Home → Supercharger KB → Printer Friendly Version
Supercharger KB
- 1. WEC and Supercharger 101
- 2. Getting Started
- 2.1. Installing Supercharger
- 2.2. Adding a Collector to Supercharger
- 2.3. Create a Subscription
- 2.4. Audit Policy for Active Directory Changes
- 2.5. Configuring Email Alerts and Reports
- 2.6. How To Purge Kerberos Ticket via Group Policy using Klist
- 2.7. Troubleshooting a Problem Forwarder
- 2.8. Granting Permissions for Security Log Forwarding
- 2.9. Install Supercharger with Splunk Free and the Splunk App for LOGbinder
- 3. Functionality
- 3.1. Subscriptions
- 3.2. Subscription Policies
- 3.3. Forwarder Analysis
- 3.4. Collectors
- 3.5. Collector Policies
- 3.6. Domains
- 3.7. Managed Filters
- 3.8. Pruning Old WEC Sources
- 3.9. Performance Monitoring
- 3.10. Health and Alerting
- 3.11. Troubleshooting
- 3.12. Security
- 3.13. Overrides
- 3.14. Licensing
- 3.15. Event Logs
- 3.16. Stalled Subscription Watchdog
- 3.17. Stalled Event Log Watchdog
- 3.18. Continuity Tracing
- 3.19. EPS Tracking
- 3.20. Configuring Supercharger for Entra
- 4. Resources
- 5. How To
- 5.1. How to Find Frequently Ran EXEs Causing Event ID 4688 Noise
- 5.2. Collecting Process Start Events (4688) Without the Noise
- 5.3. After installation Supercharger displays "Please provide credentials to an existing Supercharger database or location where a new Supercharger database will be created"
- 5.4. Customer Installed SQL Server
- 5.5. Collecting PowerShell Logs
- 5.6. All subscriptions have 0 active forwarders; System Event IDs 10128, 10129
- 5.7. How to Keep Subscriptions in Healthy State Even Though Some Workstations Are Shut Down Outside of Work Hours
- 5.8. How To Use LDAP Filters in Deterministic Subscription Policies
- 5.9. Controlling Which Computers Subscribe to a WEC Subscription
- 5.10. How To Backup and Restore Supercharger for Disaster Recovery
- 5.11. Ports used by Supercharger
- 5.12. Troubleshooting Load Balanced Subscriptions
- 5.13. Subscriptions are inactive
- 5.14. WinRM says "Unable to check the status of the firewall"
- 5.15. Using HTTPS with Windows Event Forwarding and Supercharger
- 5.16. Overriding global settings
- 5.17. How To Setup Supercharger Web GUI for HTTPS
- 5.18. KerbPurge 101
- 5.19. Eventlog-ForwardingPlugin Event ID 102 Error 5004 - subscription can not be created
- 5.20. How to use a different user if already logged in with SSO
- 5.21. How to Install SQL Express manually with Supercharger
- 5.22. High Availability with Supercharger
