Status Bar
The status bar will show information about the operation of LOGbinder.
| Displays the status of the service. The image shown indicates the service is stopped ( |
|
| Shows the status of the license for LOGbinder. If LOGbinder is not fully licensed, a message will appear in the status bar. | |
| Indicates that settings have been changed. In order to apply the changes, the LOGbinder for SharePoint (LOGbinder SP) service must be restarted. If the LOGbinder for SharePoint (LOGbinder SP) service is running and the LOGbinder for SharePoint control panel is closed, the changes will be discarded. |
License
Use the menu File\License to view information about your license for LOGbinder. If you have purchased LOGbinder for SharePoint and need to obtain a license, follow these steps:
- For Unit/Server Count, in case you are planning expansion of your farm in the near future, you can enter more than the number of servers in the farm that need licensed. (The minimum number of servers requiring licensing will be filled out automatically by LOGbinder. See box below for further details.)
- Press the Copy button, and paste the contents into a support ticket.
- When the license key is received, copy it to the clipboard and press the Paste button.
Figure 6: License window
If you are properly licensed, the license window will re-display and show that you are properly licensed. If there is problem, respond to your license request ticket immediately.
| When purchasing LOGbinder for SharePoint, confirm that you obtain a license sufficient for the SharePoint farm. The window “SharePoint Farm Properties” lists the information you need. You can find a link to this window in Options, or in any of the Input windows.
Particularly, you will need (a) the edition of SharePoint on your server farm, and (b) the number of servers requiring a LOGbinder license. Figure 7: SharePoint Farm Properties window |
The license key you receive is valid for any server in your SharePoint farm. Thus, if you need to install LOGbinder for SharePoint on a different server in the same farm, you do not need to request a new license key.
2.3. Monitoring LOGbinder for SharePoint
When installing, configuring, and running LOGbinder for SharePoint, the software writes diagnostic events to the Windows Application Event Log. Most of these will be from the source "LOGbndSE" and the category "LOGbinder." You may use the Windows Event Viewer to examine these events.
During Installation and Configuration
During installation and configuration, you will find these entries:
- After installation, there may be an entry from the source MsiInstaller: "Product: LOGbinder SP -- Installation completed successfully."
- When the configuration of LOGbinder for SharePoint changes, you will see one or more entries entitled "LOGbinder settings changed." See Appendix C: Diagnostic Events: “553 – LOGbinder settings changed” for information about these events.
- When the service starts, there may be an entry from the source LOGbinder SP: "Service started successfully." (Entries are also written when the service is stopped.)
You can monitor these events to ensure that LOGbinder for SharePoint continues to be configured properly, and that unauthorized changes do not occur.
After configuring LOGbinder for SharePoint and starting the service, it automatically performs a check to ensure that LOGbinder's settings are valid and that the account running the Windows service has sufficient authority. If there is a problem, the LOGbinder for SharePoint (LOGbinder SP) service will not start and a message will be presented to the user. In most cases, the details of the problem are written to the Application log. Common problems include:
- Input/output not configured properly. See the previous section “Configuring LOGbinder for SharePoint” for more information.
- Insufficient authority. If the service account does not have adequate authority, then the service will not run. An entry is written to the Application log. See Appendix C: Diagnostic Events “556 – LOGbinder insufficient authority” for more details. Some of the common missing permissions include:
- Account does not have authority to log on as a Windows service
- Account does not have necessary permissions in SharePoint.
- The account does not have authority to write to the Security event log. (If this output destination has not been selected, then it is not necessary to grant this permission.)
- License invalid. If the license is not valid or has expired, then the LOGbinder for SharePoint (LOGbinder SP) service will not run. An entry may be written to the Application log. See Appendix C: Diagnostic Events: “557 – License for LOGbinder invalid” for details.
- Other errors will be found in entries entitled "LOGbinder error." See Appendix C: Diagnostic Events: “555 – LOGbinder error” for more information.
If any of these errors are encountered, the LOGbinder for SharePoint (LOGbinder SP) service will not run.
While LOGbinder for SharePoint is Running
While LOGbinder for SharePoint is running, you will see information entries in the Application log as follows:
- Entries 'exported' from SharePoint. For each site collection being monitored, this message indicates the number of audit entries that LOGbinder for SharePoint has processed.
- Entries 'imported' into the Windows event log. This indicates that the audit entries have been placed in the enabled output formats. There will be one message event if multiple output formats have been selected (i.e. you have selected both Windows Security Log and Windows Event Log as output formats). The 'export'/'import' entries are complementary: there should be a corresponding 'import' entry for each 'export.'
- If the Default Audit Policy is used for newly created site collections, a number of “553 – LOGbinder settings changed” events (see Appendix C: Diagnostic Events) will be generated when configuring a new site collection.
These log entries are informational in nature. Generally no action is required. If more entries are being processed than what appear in the event logs or in your log management solution, it could be that the log size is too small and entries are being overwritten. See Appendix C: Diagnostic Events “551 – LOGbinder agent successful” for more information on these events.
There may also be some warning event entries:
- Could not find information. As LOGbinder for SharePoint translates audit entries in SharePoint, and it cannot find information, this event will be generated. See Appendix C: Diagnostic Events “552 – LOGbinder warning” for more information. (Note: When LOGbinder for SharePoint is first installed, or if a site collection is being monitored for the first time, there is a greater likelihood of these messages. Once LOGbinder for SharePoint translates the backlog of SharePoint audit entries, the number of these warnings should decrease.)
- LOGbinder agent produced unexpected results. When LOGbinder for SharePoint cannot translate an event properly, in addition to outputting the event to the selected output streams, it also creates an entry in the Application log. See Appendix C: Diagnostic Events “554 – LOGbinder agent produced unexpected results” for further details.
If LOGbinder for SharePoint has an error, an entry will be created in the Application log. If permissions are removed, or if the license expires, you may receive a "556 – LOGbinder insufficient authority" or "557 – License for LOGbinder invalid" error, which are explained above. Other errors will be entitled "555 – LOGbinder error." If you cannot resolve the problem, please submit the issue to the LOGbinder support team.
2.4. Appendix A: Assigning Permissions
SharePoint Farm Administrator
- Open SharePoint Central Administration, and select the “Security” tab
- Select “Manage the farm administrators group” under “Users”
- Add user or ensure that user is a member of a group in the list of administrators
Site Collection Administrator
- For SharePoint 2013 and 2016, see http://technet.microsoft.com/en-us/library/ff631156.aspx
WSS_ADMIN_WPG group
On SharePoint 2013, the service account has to be member of the WSS_ADMIN_WPG Windows security group.
- Open the Computer Management administrative tool.
- Under System Tools, expand Local Users and Groups, and select Groups.
- In the properties of WSS_ADMIN_WPG, add the service account.
Local Security Policy Changes
The following chart summarizes the changes to be made in the Local Security Policy. More detailed explanations are found after the chart.
|
Local Security Policy (secpol.msc) settings summary |
Windows Server 2008/2012 |
||||
|
Security Settings |
Local Policies |
User Rights Assignment |
Log on as a service |
add service account |
This always needs to be set |
|
Generate security audits |
add service account |
These need to be set if outputting to Windows Security log |
|||
|
Security Options |
Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings |
set Enabled |
|||
|
Advanced Audit Policy Configuration |
Object Access |
Audit Application Generated |
set Success |
||
Log On as a Service
- Open the "Local Security Policy" (secpol.msc) Microsoft Management Console (MMC) snap-in.
- Select Security Settings\Local Policies\User Rights Assignment
- Open "Log on as a service" and add user
- NOTE: You can also configure this via a group policy object in Active Directory. If you try to modify this setting in Local Security Policy and the dialog is read-only, it means it is already being configured via Group Policy and you'll need to configure it from there.
Generate Security Audits (SeAuditPrivilege)
- Open the "Local Security Policy" (secpol.msc) Microsoft Management Console (MMC) snap-in.
- Select Security Settings\Local Policies\User Rights Assignment
- Open "Generate security audits" and add user
NOTE: You can also configure this via a group policy object in Active Directory. If you try to modify this setting in Local Security Policy and the dialog is read-only, it means it is already being configured via Group Policy and you'll need to configure it from there.
Audit Policy
Windows Server 2008/2012
Audit policy can be configured with the original top level categories as described above for Windows 2003 but most environments have migrated to the new more granular audit sub-categories available in Windows 2008 aka (Advanced Audit Policy).
Using Advanced Audit Policy Configuration allows for more granular control of the number and types of events that are audited on the server. (NOTE: The steps described here are for Windows Server 2008 R2; see TechNet for information on earlier releases.)
- You must ensure that ‘basic’ and ‘advanced’ audit policy settings are not used at the same time.
- Microsoft gives this warning: “Using both the basic audit policy settings under Local Policies\Audit Policy and the advanced settings under Advanced Audit Policy Configuration can cause unexpected results. Therefore, the two sets of audit policy settings should not be combined. If you use Advanced Audit Policy Configuration settings, you should enable the Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings policy setting under Local Policies\Security Options. This will prevent conflicts between similar settings by forcing basic security auditing to be ignored.” (http://technet.microsoft.com/en-us/library/dd692792(WS.10).aspx)
- Select Security Settings\Local Policies\Security Options
- Open and enable “Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings”
- Microsoft gives this warning: “Using both the basic audit policy settings under Local Policies\Audit Policy and the advanced settings under Advanced Audit Policy Configuration can cause unexpected results. Therefore, the two sets of audit policy settings should not be combined. If you use Advanced Audit Policy Configuration settings, you should enable the Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings policy setting under Local Policies\Security Options. This will prevent conflicts between similar settings by forcing basic security auditing to be ignored.” (http://technet.microsoft.com/en-us/library/dd692792(WS.10).aspx)
- To enable LOGbinder for SharePoint events to be sent to the security log:
- Select Security Settings\Advanced Audit Policy Configuration\Object Access
- Edit “Audit Application Generated,” ensuring that “Success” is enabled. (LOGbinder for SharePoint does not require that the “Failure” option be enabled.)
NOTE: You can also configure this via a group policy object in Active Directory.
2.5. Appendix B: LOGbinder Event List
LOGbinder for SharePoint Events
http://www.logbinder.com/Products/LOGbinderSP/EventsGenerated
Diagnostic Events
550 – LOGbinder process report
551 – LOGbinder agent successful
552 – LOGbinder warning
553 – LOGbinder settings changed
554 – LOGbinder agent produced unexpected results
555 – LOGbinder error
556 – LOGbinder insufficient authority
557 – License for LOGbinder invalid
2.6. Appendix C: Diagnostic Events
550 – LOGbinder process report
Each time all the site collections have been processed, LOGbinder for SharePoint will write this event to the Application event log. It lists the number of site collections processed, the start and end time, and the time elapsed.
Example
LOGbinder process report
The LOGbinder agent has completed a round of processing.
Agent: LOGbinder SP
Processed: 24 SharePoint Site Collections
Start time: 8/13/2013 4:02:03 PM
End time: 8/13/2013 4:05:07 PM
Duration (minutes): 3
551 – LOGbinder agent successful
Occurs when LOGbinder for SharePoint successfully translates log entries. Usually appearing in pairs, as one indicates that log entries have been 'exported' from their source (for example, SharePoint), and the other that entries have been 'imported' to their destination (for example, the Windows event log). This event is informational in nature.
This event is written to the Windows Application log.
Example A
LOGbinder SP exported 3 entries from SharePoint site http://MySite
Example B
LOGbinder SP imported 3 entries to Security event log
Example C
LOGbinder SP imported 3 entries to LOGbinder SP event log
552 – LOGbinder warning
Occurs when LOGbinder for SharePoint does not find information as expected. In most cases, it does not indicate a serious problem, but is provided so as to complete the audit trail. This event is written to Windows application log.
For example, as LOGbinder for SharePoint translates entries, it performs various lookups to provide complete information. If the related item was deleted, a "LOGbinder warning" is generated.
Example A
LOGbinder warning
Lookup failed. Could not find Scope Item with ID of 89de71fe-1442-48ff-9a6e-052bddda3440.
Example B
LOGbinder warning
Lookup failed. Could not find User with ID of 19.
553 – LOGbinder settings changed
Occurs when the LOGbinder settings are changed. This event is written to Windows Application log.
For LOGbinder for SharePoint, this includes which SharePoint site collections are monitored, which audit event types are handled, and the date and time LOGbinder last translated log entries. In addition, the settings for output formats are included.
Example A
LOGbinder settings changed
Output to Security log enabled. Noise events included.
Example B
LOGbinder settings changed
Site collection http://spsite/administrator now being monitored.
Settings: Check Out, Check In, Delete, Update, Profile Change, Child Delete, Schema Change, Security Change, Undelete, Workflow, Copy, Move, Search.
Example C
LOGbinder settings changed
Purge of entries from SharePoint Site Collections has been enabled.
554 – LOGbinder agent produced unexpected results
Occurs when LOGbinder for SharePoint encounters something unexpected when translating a log entry. At times it may be from a custom log entry.
Microsoft has not documented all the audit log entries SharePoint produces. In addition, SharePoint allows developers to write their own custom log entries.
This event is written to Windows Application log.
You can help us improve LOGbinder by reporting these events to the LOGbinder support team so that the LOGbinder product may be improved. Private data will not be shared.
Example A
In this example, the developer created an audit entry with the type "MakeItSo."