- 5.23. How to analyze where events are coming from and how many
- 5.24. Why we don't use the global catalog or support domain-crossing for deterministic forwarder analysis or load balanced subscriptions
- 5.25. How to fix SqlException: Execution Timeout Expired errors
- 5.26. Load Balancing with Jumbos
- 5.27. How To Upgrade Supercharger
- 5.28. HTTP Error 500.31 after installation
- 5.29. Migrating Supercharger to Another SQL Server
- 5.30. How To Configure Windows Server Core as a WEF Collector in Supercharger
- 5.31. How to install Supercharger Manager on Windows Server Core
- 5.32. Configure Cross Domain Forwarding
- 5.33. Delete a Corrupted Custom Event Log
- 6. Most Used
- 7. FAQ: Frequently Asked Questions
1. WEC and Supercharger 101
1.1. Windows Event Collection
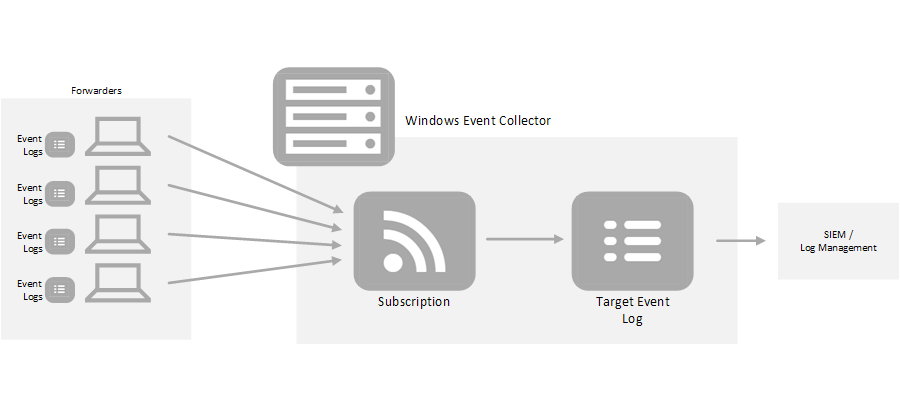
If you are already familiar with native Windows Event Collection (WEC) feel free to skip ahead to the next article. This documentation includes many visuals so here is a legend to how we consistently represent different objects:
Windows Event Collection gives you an agent-less way to efficiently collect events from thousands of Windows computers. A given Windows server is the Collector. Other computers forward specified events to a target event log on the Collector.
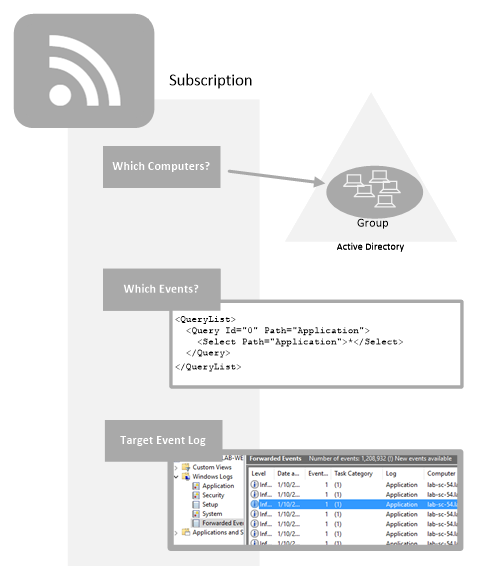
As you can see above, the Windows Event Collector server allows you to define one more Subscription objects. Subscriptions determine which Event Logs should be forwarded (and which events within those logs), which computers the subscription applies to and which event log on the Collector should receive the forwarded events.
You can define which events should be forwarded using the filter dialog in Event Viewer or with the XML query you see above for more advanced filters. The filter above simply gets all events from the Application log of the computers (forwarders) assigned.
The illustration above shows that you can use groups from Active Directory to define which computers should be forwarders for the Subscription. But you can also assign computers directly to a subscription which takes affect immediately. When you assign computers via groups, it can take days or weeks before the computer subscribes because a computer only updates its group membership when it is rebooted or you run klist. Supercharger's load balanced subscriptions feature eliminates this problem.
At any rate, all the computers you specify directly or via groups (including members of nested groups) are assigned to the subscription.