LOGbinder agent produced unexpected results
As the LOGbinder agent translated this entry, it encountered data is could not handle properly. It could have been caused by a custom or undocumented feature. So that LOGbinder can handle these entries in the future, it is suggested that you submit the entry to the LOGbinder support team
<LogEntry siteName="http://shpnt" itemType="Site" userName="Robert Solomon" locationType="Url" occurred="2009-06-26T14:13:02" eventType="MakeItSo"><RawData siteId="3b7fb82c-f30d-4604-99c0-df8325e9cff4" itemId="3b7fb82c-f30d-4604-99c0-df8325e9cff4" itemType="Site" userId="1" locationType="Url" occurred="633816223820000000" event="Custom" eventName="MakeItSo" eventSource="ObjectModel"><EventData><Version><Major>1</Major><Minor>2</Minor></Version></EventData></RawData><Details /></LogEntry>
Example B
In this example, the developer used an existing event type, "Workflow," but included non-standard event data.
LOGbinder agent produced unexpected results
As the LOGbinder agent translated this entry, it encountered data is could not handle properly. It could have been caused by a custom or undocumented feature. So that LOGbinder can handle these entries in the future, it is suggested that you submit the entry to the LOGbinder support team.
<LogEntry siteName="http://shpnt" itemType="List Item" userName="Robert Solomon" locationType="Url" occurred="2009-06-29T21:49:11" eventType="Workflow"><RawData siteId="3b7fb82c-f30d-4604-99c0-df8325e9cff4" itemId="c04f5388-bf24-4007-b463-1dd1b3c19a02" itemType="ListItem" userId="1" documentLocation="Cache Profiles/1_.000" locationType="Url" occurred="633819089510000000" event="Workflow" eventSource="ObjectModel"><EventData>http://shpnt/docLib/CopiedFile.ext</EventData></RawData><Details /></LogEntry>
555 – LOGbinder error
Occurs when LOGbinder encounters a problem that needs attention. This event is written to Windows Application log. In most cases this gives enough information for you to address the problem successfully. Otherwise, please contact LOGbinder support for assistance.
Example A
In this example, the error indicates that LOGbinder for SharePoint has not been configured properly: in that no SharePoint site collections were set to be monitored by LOGbinder.
LOGbinder error
Cannot start LOGbinder SP service, SharePoint Site Collections not configured.
Example B
In this example, a program assembly used by SharePoint SP does not exist, indicating that the LOGbinder software is no longer installed properly.
LOGbinder error
Exporter assembly does not exist: C:\Program Files\LOGbndSP\MTG.LOGbinder.Sharepoint.dll
556 – LOGbinder insufficient authority
Occurs when the LOGbinder for SharePoint service cannot run because of invalid or inadequate permissions. The event will include the module lacking the permission, the name or description of the permission, as well as relevant details. Each example below also includes the action needed in order to correct it.
Example A: No permission to write to security log
LOGbinder insufficient authority
The LOGbinder agent cannot operate normally because it lacks sufficient authority.
Source: Security Log
Privilege: SeAuditPrivilege
Details: The LOGbinder agent does not have the necessary rights to configure the security log
Action: The service account needs the "Generate security audits" privilege (https://www.ultimatewindowssecurity.com/wiki/WindowsSecuritySettings/Generate-security-audits), or do not enable LOGbinder to output to the Windows Security log.
Example B: Attempt to write to security log from invalid location
One measure to protect the security log is to write security events only from authorized locations. When LOGbinder is configured, it registers its program location with the security log. If this error occurs, then LOGbinder had been reinstalled to a different location, and the previous location was not removed properly.
LOGbinder insufficient authority
The LOGbinder agent cannot operate normally because it lacks sufficient authority.
Source: Security Log
Privilege: Invalid Location
Details: Cannot write to because the program location does not match what has been previously configured
Action: Recommended to delete the registry key manually. First ensure that LOGbinder is not open. Then delete the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog\Security\LOGbndSC. Be careful not to delete other parts of the registry, as it can cause the server to be unstable. When you reopen LOGbinder, it will reconfigure its ability to write to the security log.
Example C: Internal error
LOGbinder insufficient authority
The LOGbinder agent cannot operate normally because it lacks sufficient authority.
Source: Security Log
Privilege: Internal Error
Details: The security account database contains an internal inconsistency
Action: One factor that can cause an internal error is if the LOGbinder program path is too long. By default, LOGbinder is installed to C:\Program Files\LOGbndSP. It is recommended that the default be used. If the software has been installed to a different location with a longer program path, to correct this error it will be necessary to reinstall LOGbinder.
Example D: Log on as service
LOGbinder insufficient authority
The LOGbinder agent cannot operate normally because it lacks sufficient authority.
Source: LOGbinder service
Privilege: Log on as service
Details: Account running LOGbinder agent does not have user right "Logon as a service"
Action: The service account needs to be assigned the "Logon as a service" user right. (https://www.ultimatewindowssecurity.com/wiki/WindowsSecuritySettings/Log-on-as-a-service)
Example E: Cannot start LOGbinder control panel
LOGbinder insufficient authority
The LOGbinder agent cannot operate normally because it lacks sufficient authority.
Source: LOGbinder Manager
Privilege: File Permissions
Details: Account running LOGbinder Control Panel needs to be a member of the local Administrators group
Action: Ensure that the user account used to run the LOGbinder for SharePoint control panel has local administrator access.
557 – License for LOGbinder invalid
Occurs when the license for LOGbinder is not valid and an attempt is made to start the service. This event is written to the Application log.
If the license is not valid, the LOGbinder for SharePoint control panel continues to operate as normal. However, the LOGbinder service will not start if the license is invalid. Follow the instructions in the control panel, in the menu File\License, in order to obtain a license to the software.
Example
License for LOGbinder invalid
The license for LOGbinder has expired or is invalid.
Details: Trial period has expired.
558 –LOGbinder processing warning
This warning message will be written to the Application log if any site collections have been behind in its processing for more than 24 consecutive hours.
2.7. Appendix D: Configuring auditing on a SharePoint list or document library
When configuring the inputs for LOGbinder, LOGbinder will adjust the audit settings for the SharePoint site collection. At times, though, it is necessary to have more granular control on the settings. For example, a SharePoint document library may have confidential information, and it is desired to audit who is viewing these documents. Auditing view access for the entire site collection would result in a flood of audit entries that are not needed. The solution is to adjust the auditing of SharePoint lists and document libraries. To do this:
- In the LOGbinder control panel, set the audit policy you want enabled across the entire site collection.
- To change the audit policy for a certain document library or list, go to its settings page and click the link “Information management policy settings” under “Permissions and Management.”
- Select a content type (if applicable), and go to the “Auditing” section and configure the audit policy.
- Save your changes, and SharePoint will begin auditing that list/library according to the settings you specify. LOGbinder for SharePoint will include these audit events when it processes the site collection.
For more information, see blog How to Audit an Individual Library or List in SharePoint.
3. How To
3.1. How does LOGbinder for SharePoint detect log tampering?
While LOGbinder for SharePoint is processing events, it will perform actions that generate SharePoint events. What happens, though, if these same actions are performed maliciously by a SharePoint user? Will this compromise the integrity of the audit trail? No. LOGbinder for SharePoint can detect log tampering. How?
In order to distinguish between authorized and unauthorized changes, LOGbinder for SharePoint (version 3 and later), when processing these events, will indicate whether it performed the action itself, or the action might be unauthorized. A tamper warning will be generated in the following cases:
· Audit policy change: When processing event #11 “Site collection audit policy changed” or #12 “Audit policy changed,” LOGbinder will determine if the change overrides the settings in LOGbinder. If so, LOGbinder will reset the audit policy and generate a tamper warning (#60 “Possible tampering warning”).
· Audit logs deleted: When processing event #20 “SharePoint audit logs deleted,” LOGbinder will determine whether LOGbinder deleted the logs, and indicate it in an additional line added to this event. The line “Purge performed by LOGbinder” will show value “Yes” if LOGbinder performed the purge, and “No” otherwise. In the latter case, a tamper warning event (#60 “Possible tampering warning”) will be generated.
Note: If it cannot determined whether the logs were deleted by LOGbinder for SharePoint, the “Purge performed by LOGbinder” value will be set to “Indeterminate”. This typically occurs when processing backlog events, i.e. those produced before LOGbinder started processing the site collection.
By alerting on event #60 “Possible tampering warning”, malicious audit tampering attempts can be detected, so the audit trail is not compromised.
3.2. How to reduce the number of audit events
Enabling certain audit flags, such as the View audit flag, can result in a massive amount of audit events in a SharePoint farm. However, it might be necessary to monitor View events at least for parts of the farm. Here are two possible solutions:
- LOGbinder for SharePoint enables specifying different audit policy for each site collection. So, turn on the View audit flag only for the site collections where it is necessary.
- If it is still not granular enough, it is possible to turn on View audit flag for only specific libraries or lists. To achieve this, turn off the View flag for all site collections in LOGbinder, and then enable it only on certain libraries or site collections in SharePoint by following the instructions in the article How to Audit an Individual Library or List in SharePoint.
3.3. Why are User ID's prefixed with "i:0#.w" in LOGbinder for SharePoint?
In October 2014 a customer reported that LOGbinder for SharePoint was prefixing some usernames with what appeared to be a random string of characters. For example, instead of "test\jsmith" you may see "i:0#.w"|test\jsmith". Why is this happening and what does it mean? First of all, it's important to remember that LOGbinder is not creating this information. The User ID field comes directly from SharePoint. Secondly, these are not just random characters. This is actually the method SharePoint uses to identify the claim type being used. You can decode the claim type be reported using this Microsoft TechNet article. Occasionally, you may not see characters used as specified in the TechNet article. This is mostly because you are using a custom claims provider. For unidentified custom claims providers SharePoint will create a claim type starting with the value 500 and will increase in increments of 1 for each unidentified claims provider that is found. You can read more details about that in an article here.
Starting from version 6, LOGbinder now has the option to remove (trim) claims encoding from the user names.
3.4. LOGbinder SP use of SQL Privileges
Issue
In the blog on www.logbinder.com (Workaround if LOGbinder SP is having SQL database issues), a suggested workaround for insufficient privileges to SharePoint’s SQL databases is to add the LOGbinder service account as a database administrator (DBO). We recently published a a new blog (Least Privilege Workaround for SQL DB Access) that explains that dbo is no longer needed as there is a different role, SPDataAccess, that can be used. The question arises: How does LOGbinder for SharePoint use these privileges?
Access to SharePoint databases
First, it must be understood that LOGbinder for SharePoint does not access SharePoint’s SQL databases directly. All access to SharePoint data is through the SharePoint Server Object Model (see http://msdn.microsoft.com/en-us/library/jj164060.aspx). LOGbinder for SharePoint does not execute any Transact-SQL commands directly, nor does LOGbinder for SharePoint access the SQL database directly to adjust database structure, privileges, and so forth.
The workaround suggested in the above blog is recommended based on troubleshooting in our labs, to address what apparently is a defect in the SharePoint Server Object Model. LOGbinder for SharePoint does not then use elevated privileges to perform other activity.
LOGbinder for SharePoint’s use of SharePoint data
Even though LOGbinder for SharePoint accesses SharePoint through its object model, a secondary question may be: What activity does LOGbinder for SharePoint perform in SharePoint? LOGbinder for SharePoint’s main activity is to read SharePoint audit logs, as well as to read metadata about SharePoint site collection, lists, libraries, users, groups, and similar entities.
Through the SharePoint Server Object Model, LOGbinder for SharePoint does make some changes to SharePoint (the customer specifies these changes in the LOGbinder Control Panel). The changes LOGbinder for SharePoint will make to SharePoint include: adding/removing site collection administrators, adjusting audit policy settings for a site collection, adjusting the audit log trimming setting for a site collection, and deleting audit log records. (The documentation for LOGbinder for SharePoint contains details on these actions.) So, other than purging old log data and setting audit policy according to configuration settings by the administrator, there is nothing that LOGbinder does that modifies or could corrupt SharePoint content or the SQL database.
3.5. Workaround if LOGbinder for SharePoint is having SQL database issues
A problem that might occur when using LOGbinder for SharePoint stems from the fact that SharePoint does not behave the same way through its web interface as through its API.
As a result, even though the account has been added correctly via Central Administration or the SharePoint site collection settings page, and has no problem when using the account in the SharePoint web interfaces, the privileges granted are not sufficient when third-party software uses the public SharePoint APIs, resulting in an ‘access denied’ error.
SYMPTOMS:
Even though the LOGbinder user is definitely a farm administrator, you get an event from LOGbinder like this:
Unable to configure SharePoint export. Details: Cannot open database "WSS_Content" requested by the login. The login failed. Login failed for user 'SHAREPOINTSERVER\logbinderaccount'. SQL Database 'WSS_Content' on SQL Server instance 'SHAREPOINTSERVER\OfficeServers' not found. Additional error information from SQL Server is included below. Cannot open database "WSS_Content" requested by the login. The login failed. Login failed for user 'SHAREPOINTSERVER\logbinderaccount'.
CAUSE:
SharePoint behaves differently when accessing it via its web interface versus accessing it via standard Microsoft SharePoint API’s in third-party software. As a result, it might happen that you are able to perform certain operations through the SharePoint web interface, but when doing the same from a third-party application (such as LOGbinder for SharePoint) that is using only standard, published SharePoint API’s, the same operations performed by the same user do not work.
WORKAROUND:
In the past we have explained how LOGbinder for SharePoint uses SQL privileges. We also informed you about the unfortunate workaround of giving dbo access to certain DB's in SQL in the sporadic cases when the SharePoint API interferes with access to the databases.