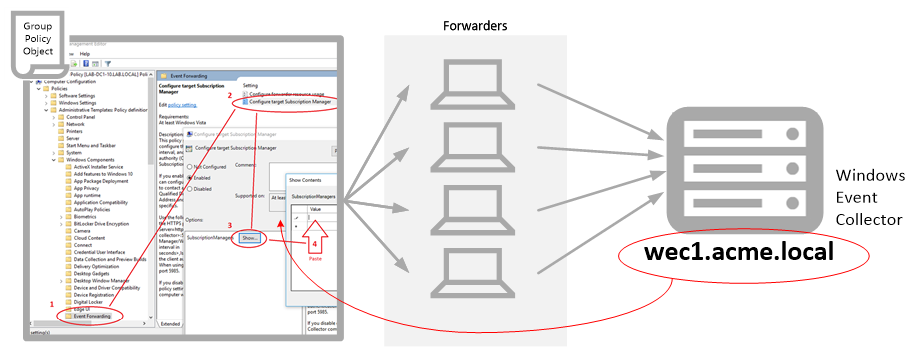
However just because a computer is in that group, it won’t start sending events yet. That’s because computers in the domain aren’t aware of your Collector automatically. You must use Group Policy to add your Collector as a Subscription Manager by going to:
Group Policy Management Editor\Default Domain Policy\Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding\Configure target Subscription Manager setting Enabled
1.2. Supercharger Architecture - Physical
Supercharger requires one server to be designated as the Manager and an agent (aka “Controller”) runs on each of the Windows Event Collectors. The Manager comprises
- Web application through which you interact with Supercharger and manage Windows Event Collection across your environment
- Controller Service – Which provides centralized management of the Supercharger installation as well as management of any local Subscriptions if the Manager is also a Collector
- SQL Express Database – Installed and managed by Supercharger
For smaller environments, it is possible to run the Manager on one of your Windows Event Collectors. Certainly, if you only have one Collector then simply use it as your Supercharger Manager. The Manager automatically includes the necessary agent for managing local Subscriptions.
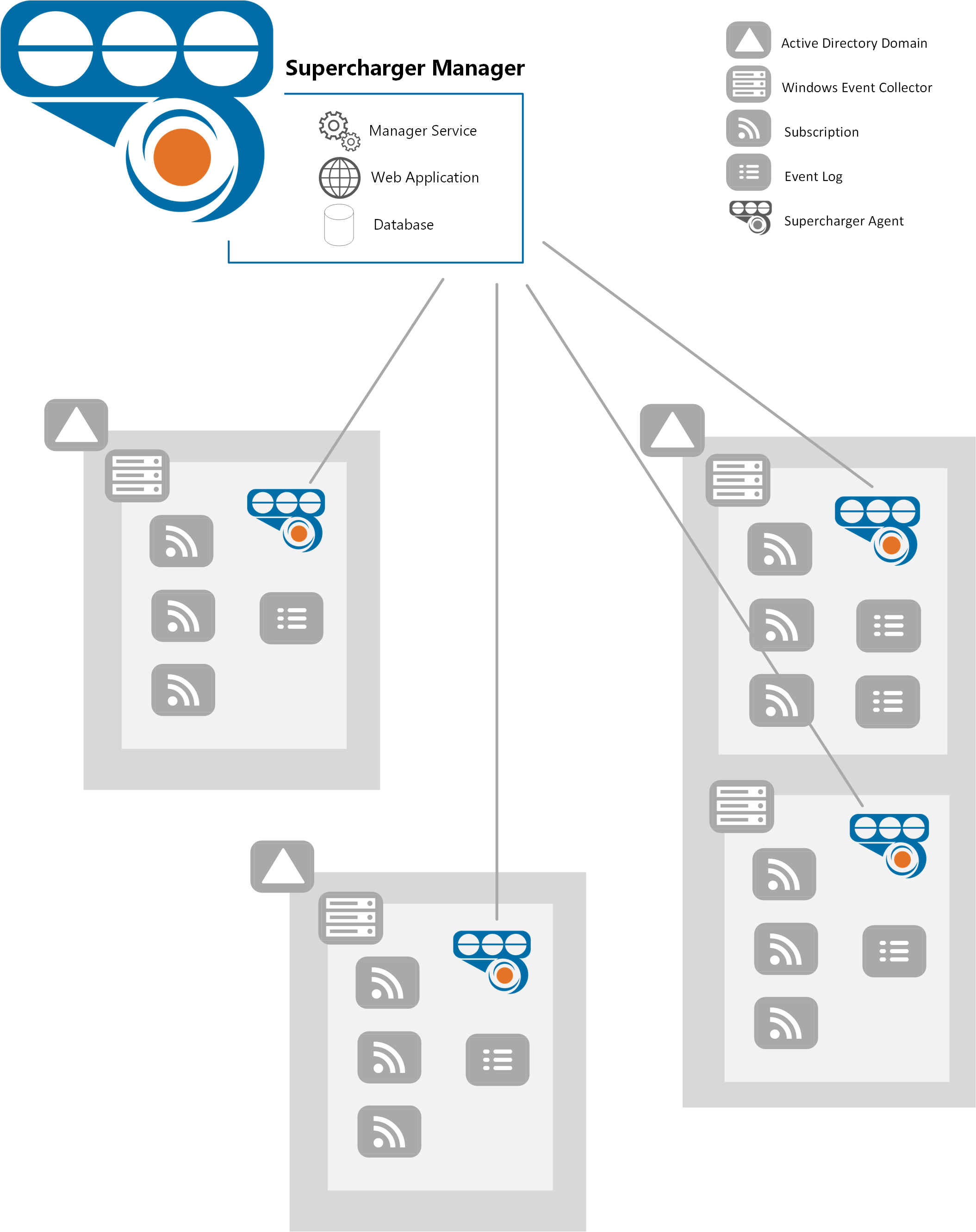
In the example below, there are 3 different Active Directory domains. One domain has 2 Collectors while the other domains each have one Collector. The Supercharger Controller (aka Agent) is installed on all 4 collectors and a 5th computer is the Manager. Supercharger supports multiple domains and no trust relationship is required; one Manager supports Collectors from multiple, unrelated domains without dependency on Forest or trust topology.
Here’s a screen shot of the dashboard for showing 2 domains, collectors and a load balancer with a load balanced subscription.
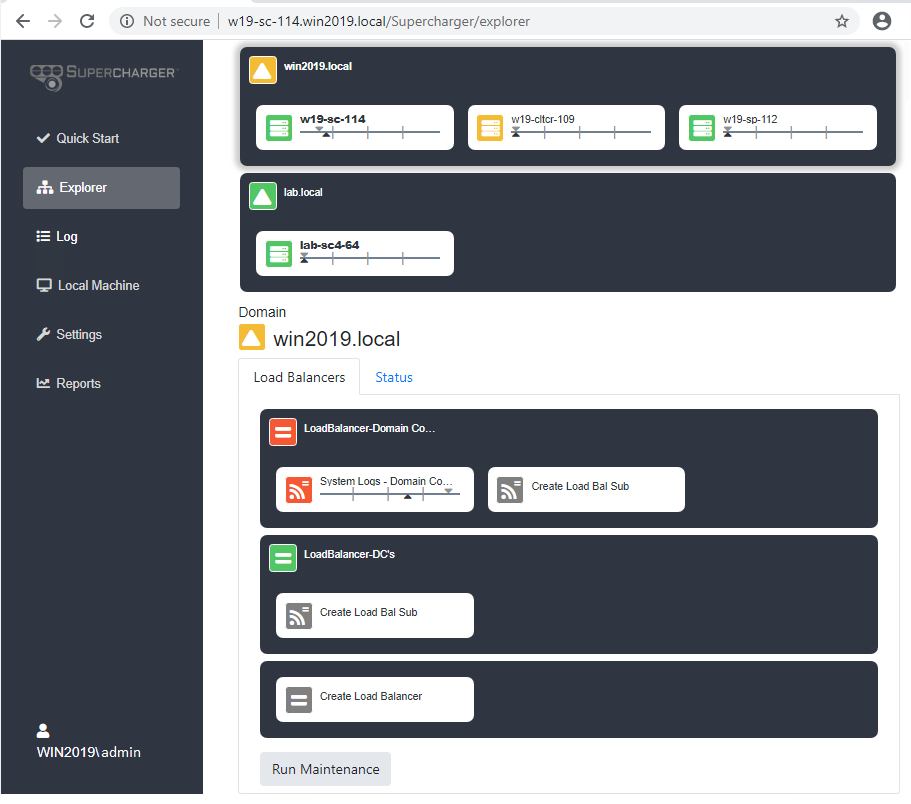
When you download Supercharger from our website, what you get is the Manager installer. Once you install the Manager, the easiest way to install the Controller (aka Agent) on each Collector is just logon to that Collector, open Supercharger with your browser and download the Controller installer as described here.
1.3. Supercharger Architecture - Logical
Supercharger’s logical architecture is centered around WEC subscriptions and the Windows servers (aka Collectors) that host them. Other Supercharger objects include Collector Policies, Subscription Policies and Managed Filters.