This was never a "workaround" that we were really happy with. Giving dbo access is not only like giving the bank the title to your home as collateral for the mortgage but also giving them a letter that says "Stop by anytime you want and while you're here feel free to repaint the walls and help yourself to the scotch in the pantry."
Thankfully, we have found a proper workaround that does not require dbo access. There is a role on the SharePoint SQL DB's named "SPDataAccess". We have found that giving the service account this role grants enough access for LOGbinder for SharePoint to function properly. Again we would like to specify that this is not the standard configuration needed with LOGbinder for SharePoint. This is only used in the rare situations when the SharePoint API is giving issues with DB access. For most of our customers the permissions set within SharePoint itself for the service account is all that is needed.
There are two ways to give the service account this role. One is using the SharePoint Management Shell and the other is directly in SQL (in our example below using SSMS).
Our preferred method is making the changes directly in SQL. We noticed that when using the SP Management Shell an extra role is given. We also noticed that this is not always the case as well. Sometimes the extra role is given and sometimes it is not. Why? We don't know. Maybe it's a hidden Microsoft feature.
If this occurs, you will likely want to perform the following workaround, so please follow these steps:
1. Go to Central Administration and under “System Settings” click on “Manage servers in this farm”.
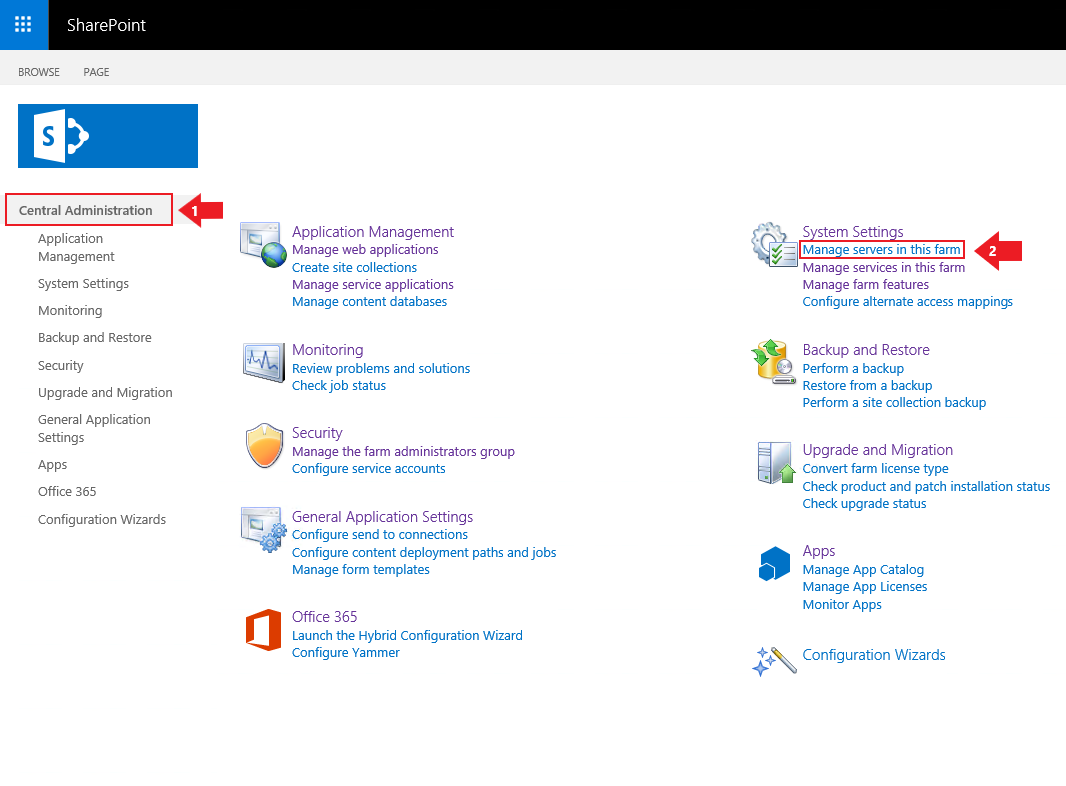
2. Make a note of the “Farm Information” at the top of the page, for example:
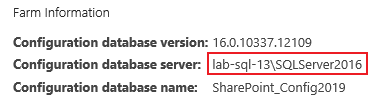
3. Using the server/instance specified above in the Farm Information, open SQL Server Management Studio.
4. In SSMS add your service account as a login.

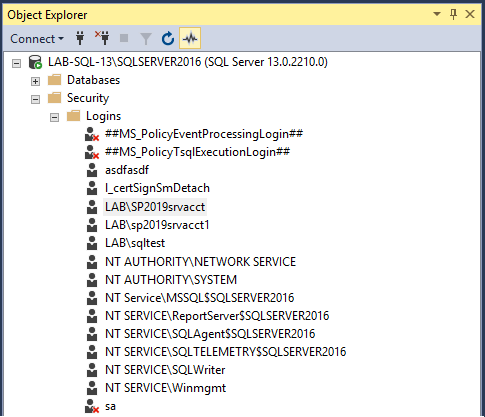
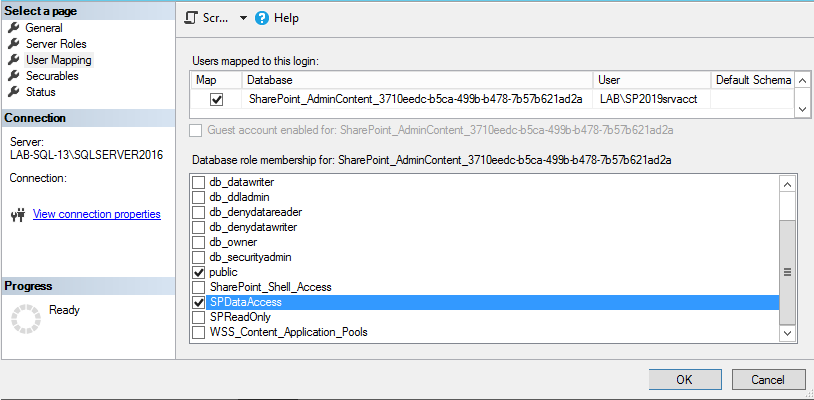
5. Open the logins properties and locate the three databases that you're SharePoint farm is using for the Admin Content, Configuration and WSS Content databases. In this instance we have SharePoint_AdminContent(GUID), SharePoint_Config2019 and WSS_Content(GUID).
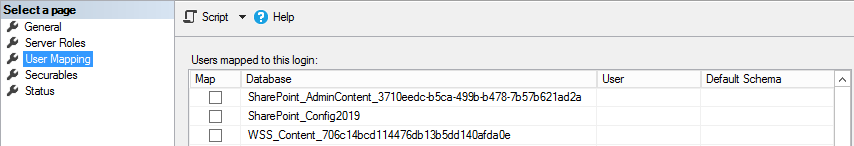
6. For each database map the SPDataAccess role to the login. You will notice that for the WSS_Content db, after saving the role change SSMS also grants the PSDataAccess and the PSReportingSchemaAdmin role. If you have more than one content db, then you will have to perform these steps on all applicable db's with the WSS_Content prefix. For more information on how to set SPDataAccess on a large number of content databases, click here.

You can also perform the steps above with a simple cmdlet using the SharePoint Management Shell. Run the following cmdlet:
Get-SPContentDatabase | Add-SPShellAdmin -UserName domain\ServiceAccount
So in our example below we ran "Get-SPContentDatabase | Add-SPShellAdmin -UserName lab\sp2019srvacct". Notice that doing this grants an additional role on all three databases; the SharePoint_Shell_Access role. As security experts our recommendation is obviously whichever process results in the least privilege needed to get the job done which, in this case, is making the changes via SSMS.
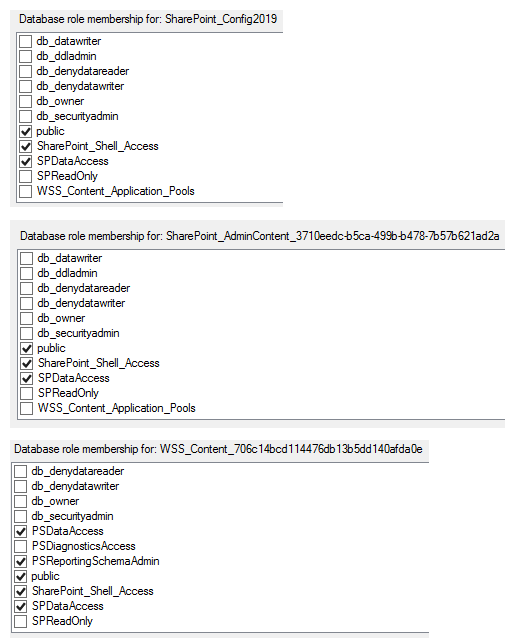
What does the SPDataAccess role allow? According to TechNet, the SP_DATA_ACCESS role will have the following permissions:
- Grant EXECUTE or SELECT on all SharePoint stored procedures and functions
- Grant SELECT on all SharePoint tables
- Grant EXECUTE on User-defined type where schema is dbo
- Grant INSERT on AllUserDataJunctions table
- Grant UPDATE on Sites view
- Grant UPDATE on UserData view
- Grant UPDATE on AllUserData table
- Grant INSERT and DELETE on NameValuePair tables
Grant create table permission
Reference: TechNet
Additional note:
A similar issue may occur with administrator privileges to SharePoint site collections: even though the service account is listed as a site collection administrator in SharePoint’s user interface, you receive an error that the user is not a site collection administrator.
If this occurs, perform similar steps as described above, but to the WSS_Content database. In this case, you would need to add only the LOGbinder SP service account, since the account you use to run the LOGbinder GUI does not need site collection administrator privilege.
It has to be emphasized that we don’t consider the above steps to be a fix, just a workaround to this SharePoint problem, which affects not only LOGbinder, but many other applications too. See, for example this, this, or this article. Even Microsoft says that it can happen and that sometimes “you cannot open a database in the SharePoint Management console of SharePoint Foundation 2010 or SharePoint Server 2010 even though you are a farm administrator who has full administrator rights”, unless you are a member of the db_owner fixed database role for the database. But we have found that the above SPDataAccess role is enough in these situations.
As a security company we strongly advocate the principles of least privilege, which we also apply in the design of our LOGbinder products. There is no reason why the LOGbinder service account should be granted any rights in SQL server. However, until Microsoft fixes this, the only way to get a third-party application work through SharePoint API is to implement the workaround outlined above.
3.6. How To Set SPDataAccess on Large Number of Content Databases
The script below is provided as an example of a script that can be used to add the LOGbinder service account to all databases that have a name starting with 'WSS_Content' as a user and set that user to the SPDataAccess role.
Please change 'LAB\lbspsvc' in the first line to the LOGbinder service account.
DECLARE @username VARCHAR(100) = 'LAB\lbspsvc'
DECLARE @MyCursor CURSOR;
DECLARE @MyField NVARCHAR(128);
DECLARE @sqlstatement VARCHAR(512);
BEGIN
SET @MyCursor = CURSOR FOR
SELECT [name] FROM master.sys.databases WHERE [name] LIKE 'WSS_Content%'
OPEN @MyCursor
FETCH NEXT FROM @MyCursor INTO @MyField
WHILE @@FETCH_STATUS = 0
BEGIN
SET @sqlstatement =
'USE ' + @MyField + '; ' +
'CREATE USER [' + @username + '] FOR LOGIN [' + @username + ']' + '; ' +
'EXEC sp_addrolemember ''SPDataAccess'', ''' + @username + ''''
PRINT @sqlstatement
EXEC (@sqlstatement)
PRINT ''
FETCH NEXT FROM @MyCursor INTO @MyField
END;
CLOSE @MyCursor;
DEALLOCATE @MyCursor;
END;
3.7. Impact of Restricted Lookups
LOGbinder for SharePoint by default makes every effort to fully translate and enrich SharePoint audit events through so called "lookups" where-in LOGbinder makes extra queries to SharePoint to obtain this information. But there is a cost/benefit relationship to be considered. Some events in the native SharePoint audit log include fields that are of low or no value to end users at many organizations. Each field in the native log, including these low or no value fields, requires a lookup by LOGbinder to resolve the native SharePoint data in to user friendly data.
For example, below is a sample of LOGbinder for SharePoint event ID 13:
Document checked in
Occurred: 6/25/2016 1:13:04 PM
Site: http://sp2010-sp
User: Administrator
Object
URL: Shared Documents/FinancialData.xlsx
Title: n/a
Version: 1.0
As you can see in the above event, the “Title” field returned from SharePoint is “n/a”. This is obviously of no value to the end user. Since SharePoint includes these low/no value fields, LOGbinder for SharePoint includes an option to intelligently restrict the number of lookups it processes resulting in increased performance of LOGbinder. You can manage the amount of SharePoint lookups by opening the LOGbinder Control Panel selecting File and then Options. The amount of lookups performed by LOGbinder can be customized by choosing a value under “Amount of SharePoint lookups.” See figure 1 below.
Figure 1: Managing the amount of SharePoint lookups
The fields that are affected (with the exception of the “Restrict all lookups option”) are all child fields of the targeted object. “URL” is the most important field included in the events and that field is always reported except on some permission change events and only if the “Exclude high/medium-cost” option is selected.
Most organizations who need to speed up LOGbinder can safely use the “Exclude high-cost lookups” option without losing significant audit information. Please note that the “Exclude high/medium-cost” option does adversely impact permission change events.
The following chart outlines which fields are affected depending on which option is selected when managing the amount of SharePoint lookups.
|
Field will be blank if this setting is chosen … |
Exclude none |
Exclude highest-cost lookups |
Exclude high-cost lookups |
Exclude high/ medium- cost lookups |
Restrict all lookups |
|
10 Noise entry |
|||||
|
This entry was generated, but contains only data that is misleading or irrelevant. |
|||||
|
Occurred: %1 |
|||||
|
Details: %2 |
|||||
|
11 Site collection audit policy changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
New audit policy: %4 |
|||||
|
12 Audit policy changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
New audit policy: %9 |
|||||
|
13 Document checked in |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Version: %6 |
|||||
|
14 Document checked out |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Version: %6 |
|||||
|
15 Child object deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Parent Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Child Object |
|||||
|
Type: %8 |
|||||
|
URL: %9 |
|||||
|
16 Child object moved |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Parent Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Child Object |
|||||
|
Type: %9 |
✘ |
✘ |
|||
|
Title: %10 |
✘ |
✘ |
|||
|
Original location: %11 |
|||||
|
New location: %12 |
|||||
|
17 Object copied |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Title: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Original location: %7 |
|||||
|
New location: %8 |
|||||
|
18 Custom event |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Details: %4 |
|||||
|
Examine the details accompanying the event for more information. |
|||||
|
19 Object deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Versions deleted: %6 |
|||||
|
Recycled: %7 |
|||||
|
20 SharePoint audit logs deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Logs deleted: %4 |
|||||
|
Last date: %5 |
|||||
|
Audit logs created before this date have been removed from SharePoint. |
|||||
|
Purge performed by LOGbinder: %6 |
|||||
|
21 Object moved |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Title: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Original location: %6 |
|||||
|
New location: %7 |
|||||
|
22 Object profile changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Profile details: %9 |
|||||
|
23 SharePoint object structure changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Details: %9 |
|||||
|
24 Search performed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Search: %4 |
|||||
|
25 SharePoint group created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Group |
|||||
|
ID: %4 |
|||||
|
Name: %5 |
|||||
|
Initial members: %6 |
✘ |
||||
|
26 SharePoint group deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Group |
|||||
|
ID: %4 |
|||||
|
The group name is not available because Microsoft does not report this. Refer to events 25, 27, 28, as these may contain the group name. |
|||||
|
27 SharePoint group member added |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Group |
|||||
|
ID: %4 |
|||||
|
Name: %5 |
✘ |
||||
|
Member |
|||||
|
ID: %6 |
|||||
|
Name: %7 |
✘ 2 |
||||
|
28 SharePoint group member removed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Group |
|||||
|
ID: %4 |
|||||
|
Name: %5 |
✘ |
||||
|
Member |
|||||
|
ID: %6 |
|||||
|
Name: %7 |
✘ 2 |
||||
|
29 Unique permissions created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Parent Object |
|||||
|
Type: %4 |
✘ |
✘ |
|||
|
Subtype: %5 |
✘ |
✘ |
|||
|
URL: %6 |
✘ |
✘ |
|||
|
Title: %7 |
✘ |
✘ |
|||
|
Description: %8 |
✘ |
✘ |
|||
|
Object |
|||||
|
URL: %9 |
|||||
|
This object no longer inherits permissions from the parent. |
|||||
|
30 Unique permissions removed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Parent Object |
|||||
|
Type: %4 |
✘ |
✘ |
|||
|
Subtype: %5 |
✘ |
✘ |
|||
|
URL: %6 |
✘ |
✘ |
|||
|
Title: %7 |
✘ |
✘ |
|||
|
Description: %8 |
✘ |
✘ |
|||
|
Object |
|||||
|
URL: %9 |
|||||
|
This object, which formerly had unique permissions, now inherits permissions from the parent. |
|||||
|
31 Permissions updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
✘ |
✘ |
|||
|
Subtype: %5 |
✘ |
✘ |
|||
|
URL: %6 |
✘ |
✘ |
|||
|
Title: %7 |
✘ |
✘ |
|||
|
Description: %8 |
✘ |
✘ |
|||
|
Target |
|||||
|
Name: %9 |
✘ |
||||
|
Type: %10 |
✘ |
||||
|
Permissions |
|||||
|
Role name: %11 |
✘ |
||||
|
Role description: %12 |
✘ |
||||
|
One instance of this event is logged for each role assigned this user. Look at adjacent events to determine all roles assigned to the user or group. |
|||||
|
32 Permissions removed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
✘ |
✘ |
|||
|
Subtype: %5 |
✘ |
✘ |
|||
|
URL: %6 |
✘ |
✘ |
|||
|
Title: %7 |
✘ |
✘ |
|||
|
Description: %8 |
✘ |
✘ |
|||
|
Target |
|||||
|
Name: %9 |
✘ |
||||
|
Type: %10 |
✘ |
||||
|
Permissions |
|||||
|
Role name: %11 |
✘ |
||||
|
Role description: %12 |
✘ |
||||
|
33 Unique permission levels created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
This object has unique permission levels (role definitions) that are not inherited from its parent. |
|||||
|
34 Permission level created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Permission Level Details |
|||||
|
ID: %8 |
|||||
|
Name: %9 |
|||||
|
Type: %10 |
✘ |
||||
|
Description: %11 |
✘ |
||||
|
Permissions |
|||||
|
List permissions: %12 |
|||||
|
Site permissions: %13 |
|||||
|
Personal permissions: %14 |
|||||
|
35 Permission level deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Permission Level Details |
|||||
|
ID: %8 |
|||||
|
The permission level name is not available because Microsoft does not report this. Refer to events 34 or 36, as these may contain the name. |
|||||
|
36 Permission level modified |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Permission Level Details |
|||||
|
ID: %8 |
|||||
|
Name: %9 |
|||||
|
Type: %10 |
✘ |
||||
|
Description: %11 |
✘ |
||||
|
Permissions |
|||||
|
List permissions: %12 |
|||||
|
Site permissions: %13 |
|||||
|
Personal permissions: %14 |
|||||
|
37 SharePoint site collection administrator added |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Administrator |
|||||
|
ID: %4 |
|||||
|
Name: %5 |
✘ 2 |
||||
|
38 SharePoint site collection administrator removed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Administrator |
|||||
|
ID: %4 |
|||||
|
Name: %5 |
✘ 2 |
||||
|
39 Object restored |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
This object was restored from the Recycle Bin. |
|||||
|
40 Site collection updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
41 Web updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Description: %6 |
✘ |
✘ |
✘ |
||
|
42 Document library updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Description: %6 |
✘ |
✘ |
✘ |
||
|
Library item updated: %7 |
|||||
|
43 Document updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Version: %6 |
|||||
|
44 List updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ |
✘ |
✘ |
||
|
Description: %7 |
✘ |
✘ |
✘ |
||
|
45 List item updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
46 Folder updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Version: %5 |
|||||
|
47 Document viewed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Version: %6 |
|||||
|
48 Document library viewed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ |
✘ |
✘ |
||
|
Description: %6 |
✘ |
✘ |
✘ |
||
|
49 List viewed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
✘ |
✘ |
✘ |
||
|
URL: %5 |
|||||
|
Title: %6 |
✘ |
✘ |
✘ |
||
|
Description: %7 |
✘ |
✘ |
✘ |
||
|
50 Object viewed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
51 Workflow accessed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
The object was accessed as part of a workflow. |
|||||
|
52 Information management policy created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Policy details: %9 |
|||||
|
53 Information management policy changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %8 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Policy details: %9 |
|||||
|
54 Site collection information management policy created |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Policy details: %4 |
|||||
|
55 Site collection information management policy changed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Policy details: %4 |
|||||
|
56 Export of objects started |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
Requested by: %3 |
|||||
|
Look at adjacent events to determine the number of items exported. |
|||||
|
57 Export of objects completed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
Requested by: %3 |
|||||
|
Total number of items: %4 |
|||||
|
Size: %5 |
|||||
|
Look at adjacent events to determine when the export was started. |
|||||
|
58 Import of objects started |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
Requested by: %3 |
|||||
|
Size: %4 |
|||||
|
Look at adjacent events to determine the number of items imported. |
|||||
|
59 Import of objects completed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
Requested by: %3 |
|||||
|
Total number of items: %4 |
|||||
|
Look at adjacent events to determine when the import was started. |
|||||
|
60 Possible tampering warning |
|||||
|
There may have been potential tampering of: %1 |
|||||
|
Details: %2 |
|||||
|
It could indicate tampering, which could affect the integrity of the audit. |
|||||
|
61 Retention policy processed |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
URL: %5 |
|||||
|
Title: %6 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Description: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
Action: %8 |
|||||
|
62 Document fragment updated |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
URL: %4 |
|||||
|
Title: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
63 Content type imported |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Source: %4 |
|||||
|
Proxy: %5 |
|||||
|
Package ID: %6 |
|||||
|
64 Information management policy deleted |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
Object |
|||||
|
Type: %4 |
|||||
|
Subtype: %5 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
URL: %6 |
|||||
|
Title: %7 |
✘ 1 |
✘ |
✘ |
✘ |
|
|
65 Item declared as a record |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
URL: %4 |
|||||
|
66 Item undeclared as a record |
|||||
|
Occurred: %1 |
|||||
|
Site: %2 |
|||||
|
User: %3 |
✘ |
||||
|
URL: %4 |
1 This lookup is not done only when the target object is a list item. If the target item is a document, folder, list, or library, the lookup is performed.
2 Applies to SharePoint 2007 only. In later versions this data is included in the event data without requiring a lookup.
3.8. Can't connect to SQL database WSS_Content?
From time to time, customers receive the following error in conjunction with LOGbinder, we've even had it in our lab environment. We are trying to get to the bottom of the issue, and we need your help--even if you haven't had the problem yourself.
"Unable to configure SharePoint export. Details: Cannot open database "WSS_Content" requested by the login. The login failed. Login failed for user 'SHAREPOINTSERVER\logbinderaccount'. SQL Database 'WSS_Content' on SQL Server instance 'SHAREPOINTSERVER\OfficeServers' not found. Additional error information from SQL Server is included below. Cannot open database "WSS_Content" requested by the login. The login failed. Login failed for user 'SHAREPOINTSERVER\logbinderaccount'."
Through our research so far, we find it is a common error with SharePoint, occurring most often (a) in conjunction with an upgrade or (b) when SharePoint is accessed via a console application or service. The second scenario applies to LOGbinder for SharePoint. And this error occurs even though the account is a SharePoint farm administrator, with all privileges being assigned correctly.
The workaround is to add the account manually as a user to the SQL database WSS_Content, assigning permissions as SharePoint Data Access (SPDataAccess role). This works most of the time. However, we would like to get some more definitive answers on this issue. To do that, could you answer the following questions?
If you have had the error:
- Did it occur in your test or production environment?
- What did you do to work around the error?
If you have NOT had the error:
- For the account you use to run the LOGbinder agent, what SharePoint groups does it belong to?
- Is the account a domain account or a local user account?
- To what domain groups does it belong?
- What local groups?
- If you have a multi-server SharePoint farm, from which server is LOGbinder running? (database, front-end, application, etc.)
You may give us your response in a support ticket even if you do not have a current support contract. Any information you provide will be kept strictly confidential. Thank you.
3.9. Default Audit Policy Options
LOGbinder for SharePoint allows you to specify a “Default Audit Policy.” This allows you to define a policy once, and apply it to the site collections you specify—thus allowing for more consistency in audit settings.
The default audit policy can also be applied to new site collections. Thus, soon after a site collection is created, LOGbinder for SharePoint can automatically enable auditing and begin processing its audit logs.
Configure Inputs (SharePoint Site Collections)
There are now three ways to specify the audit settings for a site collection:
- “Custom audit policy”: Corresponds to Version 2.x, where you use LOGbinder to set the site collection’s audit policy.
- “Allow Site Collection Administrator to configure audit policy using SharePoint’s administration page”: This allows you to set the audit policy in SharePoint (if running the Microsoft SharePoint Server edition).
- “Use LOGbinder’s default audit policy”: Once the default audit policy has been defined, it can be applied to the site collection. If the default audit policy later changes, LOGbinder will automatically apply the changes to the site collection’s audit settings.
3.10. LOGbinder for SharePoint Restricted Lookups Option
LOGbinder for SharePoint by default makes every effort to fully translate and enrich SharePoint audit events through so called "lookups" where-in LOGbinder makes extra queries to SharePoint to obtain this information. But there is a cost/benefit relationship to be considered. Some events in the native SharePoint audit log include fields that are of low or no value to end users at many organizations. Each field in the native log, including these low or no value fields, requires a lookup by LOGbinder to resolve the native SharePoint data in to user friendly data.
For example, below is a sample of LOGbinder for SharePoint event ID 13:
Document checked in
Occurred: 6/25/2016 1:13:04 PM
Site: http://sp2010-sp
User: Administrator
Object
URL: Shared Documents/FinancialData.xlsx
Title: n/a
Version: 1.0
As you can see in the above event, the “Title” field returned from SharePoint is “n/a”. This is obviously of no value to the end user. Since SharePoint includes these low/no value fields, LOGbinder for SharePoint includes an option to intelligently restrict the number of lookups it processes resulting in increased performance of LOGbinder. You can manage the amount of SharePoint lookups by opening the LOGbinder Control Panel selecting File and then Options. The amount of lookups performed by LOGbinder can be customized by choosing a value under “Amount of SharePoint lookups.” See figure 1 below.