In the above example, we have 2 Active Directory domains. The first domain has 1 Collector and there are 2 Collectors in the other domain.
Above, you’ll notice 4 types of objects in Supercharger:
- Collector Policies allow you to define values for the many different configuration settings WEC provides at the server level. You can assign a given Collector Policy to multiple Collectors and be sure they are all configured consistently. There is a Default Collector Policy which comes with Supercharger out of the box. You can define additional Collector Policies that
- Subscription Policies are like Collector Policies but at the Subscription level. Both Supercharger and WEC have a number of settings on Subscriptions that determine how the subscription works in WEC and how Supercharger handles it as well. You can configure these settings as a Subscription Policy and assign that policy to each subscription across your environment that needs to be configured the same way.
- Managed Filters One of the most powerful features of Windows Event Collection is its ability to define advanced filters that define exactly which events you want to forward – and those that are just “noise” and should be left behind. But building these filters requires specialized knowledge of XML query syntax and of the event logs you are collecting. Supercharger helps you build powerful filters whether you know XML query and we provide special help for the Security Log thanks to our relationship with UltimateItSecurity.com. Managed filters are where you find these capabilities. Once you build your filter you can assign it to multiple subscriptions without duplicating it.
- LDAP Queries Supercharger allows you to use custom LDAP queries to specify a set of forwarder computer accounts from AD using any query-able property from AD. This object type allows you to re-use a given LDAP query in multiple places.
The forwarders are not shown. By the way, technically, forwarders can cross domain boundaries and send events to Collectors elsewhere in the forest but we don’t recommend it nor does Supercharger fully support forwarders crossing domains. But as we said earlier, Supercharger fully supports multiple domains with no dependencies on trust or forest topology. It’s just best to avoid assigning forwarders to Collectors outside their domain.
The other important dimension of Supercharger’s logical architecture is Load Balanced Subscriptions. If you have a large environment with thousands of forwarders you’ll especially want to read this.
1.4. Load Balancing Many Forwarders Across Multiple Collectors
What if you have tens of thousands of workstations or hundreds of servers that simply produce more events than one Collector can keep up with? Supercharger’s Enterprise functionality can automatically distribute and balance this load across multiple controllers with a feature called Load Balanced Subscriptions.
A Load Balanced Subscription is like a normal Subscription in WEC but you create it in Supercharger at the domain level and then Supercharger creates actual WEC subscriptions on collector as necessary with an equal portion of computers to each collector.
Load Balancer
Inside a given domain, you first create an object called a Supercharger object called a Load Balancer which is made up of 2 lists
- The Collectors among which Supercharger should distribute the load of forwarders
- The Cohort of Forwarders that should be evenly distributed among the Collectors. This set of computer accounts from AD is called the Cohort. You can define using either an AD group or with and LDAP query. Supercharger will find all the computers in that group or LDAP query and they become the Cohort. Supercharger takes into account each computer's status in AD (is it enabled? is it dormant?) and assigns an even number to each collector. As the word implies, the cohort should be a fairly homogeneous set of similar computers that would be expected on average to produce a like number of events.
Load Balanced Subscriptions
But wait, all we've defined is a set of Collectors and a cohort of Forwarders. What about specifying which Event Logs and which events in those logs you need to collect? That's where the next object type, Load Balanced Subscriptions, come in. Load Balanced Subscriptions are child objects of a Load Balancer.
For a given Load Balancer you can create one or more Load Balanced Subscriptions which comprise
- Managed Filter - a Supercharger object that specifies which event logs and events to collect. More info
- Subscription Policy - a Supercharger object that specifies all the WEC settings for a subscription. For Load Balanced Subscriptions, Supercharger only displays Deterministic policies. More info
- Destination Log Name - this log must be present on each collector in the Load Balancer but Supercharger helps you manage this
Here is an overall diagram showing the relationship of Load Balancers, Load Balanced Subscriptions and the actual Collectors and Subscriptions in Windows.
2. Getting Started
2.1. Installing Supercharger
When you download Supercharger from our website, you get the Manager installer. Where should you install the Manager? It depends on how many Collectors you expect to have.
How Many Collectors?
One collector can usually handle thousands of forwarders. If this is an evaluation or you only plan to have one Collector, then you should probably just install the Manager on that one Collector. For more information check out the physical architecture article.
If you have multiple collectors we recommend dedicating your a modest sized VM as the Supercharger manager.
Simply run the downloaded installer on a domain server as a domain user who is in the local administrators group on the server that will be the central server for managing all your Collectors.
If you need to install Supercharger on a server that has ever had SQL Server 2016 installed please contact support first.
If necessary, the installer will first install the .NET Framework. Then it will install an instance of SQL Server Express. After those prerequisites, it will configure IIS to host the Supercharger web application which is the user interface for Supercharger. Finally, it will install the Controller service which, on the Manager, provides background management of the overall Supercharger environment and also allows you to manage local subscriptions if desired.
After installation
You, the installer, will automatically be added to the Administrators role in Supercharger. You can add more users to the various roles later in the Settings/Security area of Supercharger.
Once the manager is installed it will start your web browser and open Supercharger’s dashboard. You will see the current domain and the local server will show up as a Collector. If you’ve already created any Subscriptions on this server in WEC manually, they will show up in a few seconds if you expand the Collector tile. You can open the viewers for the domain, Collector, Subscriptions and Event Logs to see their details or to make changes.
Do you have other Collectors?
Just remote desktop in to those Collectors and then direct the local web browser back to the Supercharger web site. Its URL is the DNS name of the manager plus “/supercharger”. So if your manager is wecmgr.acme.local then direct your browser to http://wecmgr.acme.local/supercharger. If the Collector is in the same domain and you are logged into it as the same account as when you installed the Manager your authentication will probably be automatic. Otherwise you’ll be prompted for credentials of a user in the Manager’s domain who has been assigned to one of the roles within Superchargers Settings/Security page.
Once you are logged into Supercharger from the new Collector, click on Local Machine and download the Controller (agent) installer. You will be prompted the 2 data that are displayed on this page: 1) SQL Server DNS name – this is the same as the Manager, and 2) the Authenticator – this a security key changed every 24 hours that is part of the security controls Supercharger enforces to prevent rogue Controllers.
After you provide this information to the installer, the rest is automatic. Soon you should see the new Collector show up on the dashboard where you should approve it. After approval, within a short while a new tile will appear for the Controller and you’ll see any pre-existing Subscriptions or you can create a new one.
2.2. Adding a Collector to Supercharger
To add a new collector to Supercharger:
- Open Supercharger and go to the "Local Machine" tab.
- If you do this step on the server that you want to add, the next step will be somewhat easier, but it is not a requirement. You can open Supercharger from any server by navigating to the address of the Manager server, for example, http://managerserver.domain.local/supercharger
- If you do this step on the Supercharger manager or another server, you will just have to copy the installer to the server that you want to add.
- Please do not use Internet Explorer. Instead, use Edge, Chrome, Firefox etc.
- Click on the "Download and launch collector installer" link to download the installer.
- Run the downloaded installer on the server you want to add.
- The installer requires the two pieces of information provided in step 2 above. Click the "Copy To Clipboard" button and paste the SQL Server DNS name in to the installer. Do the same for the Authenticator code. Click Next to Install.
- Once the installer is complete, navigate back to the Manager URL in the browser and click on the "Explorer" tab on the left. In about less than a minute you should see the new collector pop up with Approve or Deny buttons. Click on Approve.
- Click on "OK" on the confirmation message.
- The new collector is now added and should turn green once all of the preliminary checks are complete.
2.3. Create a Subscription
This is a step-by-step article. For important background please review the Getting Started articles first – especially the overview of Windows Event Collection.
1. Choose your Windows Event Collector
Select a Windows server running Windows Server 2008 R2 or above to be your Windows Event Collector. Install the Supercharger Controller Service (aka Agent) on that server. Supercharger will enable Windows event collection automatically.