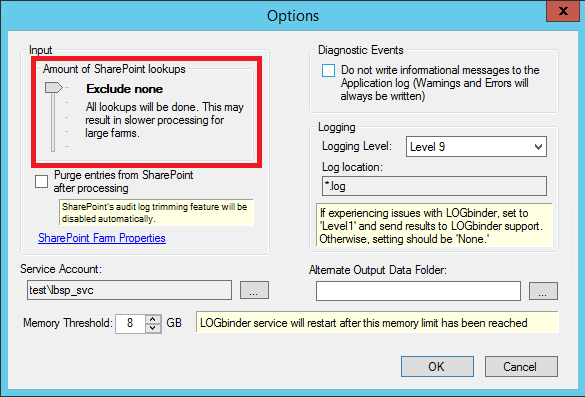
The fields that are affected (with the exception of the “Restrict all lookups option”) are all child fields of the targeted object. “URL” is the most important field included in the events and that field is always reported except on some permission change events and only if the “Exclude high/medium-cost” option is selected.
Most organizations who need to speed up LOGbinder can safely use the “Exclude high-cost lookups” option without losing significant audit information. Please note that the “Exclude high/medium-cost” option does adversely impact permission change events.
We have created a document that explains outlines which fields are affected depending on which option is selected when managing the amount of SharePoint lookups. You can find a link to the document on the LOGbinder for SharePoint resources page or by clicking here.
3.11. Audit log truncation and audit integrity
Occasionally we get feedback from customers that boils down to questions about truncated audit log output. It is important that security analysts and compliance officers understand some basic technology aspects of audit log processing because it helps them to grasp how audit integrity is preserved within the limits of audit log reporting.
Audit truncation: Just the facts
Some event logs from Exchange and SharePoint contain very large chunks of data. Which is fine, except for a simple and incontrovertible fact: there is a limit to the amount of data that can be written to common audit log outputs such as the Windows Event and Security log and Syslog.
- Windows Event and Security log limit events from about 27,000 to 32,000 bytes.
- Some implementations of Syslog limit the size to 65,000 bytes, while other Syslog variants have different limits.
An example of an excessive event in SharePoint would be when someone changes the layout of a list or document library, or adds a rule to sort the list: event 23 will include tons of information about all the schema changes which quickly adds up to tens of thousands of bytes. Another example: Exchange includes a field on some events called “Additional information” that can contain thousands of bytes only marginally-important from a security perspective.
There is no byte limit to file outputs.
What you need to know about audit integrity and LOGbinder’s audit log truncation
LOGbinder puts audit integrity ahead of other considerations in the course of its work. This does not mean that we don’t truncate logs when the required output demands it. For customers whose SIEM requires an output that imposes a limit to the size of recorded event, a decision must be made on how to deliver the event. (It would be unacceptable to just skip it and fail to deliver the audit event.)
In the case of an excessive byte-sized event, LOGbinder makes the decision to truncate what we view to be extraneous: information that can be retrieved via other means (such as the schema change we mentioned earlier) or that is less important to SIEM security analysts than the particulars about the event such as the “who did it, what did they do, and where did it happen”. Those field data elements are never too big.
When we truncate the event, we take extra care to deliver all that is possible. Our very cool technology truncates events only to the size insisted on by the SIEM-specific Syslog implementation for example, starting with the full amount and reducing until it is accepted.
Of course, no such truncation takes place if the LOGbinder output is directed to a plain text file.
It should be stated that, by a wide margin, most use-cases never encounter this issue. Security officers and SysAdmins have good reasons to narrow their monitoring focus to the most relevant audit events. They exclude the noise events which are typically those that would require truncation.
Audit integrity has always been a LOGbinder core value. Our architects and developers have gone to great length to ensure security analysts have what they need from audit logs, both for real-time security event information and forensic investigations– despite hard-coded technological limitations in common event logging formats. The ability to simultaneously direct output to a file that has no byte limitation is an expression of our core value.
LOGbinder for SharePoint even has a feature to configure “lookup levels” to allow organizations to configure their own suitable balance between system performance and the collected audit log detail.
3.12. FIPS Mode and LOGbinder software
Recently, 3 different customers in as many days came to us with the same problem: LOGbinder installation would return “Error 1001” and fail to install. We’re not sure why this suddenly became an issue mid-January 2016, but the problem turned out to be with the Local Security Policy setting enabling “FIPS mode”, specifically the security option called “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing”.
FIPS mode has an interesting history. We thought we’d pass along Microsoft’s TechNet post about it so you can understand how to address this issue should it come up in your organization.
In April 2014 Microsoft posted “Why We’re Not Recommending ‘FIPS Mode’ Anymore.” Prior to this post, Microsoft recommended a Local Security policy setting to impose compliance with a US Federal Information Processing Standard (FIPS) 140 requiring National Institute of Standards and Technology (NIST) validation of an implementation of cryptographic algorithms. When this setting was enabled a particular algorithm that had not been submitted to NIST would not be allowed on the local system.
However, the April posting listed multiple, compelling reasons why FIPS-140 is deficient, and even went so far as to call it “particularly onerous”. Enabling FIPS mode in Security Policy arbitrarily presumes that non-validated cryptographic classes are undesirable, when in fact they may be just as good and provide much faster operations. But the problems associated with applications using the .NET Framework are more troublesome. To quote the article:
“If FIPS mode is enabled, the .NET Framework disallows the use of all non-validated cryptographic classes. The problem here is that the Framework offers multiple implementations of most algorithms, and not all of them have been submitted for validation, even though they are similar or identical to implementations that have been approved...
Compounding the problem is that in most cases the Managed implementations of the various cryptographic algorithms have been available much longer than their Cng and CryptoServiceProvider counterparts, and on top of that, the Managed implementations tend to be significantly faster….
“Finally, the .NET Framework’s enforcement of FIPS mode cannot tell whether any particular use of a cryptographic class is not for security purposes and thus not in violation of standards.”
It is in this context that we report LOGbinder will not run if FIPS mode is enabled on the installed server. LOGbinder software uses Microsoft’s recommended cryptography implementations; they perform well and provide excellent protection. However, they are incompatible with FIPS mode.
If your organization must enable FIPS mode on the server running LOGbinder (for some reason greater than all the reasons not to do so as described in Microsoft’s post nearly 2 years ago), then contact our support desk using the word “FIPS” in the subject line. They can walk you through how to manually install files in the LOGbinder installation directory to overcome the security policy setting just for the LOGbinder application.
Click here to read the TechNet post: https://techcommunity.microsoft.com/t5/microsoft-security-baselines/why-we-8217-re-not-recommending-8220-fips-mode-8221-anymore/ba-p/701037
3.13. New technical updates posted and available for customers with current maintenance and support contracts - July 2015
Within the last few weeks (July 2015) we posted new versions of our software containing features and improvements to all 3 of our applications. Two major features will bring immediate performance benefits:
- Split Syslog output if over 100mb. Prior to this update, LOGbinder started a new Syslog output every day (with the file named appropriately), but some organizations’ audit activities would generate more than 1GB of data in a day. This large output file size caused problems. So, we updated all 3 of our applications to create a new file after every 100mb of output and creating a file name suited to this new schema.
- Streamlined internal audit request and delivery process. To protect the monitored application’s performance and stability, LOGbinder carefully manages the process by which it requests audit log data. Persistent audit log demands can cause harm to the application. We have released an update to all 3 of our products that adds further refinement to the audit request technology by improving the calculated times for audit request and processing. The net effect is reduced resource demand on the monitored application while maintaining delivery speed and audit integrity.
The new updates are available via the website’s download resource page. Customers with current support and maintenance contracts may download and apply these new updates at no additional charge.
3.14. “Run as Administrator” may be needed to initialize LOGbinder for SharePoint
When LOGbinder is first started, it must set up event sources necessary for its operation. So, in some environments and for the first run it may be necessary to start the LOGbinder application using the “Run as Administrator” option. Thereafter it should be enough to run the application as a user who is a member of the local Administrators group, but in practice we find that in some environments the user must always use "Run as administrator". Your circumstances may vary, but if the system returns a message containing “insufficient privileges for creating event source”, try the “Run as Administrator” to see if it doesn’t solve your problem.
3.15. Tech Tip: Manage the audit performance by tweaking the amount of excess information attached to the audit
One of the new features of LOGbinder SP 5.0 is the ability to dial-back internal processing to tweak audit performance. LOGbinder SP allows the control of how many lookups it should perform in order to obtain additional information while translating raw audit events to easy-to-understand audit entries. Examples of this could be resolving a user ID to user name or an object GUID to the actual name of the object. We include recommendations to help guide you in our LOGbinder for SharePoint Getting Started Guide. See pages 8 and 9 for details.
3.16. Where to find information about LOGbinder events
Every month we answer about 150,000 questions about events. But where do you go if you have a specific question about an event reported by LOGbinder? Some of our SIEM Synergy partners have collaborated with us to provide a hyperlink within their application to take you directly to the relevant event ID page. So when you see an event you wish to research, clicking on the hyperlinked Event ID will take you directly to the details page on Ultimate Windows Security’s Online Encyclopedia.
But what if your SIEM doesn’t have a hyperlink to the right page? You can still get the information by browsing to UltimateItSecurity.com and clicking on Security, then Encyclopedia. (https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/Default.aspx) Once there, select the source of the event (All Sources, Windows Audit, SharePoint Audit, SQL Server Audit or Exchange Audit). If you want to narrow the list use the drop-down box on the right, else browse the list of events and click on the appropriate one to get the full details. We list the events in numerical order, so they’re easy to find. (By the way, when you get a chance, send a note to your SIEM’s product manager to ask them to finish their integration so you can save yourself the trouble next time when you need the event information.)
If you still can’t find your answer there then click on the blue “Ask a question about this event” button and post your question in the Ultimate IT Security forum. LOGbinder is now sponsoring an Exchange, SQL and SharePoint forum there and you can expect a quick response from one of our technical engineers.
3.17. You want to run audit reports in SharePoint but LOGbinder for SharePoint purges the audit log
LOGbinder for SharePoint can automatically purge audit entries from SharePoint after they have been processed by LOGbinder for SharePoint and forwarded to an event log or your SIEM/Log Management solution. This purging occurs on a daily basis, but a buffer is maintained, so only entries older than 24 hours are purged.
This is usually sufficient to satisfy security and compliance requirements through the audit logs stored in the organization’s SIEM or log management solution. However, in some rare instances, it might be necessary to leave the audit logs in SharePoint in order to be able to run audit reports from within the SharePoint environment. The problem is that these logs are no longer available in SharePoint, since LOGbinder for SharePoint purged them.
In this case, the LOGbinder for SharePoint automatic purging feature needs to be disabled through the Options dialog on the LOGbinder interface. Since it will not process events it has already processed, not purging the logs from SharePoint will not create duplicate events in your log management.
Figure 1: Disable purging under LOGbinder for SharePoint Options
To avoid the logs to accumulate in SharePoint, taking up valuable resources and potentially degrading the performance of the site collection, SharePoint can be set to trim the audit log. Under Site Settings / Site Collection Administration group / Site collection audit settings options are available to trim audit logs when they reach a certain age (specified in number of days) and optionally be stored in a document library.
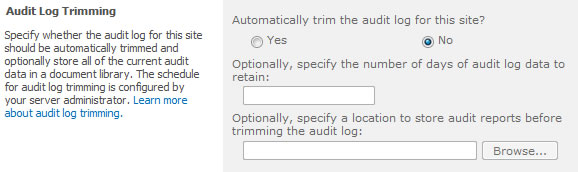
Figure 2: Enable trimming in SharePoint audit settings
Applying these changes you can benefit from the managing your logs with your preferred SIEM/Log management solution through LOGbinder, while still taking advantage of having access to the audit logs from SharePoint.
3.18. Why There's No Event for List Item Views
You may have noticed that there is no event from SharePoint auditing (and therefore LOGbinder for SharePoint) for "List item viewed". All you get are events telling the the overall List was viewed (event ID 49).
On the other hand, for document libraries and documents you get events for when the library is viewed (event ID 48) and when documents are viewed that identity the individual document (47).
This seems like a hole in the SharePoint audit trail at first but when you think about it, it makes sense.
It's easy to audit when a document is viewed but not for list items. You see, the document's contents cannot be displayed as a column in a View, so the viewing or downloading of a document is a very discreet event. On the other hand you can display any and all properties of a list item in a view.
You can potentially view any list item in full detail anytime you view a list. To provide an audit trail of list item views, it would be necessary to output an "item view" event for every item included by the filter criteria of the view each time the view is viewed or refreshed.
3.19. How to change the LOGbinder service account password
If the password for the LOGbinder service account changes, it also has to be changed on the LOGbinder service.
- Open Services.msc
- Find the LOGbinder service and open its properties
- On the Log On tab, set the new password for the LOGbinder service account
3.20. Diagnostic logs – Use them and let them go
Back in December 2015 we offered a tech tip to turn diagnostic logging on when troubleshooting. Like many things, diagnostics reach a point at which the diagnostic is complete. When this happens, turn off the diagnostic log function within LOGbinder! For one thing diagnostic logs can place a huge amount of data in the C:\ProgramData\LOGbinderXX folder. More important, diagnostic logging slows down the processing speed of the LOGbinder service.
Unless our support team is working with you on an issue, you will want to turn diagnostic logging off to conserve system resources.
3.21. LOGbinder troubleshooting tip: Use the Diagnostic Logs
By a wide margin, the support issues we hear about are resolved by revisiting the steps provided in the Troubleshooting section of the LOGbinder application’s Getting Started Guide. Our support desk reports that most customers “self-serve” by checking that section or even the Windows Event Viewer for details, but only after first submitting a trouble ticket. We are happy to have such feedback by the way; it helps us to make sure our installation guides are comprehensive.
But here’s a tip for all the other support issues where such “Tier 1” steps don’t fix the problem: review the LOGbinder diagnostic log file(s). Here’s how to generate this troubleshooting file(s):
-
Choose “File | Options” from LOGbinder control panel.
-
Set “Logging level” to Level 1 and start or restart the service.
-
Waiting for the issue to happen again, find all log files in C:\ProgramData\LOGbinderXX folder (where XX=SP, SQL or EX for the SharePoint, SQL Server or Exchange audit solution). The log files will have a “.log” suffix to the file name. The number of log files in the folder will depend on the LOGbinder application.
Very often the bit of information needed to resolve a problem is contained in the LOGbinder-generated diagnostic log files. Customers often successfully troubleshoot their issues by perusing these files.
If you need our technicians to help you with a particular problem connected to LOGbinder, open a support ticket and attach these level 1 diagnostic files (compressed into a zip file). Doing so will greatly decrease the time it takes for our technicians to help you solve the problem. Many of the initial questions the support desk will have are answered in one or more of these diagnostic log files.
After the problem is resolved, remember to turn off diagnostic logging to conserve disk space and CPU time.
3.22. LOGbinder for SharePoint 6 Features
In May 2016 Microsoft released SharePoint 2016 but due to a bug in Exchange 2016, we wanted to make sure that we performed very extensive testing of SharePoint auditing to make sure we didn’t discover any bugs. We also performed very stringent testing of LOGbinder for SharePoint to make sure that our software continues to meet and exceed our internal standards.
What is new in LOGbinder for SharePoint 2016?
- Support for SharePoint 2016 On-Premises
- New installer – Our new installer automates some of the prerequisites required during the installation process. Installation time is now just a couple of minutes.
- Improved service resilience – A few customers have reported to us that from time to time the LOGbinder service is stopped. The detailed service logs showed that delays between SharePoint and the farms’ SQL Server were causing timeouts. These timeouts were being reported by SharePoint and were long enough to negatively impact the LOGbinder service. Now the LOGbinder service will handle these interruptions with less impact.
- Weird username prefixes removal – Some customers were wondering why they are seeing weird characters prefixing usernames in the logs. You can find more info about it here. We have included an option to remove the claim type characters from the data.
- Site collection selection – Managing a handful of site collections is easy. Some customers though have thousands and thousands of site collections being monitor. Now you can use CTRL-A to select all site collections in the LOGbinder input.
These are just a few of the improvements in this release of LOGbinder for SharePoint.
Customers with current support and maintenance contracts can access the latest version at the link below. To upgrade to the latest version just run the installer on top of the previous version. No data or settings will be lost.
3.23. How to Audit an Individual Library or List in SharePoint
- Viewing
- Editing
- Deletion
- Check in /Check out
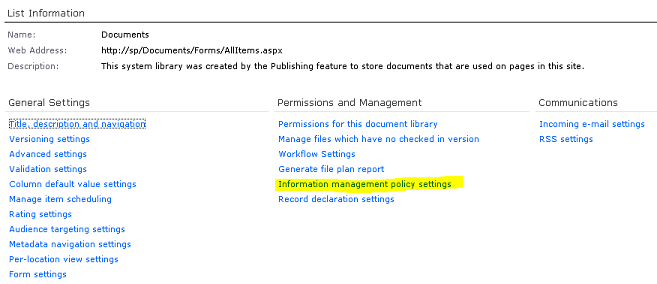
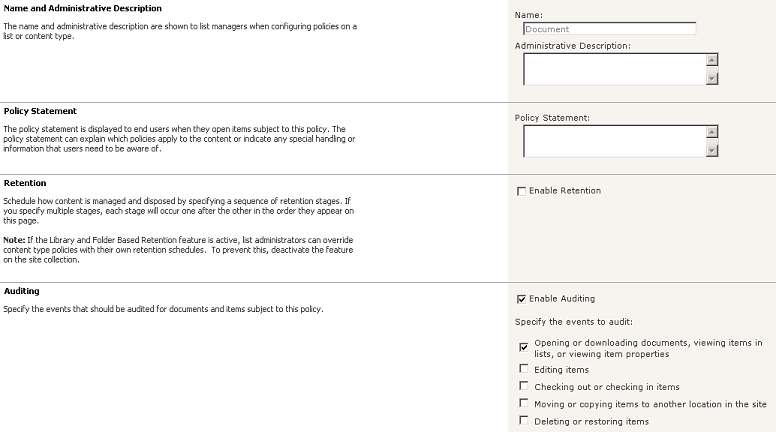
3.24. Recovery options for LOGbinder service
The other day our support staff received the following error:
LOGbinder error
Error when translating entries. Details: A transport-level error has occurred when sending the request to the server. (provider: TCP Provider, error: 0 - An existing connection was forcibly closed by the remote host.); at System.Data.SqlClient.SqlConnection.OnError(SqlException exception, Boolean breakConnection) ...
After some investigation, we found it was because the SQL server that SharePoint was installed on was rebooted. Well, first of all, we put in a ticket to improve the message. But what can be done to keep LOGbinder running?
In the Services MMC snap-in, open the properties of the LOGbinder service, and go to the Recovery tab. You can set the recovery option for first, second, and subsequent failures to "Restart the Service." We would suggest changing the value of "Restart service after" to 15 minutes, to allow SQL to restart.
Let us know what you find practical for your organization.
3.25. New Syslog Features in LOGbinder SP 4.0.5
We have a quick update to LOGbinder for SharePoint for all of you who are using Syslog to forward your SharePoint audit log to your favorite SIEM.
LOGbinder for SharePoint version 4.0.5 adds the following new features:
- Alternate Output Data Folder: It is now possible to change the default data folder, which is also used for the output data. This is the folder where LOGbinder stores its outputs that are written in files, as well as the diagnostic files. Now you can store these in a different folder, or on a different hard drive, or even in shared folder on a different server. You will find this useful, if you need to separate software and data, or you have the requirement of using minimal disk space on the hard drive where your programs are installed.
- Network locations for Syslog output: As a result of the above change, it is now possible to use network location for Syslog outputs, such as Syslog-Generic (File) and Syslog-CEF (File). These files, in turn, can be easily accessed by your SIEM.
- Test button for Syslog output: A "Test" button is now available for Syslog outputs that sends a test Syslog message using the specified address/port. When setting up LOGbinder to output to a Syslog server for your SIEM to collect the logs, the most difficult part can be to ensure that firewalls and other settings don't block the traffic from LOGbinder to the Syslog server. The "Test" button will assist you in setting up and testing this connection.
- Output file name clarification: The sample file name for the Syslog (File) outputs now correctly indicates that the date is included in the file name.
If you would like to take advantage of the above feature, please go ahead and download LOGbinder for SharePoint.
4. Resources
4.1. LOGbinder for SharePoint Version History
LOGbinder for SharePoint 8.0.1 (11/28/2023)
- Trim long events before writing to event log
- Better error reporting for FIPS related issues
- Do not try to set site collection administrator for ReadOnly sites
- Reduce max time range to 2 days to improve performance in certain situations
- Upgrade to .NET Framework 4.8
- Some user interface accessibility improvements
- Remove support for SharePoint 2007 and 2010
LOGbinder for SharePoint 7.0.15 (4/24/2021)
- Handle case if site is deleted before purge
- Skip site if it is temporarily read-only
LOGbinder for SharePoint 7.0.7 (1/27/2020)
- Fix loading appropriate SharePoint DLL
- Add Netwrix SharePoint Audit Event
LOGbinder for SharePoint 7.0.1 (11/13/2019)
- Change many parts of memory management to significantly reduce memory consumption
- Add event filtering options (ability to filter out events from processing based on user-specified URL patterns)
- Add better error handling for certain errors
- Retry certain failed actions a few times, in case the problem is temporary
- Don't stop on certain errors that are either recoverable or localized to few site collections
- Speed up outputting to Syslog and Syslog files
- Retry creating/opening Syslog files on error
- Add noise event statistics (displaying how many noise events were suppressed)
- Fix noise event filtering for all outputs
- Add error handling for corrupted settings file
- Add Microsoft.SharePoint.dll version 16 for SharePoint Server 2016 support
- Many performance improvements
- Many bug fixes
LOGbinder for SharePoint 6.1.52 (1/1/2019)
- New code signing certificate
LOGbinder for SharePoint 6.1.48 (8/13/2018)
- Fixed a regression bug
LOGbinder for SharePoint 6.1.36 (6/3/2018)
- Corrected some CEF problems (a duplicate field in some events and escaping '=' signs)
LOGbinder for SharePoint 6.1.29 (3/28/2018)
- Some minor fixes
LOGbinder for SharePoint 6.1.27 (3/9/2018)
- Handle multiple NICs correctly for Syslog outputs
LOGbinder for SharePoint 6.1.24 (12/22/2017)
- Fixed Syslog date to use US format of month names instead of internationalized versions
- Fixed a small regression bug
LOGbinder for SharePoint 6.1.20 (11/17/2017)
- Added user option to set batch size
- Added sorting capability to input columns
- Added feature to select inputs by searching for text included in their names
- Added date range to event 551
- Fixed an issue relating inspection
LOGbinder for SharePoint 6.1.11 (11/1/2017)
- Increased allowed memory threshold
LOGbinder for SharePoint 6.1.9 (8/8/2017)
- Fixed a date issue due to regional settings
LOGbinder for SharePoint 6.1.7 (7/7/2017)
- Increased LOGbinder service startup timeout
LOGbinder for SharePoint 6.1 (2/24/2017)
- Added statistics to informational events
- Information includes processed file names, elapsed time, EPS (events per second)
- New and improved installer
- Refined service start/stop process
- Improved resilience when site collection names are temporarily not retrievable
- Improved handling of SharePoint out-of-memory errors
- Changed some LOGbinder message terminology
- Added option to specify installation folder other than the default
- Removed reporting and event nodes from the Control Panel
- Fixed issue when adding secondary site collection administrator
- Fixed claims encoding not considered when adding secondary site collection administrator
- Fixed crushing when setting last processed date to a future date
- Fixed not issuing tamper warnings
- Several other updates and improvements
LOGbinder for SharePoint 6.0 (10/31/2016)
- Support for SharePoint 2016 On-Premises
- New installer automates some prerequisites
- Service will not shutdown if there is an interruption between SharePoint and the SQL Server
- Option to remove the claim type data prefix from usernames
- Select all site collections using "CTRL-A"
- If a site collection goes offline or is unreachable it will not get set to "Not Monitored" immediately
- Removed support for Windows Server 2003
- Microsoft .NET Framework minimum requirement is version 4.5.1
LOGbinder for SharePoint 5.1.13 (5/24/2016)
- Handle invalid XML in search event #24
- Note: The event's output is unchanged (i.e. we do not strip characters from the search string)
- Allow customer to set memory threshold to restart service
- Range that can be chosen is from 2GB-10GB. Default setting is 8GB. Setting in Options window.
- Fix output for events #65, 66
LOGbinder for SharePoint 5.1.12 (3/18/2016)
- Fix for issue found with 64bit .msi installer in some environments
LOGbinder for SharePoint 5.1.9 (1/16/2016)
- Bug Fix for outputting LEEF in UDP
LOGbinder for SharePoint 5.1 (4/24/2015)
- New events: #64 “Item declared as a record”, #65 “Item undeclared as a record”, #66 “Policy deleted” for undocumented SharePoint events
- Improve memory usage by responding more quickly when reaching memory threshold, in order to deal with SharePoint memory management issues
- If LOGbinder is forced to restart because of memory usage, resume at the next site collection where it left off, instead of the first one
- Improve handling of a site collection being deleted while LOGbinder is running
- Improve handling of identifying servers in farm that require licensing, so that multiple servers with same IP address will not be counted multiple times
- Add role name and description to event #32
- Improve handling of Syslog error "non-blocking socket operation could not be completed"
- A number of other internal improvements
LOGbinder SP 5.0.29 (1/16/2015)
- Fix missing details in certain events
LOGbinder SP 5.0.28 (10/24/2014)
- Fix problem if writing large warning event
LOGbinder SP 5.0.23 (10/1/2014)
- Add support for LEEF output
LOGbinder SP 5.0.15 (9/2/2014)
- Add option to tune SharePoint lookups so that customer has control over how many lookups are done
- Add to Options the ability to change LOGbinder's output directory
- Adjust Output window to indicate that date is part of CEF/Syslog file name
- Adjust way of getting paths
- Make LOGbinder Control Panel / Service start more efficiently
- Rework caching to ensure efficiency
- Do not process event backlog when starting
- Do not remove site collection administrator when adding service account
- Improve handling when SharePoint loses connection to SQL server
- Handle memory error from Security log
- Fix bug where enabling security log created error when starting service from Control Panel
LOGbinder SP 4.0.5 (2/27/2014)
- Allow to use network location for Syslog output, by changing Alternate Output Directory in Options
- Add Test button to Output properties of Syslog outputs to test connection
- Adjust sample file name in Output properties window so that it indicates that the date is included in the file name
LOGbinder SP 4.0.3 (10/4/2013)
- Fix handling of SharePoint permissions updated/removed according to some undocumented changes by SharePoint
LOGbinder SP 4.0.1 (9/6/2013)
- Allow service to restart properly after a site collection is deleted
LOGbinder SP 4.0.0 (9/2/2013)
- Support SharePoint 2013
- If service not installed, install when LOGbinder Control Panel starts. Also allow install/uninstall by double-clicking on service in status bar
- Reduce large memory consumption for long periods of time
- Give more meaningful message if bad credentials entered during installation
- Adjust installer so installs for all users properly
- Not adjust secondary site collection administrator if not necessary
LOGbinder SP 3.6.6 (6/6/2013)
- Fix 32-bit installer
LOGbinder SP 3.6.5 (4/15/2013)
- Truncate large events being written to Security log
- Improve error reporting
LOGbinder SP 3.6.4 (3/19/2013)
- Fix bug if SharePoint custom event and event name is empty
LOGbinder SP 3.6.3 (3/7/2013)
- Do not set site collection administrator needlessly
LOGbinder SP 3.6.0 (3/1/2013)
- Add option for adjusting properties of multiple inputs
- Add option to exclude personal sites from default audit policy
- Add Central Administration site collection monitoring
- New event #63 “Content type imported”
- New event #550 “LOGbinder process report”
- New event #558 “LOGbinder process warning”
- Fixed several small issues
LOGbinder SP 3.5.15 (1/21/2013)
- Adjust CEF fields for ArcSight certification
- Fix issue with messages file to format dates in international format
- Fix to allow Conserve Resources option to be saved
LOGbinder SP 3.5.12 (10/5/2012)
- Truncates details for event 22 Object profile changed and 23 SharePoint object structure changed. Details will have limit of 1000 characters
LOGbinder SP 3.5.11 (9/10/2012)
- Add output option for Syslog-Generic and Syslog-Generic (File)
- Add output option for Syslog-CEF and Syslog-CEF (File)
- New option to “Conserve resources with lookups”
- Reset connection to SharePoint site collection after 90 minutes
- Diagnostic log splits after reaches 10MB in size
LOGbinder SP 3.1.0 (6/22/2012)
- Enable Security log output during Trial period
- Add event #61 “Retention policy processed”
- Add event #62 “Document fragment updated” for FileFragmentWrite audit type
- Reset SharePoint connection automatically after 23 hours
- Fix several small issues
LOGbinder SP 3.0.0 (3/6/2012)
- Add farm-wide default audit policy
- New site collections automatically audited
- Add new ways to specify the audit settings for a site collection
- Add SharePoint Farm Properties window
- Add automatic tamper detection and response
- Add event #60 “Possible tampering warning”
- Add access to LOGbinder Diagnostic Events from within LOGbinder
- Add “Reports” that contain our recommended SIEM reports
- Update the text of the output properties window to make the options more clear
LOGbinder SP 2.1.10 (12/12/2011)
- Several updates and improvements
LOGbinder SP 2.1.7 (9/1/2011)
- Several updates and improvements
LOGbinder SP 2.1.1 (2/23/2011)
- Several updates and improvements
LOGbinder SP 2.0.2 (8/19/2010)
- Several updates and improvements
LOGbinder SP 1.9.0 (7/1/2010)
- Several updates and improvements
LOGbinder SP 1.2.0 (3/31/2010)
- Several updates and improvements
LOGbinder SP 1.1.3 (2/26/2010)
- Several updates and improvements
LOGbinder SP 1.1.2 (2/13/2010)
- Several updates and improvements
LOGbinder SP 1.1.1 (2/11/2010)
- Several updates and improvements
LOGbinder SP 1.1.0 (2/8/2010)
- Several updates and improvements
LOGbinder SP 1.0.1 (10/7/2009)
- Several updates and improvements
LOGbinder SP 1.0 (9/25/2009)
- First release
4.2. Video Demo: Installation and Configuration
The video below shows the installation, configuration and use of LOGbinder for SharePoint. In the video we also walk through and explain all of the options found in LOGbinder for SharePoint.
You might need to right-click and select Play or Show Controls on the video below.
4.3. LOGbinder for SharePoint FAQ
Where can I learn more about the SharePoint Audit Log?
Visit Randy's SharePoint section at UltimateItSecurity.com.
What can I monitor with the SharePoint Audit Log and LOGbinder for SharePoint?
What does LOGbinder for SharePoint do to my SharePoint installation? Does it modify SharePoint? Will it conflict with any other SharePoint extensions or modifications?
"Nothing" and "no" are the short answers. LOGbinder for SharePoint is a Windows service that runs independently of SharePoint. There are NO changes to SharePoint whatsoever other than configuring SharePoint's audit feature and purging the SharePoint audit log of old events if you configure LOGbinder for SharePoint to do so.
Will LOGbinder for SharePoint slow down my server or cause other resource issues?
No, the LOGbinder for SharePoint service is a tiny executable program that efficiently checks the SharePoint audit log for entries and uses limited resources while processing events.
LOGbinder for SharePoint runs at a lower priority than SharePoint, so it will never compete with SharePoint for resources.
Your SharePoint audit policy has the biggest impact on what resources LOGbinder needs; for each site collection, consider whether you really need to audit read/view access.
How secure is LOGbinder for SharePoint?
LOGbinder is fully integrated with Windows security and complies with widely accepted secure design and coding techniques.
At installation, LOGbinder secures the folder permissions where the software files reside. To protect LOGbinder's configuration from tampering, LOGbinder encrypts its configuration data.
LOGbinder security requirements are greatly simplified since LOGbinder does not store your audit log data. LOGbinder is designed to quickly get audit events out of the SharePoint audit log and to the destination of your choice, at which point your log management solution takes over. If you configure LOGbinder for SharePoint to direct events to the Windows security log, you leverage the significant effort Microsoft has invested in protecting the security log. And if you are already collecting Windows security logs with your log management application, SharePoint events will automatically be included when you install LOGbinder for SharePoint.
LOGbinder for SharePoint's design helps you fulfill separation of duty and audit trail integrity requirements by quickly getting audit events off the system where they are produced (and thus vulnerable to intruders or malicious administrators) and into your separate and secure log management system.
Does LOGbinder for SharePoint require much configuration?
LOGbinder for SharePoint installs in about 2 minutes and only requires a few settings:
- Select which site collections for LOGbinder to translate the audit log
- Specify the user account LOGbinder should run as
- Choose whether to output events to the custom LOGbinder SP event log, to the actual Windows Security Log, syslog or to a text file.
How do you monitor LOGbinder for SharePoint’s health?
Check the Application log for warnings or errors from source LOGbndSE.
Why doesn’t LOGbinder for SharePoint include alerting or long term archival capability?
These are functions of a log management solution. LOGbinder complements and enhances the value of your log management solution.
How does LOGbinder for SharePoint integrate with my current log management solution?
With LOGbinder, any log management solution that supports Windows event logs, text file or syslog can now collect, monitor, archive, and report on SharePoint audit log activity. Also, see next Q&A.
Which output formats does LOGbinder for SharePoint currently support?
LOGbinder can output to either the Windows Security Log, syslog, text file, or a custom Windows event log called LOGbinder for SharePoint.
How is LOGbinder for SharePoint licensed?
Does LOGbinder for SharePoint need to be installed on the SharePoint server?
You do not need to install LOGbinder for SharePoint on a production SharePoint server.
The SharePoint object model classes that provide access to the SharePoint audit log require code to run locally. To audit a given SharePoint farm, LOGbinder for SharePoint needs to be installed on just one of the servers to fully audit the farm. This can be an existing SharePoint production server or a new server you deploy for LOGbinder for SharePoint (usually a virtual machine).
What user credentials must be assigned to LOGbinder for SharePoint? Why?
The account used to run the LOGbinder application must be a member of the server's local Administrators group and a SharePoint farm administrator. The account you choose for the LOGbinder service (which can be the same) must also be a SharePoint farm administrator and an administrator on each site collection being monitored. These requirements come from SharePoint in order to access the SharePoint audit log. This account needs to be authorized to run as a service, and if outputting the Security log, must be authorized to write to the Security log.
Does LOGbinder for SharePoint support multiple SharePoint site collections?
Yes. With LOGbinder for SharePoint you can configure the SharePoint audit policy and enable/disable translation of the audit log for each site collection on the SharePoint server.
4.4. End User License Agreement
END-USER LICENSE AGREEMENT
IMPORTANT. PLEASE READ THIS LICENSE AGREEMENT BEFORE LOADING THE SOFTWARE ONTO YOUR COMPUTER/SERVER.
This End-User License Agreement (“EULA”) is a legal agreement between you (a single entity) and Monterey Technology Group, Inc. (“Licensor”) for the license of the Software from Licensor accompanying this EULA. If you have entered into an agreement with Licensor, this EULA supplements and is a part of your agreement and is incorporated into your agreement. If you have not yet entered into any other agreement or contract with Licensor, this EULA is a binding, independent legal agreement between you and Licensor. By clicking “I agree,” or by installing, copying, modifying, registering, or otherwise using the Software, you agree to be bound by the terms of this EULA.
If you do not agree to accept all of the terms of this EULA, without any changes, additions or subtractions, please promptly click “I do not agree,” uninstall and remove the Software from your system, all of your computer(s), server(s), and/or your network, and return the Software to Licensor.
DEFINITIONS:
The following definitions apply to terms as they appear in this EULA:
(a) “EULA” means this End-User License Agreement.
(b) “Software” means the software accompanied by this EULA.
(c) “Licensor” means Monterey Technology Group, Inc.
(d) “You” means you, a single entity.
(e) “computer” and “server” each mean a single computer server.
THE SOFTWARE:
The Software is owned by and the property of Licensor. The Software is protected by the copyright laws of the United States of America, as well as international treaties protecting copyrights, as well as other intellectual property laws and treaties. While Licensor continues to own the Software, you will be granted, under this EULA, certain limited rights only to use the Software after your acceptance of this EULA.
LICENSE GRANT:
This EULA grants you the following rights:
(a) For any SharePoint farm where this software is used, this software must be licensed for the total number of servers on the farm. For the avoidance of doubt, you must purchase multiple licenses equal to the number of servers on the farm.
(b) Notwithstanding the foregoing, You may make one copy of the Software for archival purposes, or copy the Software onto the hard disk of your server as a single copy and retain the original for archival purposes. In the event that you make such a copy, you must ensure that the proprietary, copyright, trademark or other such notices contained in or placed on the Software are affixed to any such copy in the same location and manner as it appears in or on the Software.
(c) You may, after prior written notice to Licensor and Licensor’s consent, which shall not be unreasonably withheld, transfer the Software on a permanent basis to another person or entity, provided that you retain no copies of the Software and that the transferee agrees to all of the terms of this agreement and provides written notice of its agreement to Licensor.
(d) You may only use the Software for commercial purposes, and not for personal or household use.
DESCRIPTION OF OTHER RIGHTS AND LIMITATIONS:
(a) You may not copy any documentation which accompanies the Software.
(b) You may not sublicense, rent, or lease the Software, in part or in whole, or host the Software on your server for others to use. You may not allow the use of the Software as a service bureau.
(c) You may not reverse engineer, decompile, disassemble, modify, adapt, alter, integrate, translate, convert into human readable form, or make any attempt to discover, view or read the source code of the Software. You may not create derivative works, modifications or improvements to, of, from or on the Software.
(d) The Software is a single product. It may not be separated into its individual parts for use on any other server or computer.
(e) You may not transfer the Software to any third party without the prior written consent of Licensor.
(f) You may not use a previous version or copy of the Software after you have received a replacement or an upgraded version as a replacement of the Software. All copies of any prior version must be destroyed.
(g) Software installation, setup and maintenance is your sole responsibility. Licensor shall have no obligation or responsibility for software installation, setup or maintenance.
(h) You agree and grant Licensor the right to enter your premises and to access electronically at any time your server/computer as installed in order to verify your compliance with this EULA.
(i) All rights not expressly granted are reserved by Licensor. This EULA does not grant you any rights in connection with any copyrights, trademarks or service marks of Licensor.
(j) The Software may include copy protection or sunset technology to prevent the unauthorized copying or use of the Software. You agree that you will not circumvent any copy protection technology in the Software.
(k) This EULA does not require Licensor to provide to you any maintenance, updates, new versions, or support services related to the Software. The Licensor may or may not support the Software or any particular versions of the Software. Any services provided by Licensor, if any, may be described in the governing services agreement. Any supplemental software code, updates, modifications, or upgrades provided to you, whether as part of any support services or otherwise, are considered part of the Software and subject to the terms and conditions of this EULA. You acknowledge and agree that Licensor may use for its business purposes, including product support and development, any information you provide to Licensor whether the provision occurs during any support services, warranty claim or otherwise.
(l) Without prejudice to any other rights, Licensor may immediately terminate without notice this EULA if you fail to comply with any terms or conditions of this EULA.
(m) Returns and refunds are not accepted.
(n) You agree that you will not use the Software for any non-commercial purposes. You agree that you will not use the Software for personal or household purposes.
(o) You represent that you are authorized on behalf of your business or enterprise to enter into this EULA.
(p) You agree that you will not, during or after the termination of this EULA, contest or challenge Licensor’s ownership of, or interest in, the Software.
(q) You may not remove any copyright or other proprietary rights notices on any label of disks or other storage media containing the Software or in any documentation for the Software. You shall ensure that Licensor’s copyright and proprietary rights notices are not disabled and remain conspicuously displayed as provided in the Software.
UPGRADES:
Any are subject to all terms and conditions of this EULA.
INTELLECTUAL PROPERTY RIGHTS:
The Software, including but not limited to any and all source code, object code, software product, images, audio files, photographs, animations, macros, applets, video, music, text, the accompanying printed materials, related instructional material (whether in the Software, provided with the Software, or available concerning the Software), and documentation, is copyrighted with all rights reserved. You agree that Licensor, or third parties where appropriate, own(s) all rights to and in the Software, including without limitation all copyrights, proprietary rights, trademarks, service marks, patents, patent rights and trade secrets, as well as any and all such things for any modifications, derivatives, or improvements of the Software, or any part thereof, which you, Licensor, or others may make (in whole or in part), whether authorized or not.
NO WARRANTY:
The Software is provided as is and without any warranty.
DISCLAIMER OF WARRANTIES:
Licensor does not warrant any specific level of system functionality, availability or uptime.
LICENSOR HEREBY DISCLAIMS, AND DOES NOT MAKE, ANY AND ALL EXPRESS, IMPLIED, AND STATUTORY WARRANTIES, INCLUDING WITHOUT LIMITATION ANY IMPLIED WARRANTIES, DUTIES OR CONDITIONS OF MERCHANTABILITY, OF FITNESS FOR A PARTICULAR PURPOSE, OF ACCURACY OR COMPLETENESS OF RESPONSES, OF RESULTS, OF WORKMANLIKE EFFORT, OF LACK OF VIRUSES, OF LACK OF NEGLIGENCE AND OF NON-INFRINGEMENT. WITH RESPECT TO THE SOFTWARE, THERE IS NO WARRANTY OR CONDITION OF TITLE, QUIET ENJOYMENT, QUIET POSSESSION, CORRESPONDENCE TO DESCRIPTION OR NON-INFRINGEMENT. On occasion, all software has glitches or unforeseen errors, and consequently, Licensor makes no warranties and disclaims any and all warranties that the Software will function without interruption.
EXCLUSION OF INCIDENTAL, CONSEQUENTIAL AND CERTAIN OTHER DAMAGES:
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, IN NO EVENT SHALL LICENSOR BE LIABLE FOR ANY SPECIAL, INCIDENTAL, INDIRECT, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING, BUT NOT LIMITED TO, DAMAGES FOR LOSS OF PROFITS OR CONFIDENTIAL OR OTHER INFORMATION, FOR BUSINESS INTERRUPTION, FOR PERSONAL INJURY, FOR LOSS OF PRIVACY, FOR FAILURE TO MEET ANY DUTY INCLUDING OF GOOD FAITH OR OF REASONABLE CARE, FOR NEGLIGENCE, FOR LOSS OF DATA, AND FOR ANY OTHER PECUNIARY OR OTHER LOSS WHATSOEVER) ARISING OUT OF OR IN ANY WAY RELATED TO THE USE OF OR INABILITY TO USE THE SOFTWARE, THE PROVISION OF OR FAILURE TO PROVIDE SUPPORT SERVICES, OR OTHERWISE UNDER OR IN CONNECTION WITH ANY PROVISION OF THIS EULA, EVEN IN THE EVENT OF THE FAULT, TORT (INCLUDING NEGLIGENCE), STRICT LIABILITY, BREACH OF CONTRACT OR BREACH OF WARRANTY OF LICENSOR, AND EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
LIMITATION OF LIABILITY AND REMEDIES:
NOTWITHSTANDING ANY DAMAGES THAT YOU MIGHT INCUR FOR ANY REASON WHATSOEVER (INCLUDING, WITHOUT LIMITATION, ALL DAMAGES REFERENCED ABOVE AND ALL DIRECT OR GENERAL DAMAGES), THE ENTIRE LIABILITY OF LICENSOR WHETHER UNDER ANY PROVISION OF THIS EULA, OR FROM ANY OTHER SOURCE OF LIABILITY, WHETHER IN CONTRACT OR IN TORT, INCLUDING NEGLIGENCE, AND YOUR EXCLUSIVE REMEDY FOR ALL OF THE FOREGOING (EXCEPT FOR ANY REMEDY OF REPAIR OR REPLACEMENT ELECTED BY LICENSOR WITH RESPECT TO ANY BREACH OF THE LIMITED WARRANTY), SHALL BE LIMITED TO THE AMOUNT ACTUALLY PAID, WITHIN THE ONE (1) CALENDAR YEAR PRECEDING THE TIME YOU MAKE A CLAIM TO LICENSOR OF SUCH DAMAGES, BY YOU TO LICENSOR FOR THE SOFTWARE THAT CAUSED THE DAMAGES OR THAT IS THE SUBJECT MATTER OF OR DIRECTLY RELATED TO THE CAUSE OF ACTION. IN NO EVENT WILL LICENSOR BE LIABLE FOR ANY DAMAGES CAUSED, IN PART OR IN WHOLE, BY YOUR FAILURE TO PERFORM YOUR OBLIGATIONS, OR FOR ANY LOSS OF DATA, PROFITS, SAVINGS, OR ANY OTHER CONSEQUENTIAL OR INCIDENTAL DAMAGES, OR FOR ANY CLAIMS BY YOU BASED UPON A THIRD-PARTY CLAIM.
SOME STATES DO NOT ALLOW THE LIMITATION OR EXCLUSION OF LIABILITY FOR CERTAIN TYPES OF DAMAGES, SO THE ABOVE LIMITATIONS OR EXCLUSIONS MAY OR MAY NOT APPLY TO YOU. THE PROVISIONS IN THIS PARAGRAPH WILL APPLY REGARDLESS OF WHETHER YOU ACCEPT THE SOFTWARE.
YOUR EXCLUSIVE REMEDY:
Licensors sole obligation and entire liability, if any, shall be, at Licensor=s option from time to time exercised subject to applicable law, to repair or replace the Software, so long as you return the original Software. If such a remedy is elected by Licensor, you are responsible for any expenses you may incur (e.g. cost of shipping Software to Licensor). Any replaced parts shall become the property of Licensor. Any replaced Software will be warranted with the same limited warranty set forth above for the longer of the amount of time left in the original warranty period or thirty (30) days. To exercise your remedy, contact Licensor at the address listed below.
CONFIDENTIALITY :
You acknowledge the Software, including its source code and know-how relating to such things, constitute confidential information of Licensor (collectively, “Confidential Information”). You (“Disclosee”) will therefore: (a) will take reasonable steps (including those steps that the Disclosee takes to protect its own information that it regards as confidential) to keep the Confidential Information confidential; and (b) will not disclose or otherwise make available, except as otherwise provided by law, the Confidential Information of the other party to any third party except to such directors, officers, employees and agents of the Disclosee who have a need to have access to the Confidential Information of the other party to perform their obligations to the other party under this EULA. The confidentiality provisions of this paragraph will not apply to Confidential Information that: (a) is in the public domain other than as a consequence of a breach of the obligations contained in this EULA to maintain the confidentiality of such Confidential Information; (b) is established by Disclosee’s documents as being known by the Disclosee prior to its disclosure to the Disclosee hereunder or is independently developed by the Disclosee without breach of the obligations contained in this EULA; or (c) has been received by the Disclosee from a third party who is not subject to obligations similar to the obligations contained in this EULA. In the event that the Disclosee receives notice indicating that it may or will be legally compelled to disclose any of the Confidential Information, it will provide Licensor with prompt notice so that the Licensor may at its sole discretion seek a protective order or other appropriate remedy and/or waive compliance with the provisions of this EULA. In the event that such protective order or other remedy is not obtained for whatever reason, or that such other party waives compliance with the provisions of this EULA, the Disclosee may furnish only that portion of the Confidential Information that he or she is legally required to disclose. The foregoing agreements and covenants set forth in this paragraph will be construed as being an agreement independent of the provisions in this EULA. The existence of any claim or cause of action of either party against the other party, whether predicated on this EULA or otherwise, shall not constitute a defense to the enforcement by such other party of any of the covenants and agreements of this paragraph. Each of the parties acknowledges that its failure to comply with the provisions of this paragraph will cause irreparable harm to the other party which cannot be adequately compensated for in damages, and accordingly acknowledges that the other party will be entitled, in addition to any other remedies available to it, to interlocutory and permanent injunction relief to restrain any anticipated, present or continuing breach of this paragraph.
In the event you breach this EULA, Licensor shall have the right, at its sole option, to terminate this EULA or any portion of this EULA, in addition to any other available remedies.
Upon Termination of this EULA. Upon the termination of this EULA: (a) Your confidentiality obligations, as well as any accrued payment obligations to Licensor, shall survive such termination; (b) your license right to the Software shall immediately cease, and (c) you shall: (i) return to Licensor all copies of and media bearing the Software within 10 business days; (ii) delete and erase any copy of the Software copied onto any computer/server pursuant to this EULA; (iii) erase all backup and archival copies of the Software; and (iv) certify in writing to Licensor within ten (10) business days of the termination of this EULA that all copies of the Software have been returned to Licensor or have been erased. You further authorize Licensor, in the event of termination of this EULA, to remotely and/or electronically disable, delete and/or remove the Software from your computer(s), server(s), and system(s). Termination of this EULA shall not limit either party from pursuing other remedies available to it, including injunctive relief, nor shall such termination relieve you from your obligation to pay fees accrued prior to the termination.
MISCELLANEOUS:
If applicable and unless overridden by a separate agreement, this EULA is incorporated into the agreement you have reached with Licensor for the Software, and in the event of any conflict between the terms of such agreement and this EULA, the terms of this EULA shall prevail and govern.
You acknowledge that the Software is of U.S. origin. You agree to comply with all applicable international and national laws that apply to the Software, including the U.S. Export Administration Regulations, as well as end-user, end-use and destination restrictions issued by the U.S. and other governments.
This EULA is governed by the laws of the State of North Carolina. This EULA may only be modified by a writing signed by both you and Licensor.
Disputes concerning or arising out of this EULA shall be submitted to confidential binding arbitration in Greensboro, North Carolina before the Judicial Arbitration and Mediation Service (“JAMS”) pursuant to the Streamlined JAMS Arbitration Rules and Procedures. Each party hereto submits to the jurisdiction of JAMS at the location so indicated above. Any process served in connection with any proceeding arising out of or relating to this EULA may be served upon the party to be served by registered or certified mail at the address listed above. Any such service will have the same effect as personal service within the states so indicated above. The foregoing shall not preclude any party hereto from seeking enforcement outside the relevant state of the arbitration of any order or judgment rendered by any court upon the JAMS award.
Except as expressly provided in this EULA, no amendment or waiver of this EULA shall be binding unless executed in writing by the Customer and Licensor. No waiver of any provision of this EULA shall constitute a waiver of any other provision nor shall any waiver of any provision of this EULA constitute a continuing waiver unless otherwise expressly provided.
If any provisions of this EULA shall for any reason be held illegal or unenforceable, such provision shall be deemed separable from the remaining provisions of this EULA and shall in no way affect or impair the validity or the enforceability of the remaining provisions of this EULA.
This EULA constitutes the entire agreement between the parties pertaining to the subject matter hereof. There are no warranties, conditions, or representations (including any that may be implied by statute) and there are no agreements in connection with such subject matter except as specifically set forth or referred to in this EULA.
Should you have any questions concerning this EULA, or if you desire to contact Licensor for any reason, please send a written communication to: rsmith@montereytechgroup.com.
4.5. Annual Support and Maintenance Terms and Conditions
Coverage
Purchase of an Annual Support and Maintenance Agreement (Agreement) covers:
- Updates. Availability announcements of updates are sent to the email address on the Certificate.
- Technical support (excluding consulting). Support is initiated by creating a ticket in our support portal. Subsequent phone or web conferences will be arranged as deemed necessary by our support. Licensee may be asked for certificate number before being provided support.
- Support is available 9am-5pm Eastern US time Monday – Friday.
- 24 hour response time during normal business hours. Failure: 1 month of PSM refunded for each day missed. If not solved within 48 hours, customer can request to escalate the issue to LOGbinder's Development Triage Team who will classify the issue as:
- LOGbinder product defect
- Environment specific issue
- Microsoft product defect
Regardless of the classification we will make our best effort to solve or create a work around at which time a case-specific patch or product update will be provided. (To date we've only classified one issue as environment specific and we solved it in the next release of the software.)
- Credit towards the purchase of a higher-level license and Support and Maintenance Agreement (e.g. when you upgrade from WSS to Enterprise, etc.). This includes the original software cost and the unused portion of this Support and Maintenance Agreement (pro-rated and applied to the maintenance fee for the higher-level license).
Pricing
Annual Support and Maintenance Agreements can be purchased in 1, 2 or 3 year increments.
| Years | Amount |
| 1 | 20% of software list price |
| 2 | 38% of software list price |
| 3 | 54% of software list price |
Terms and Conditions
Renewal: We will email the technical contact and business contact we have on record at least 30 days prior to expiration to arrange renewal. (We will likely begin reminding you 90 days before expiration as well as send a fax to your main office.) Unless you renew, this Agreement automatically expires on midnight of the expiration date.
The cost of the Support and Maintenance Agreement will be based on the list price of the software at the time of the purchase. After that period, the cost to renew the Support and Maintenance Agreement will be based on the list price of the software at the time of each renewal.
Please note that lapses in Support and Maintenance Agreements are not allowed. In the case where a Support and Maintenance Agreement expired, any future renewals of said agreement will begin on the day following the original expiration date.
Cancelation: The Agreement can be canceled at any time in writing by e-mail, fax or letter. In case of cancelation, Monterey Technology Group, Inc. will not pro-rate or issue any refunds for any unused time on this agreement.
4.6. Whitepapars, Webinars and SIEM Integration Resources
Click here for various resources about LOGbinder for SharePoint.
4.7. Events Generated
Click here for a list of events generated by LOGbinder for SharePoint.