2. Target Computers at the Collector
Computers in your domain need to know about the new collector. Use group policy to accomplish this.
Select a group policy object that will be applied to all the computers that may potentially need to forward events to the collector. It’s OK to target more computers at a collector than will actually be sending events. Unless you have specific reasons to use a more narrow scope, edit your Default Domain Policy GPO so that all computers in the domain are targeted at your collector.
First though you need a specially formatted string for each collector. Supercharger will automatically build this string for you. Just open the Domain’s viewer dialog from the dashboard to access the Target Subscription Manager string for each Collector in your domain. If you have multiple collectors you will usually want to add each to the group policy setting.
The screen shot below shows the exact “Configure target Subscription Manager” setting in group policy where you should add the above collector strings. It can be found under Group Policy Management Editor\Default Domain Policy\Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding.
At this point, as computers apply group policy, and if WinRM is configured on them (see next step), they will begin to regularly check in with the specified collectors to find out if any subscriptions apply to them. Computers will check based on the Refresh interval specified in the controller string. By default Supercharger sets this to every 900 seconds.
3. Configure Computers for Event Forwarding
More recent versions of Windows are automatically configured to forward events once you complete the earlier steps. But be aware that that the WinRM service must be running and configured to automatically start. In addition depending on the version and flavor of Windows on a given forwarder (aka WEC source) it may be necessary to run “winrm qc” or accomplish the same via group policy (see http://www.grouppolicy.biz/2014/05/enable-winrm-via-group-policy/).
Security Log Specific Concerns
Is this subscription intended for collecting the Security Log? If so there is an additional configuration requirement on forwarder computers. The security log has more restrictive permissions than other event logs and by default the WinRM service cannot access it. See Granting Permissions for Security Log Forwarding
4. Select your Forwarders
Next you need to select an existing or create a new group in Active Directory whose members correspond to the computer accounts that should forward events. If you already have a group in AD with the right computer accounts, there’s nothing else to do in this step. You’ll use this group in the next step when you create the subscription.
Group Membership Doesn’t Take Effect Until Reboot
When you add a computer as a member of a group, the change does not take effect until you reboot the computer. A common problem with Windows Event Collection arises you make a computer a member of a group, configure the subscription with that group and then target it at the collector. The computer does not start sending events because it’s Kerberos ticket was built prior to the group membership change. You must either
- run klist -lh 0 -li 0x3e4 purge which purges the Kerberos tickets. https://blogs.technet.microsoft.com/tspring/2014/06/23/viewing-and-purging-cached-kerberos-tickets/
- reboot the computer so that it’s Kerberos ticket is recreated.
Group Policy vs. Group Membership
It’s important to understand the relationship of this group to the scope of computers that apply the group policy you configured earlier. Only those computers that are targeted at the collector via the group policy object AND belong to the Active Directory group you select in this step will become forwarders on that subscription.
5. Create the Subscription
On the Dashboard in Supercharger, click the Add Subscription tile under that appropriate collector.
On the first page of the wizard you will need to select the destination event log. This is NOT the event log you are collecting events from on forwarders. It is the event log on the collector that will receive events. Out of the box, Windows only supports using the Forwarded Events log to receive events. In the future we plan to add this capability to Supercharger. If you need to create additional destination logs contact support.
Next select a Subscription Policy. Subscription Policy controls advanced WEC configuration settings for the subscription and how Supercharger will assess the health of the subscription. Read more here.
On the Allowed Forwarders dialog add the group you selected in the previous step. When computers targeted at this collector next check-in, Windows will see they are a member of this group and they will connect to this subscription.
On the Filters page you can either enter a raw XML log filter or select one of the managed filters. This defines which logs on source computers and which events within those logs will be forwarded.
Create the subscription. The web application submits the command to the collector and within a minute you should see the new subscription appear in the dashboard.
6. Look for Current Forwarders
At this point you will want to open the new subscription and select the Current Forwarders tab.
Many things influence how long it takes for forwarders to show up including
- How long ago you configured group policy to target computers at this collector
- How long ago you created the group and added the source computers as members
- How many domain controllers and sites exist in the domain as well as the replication schedule
- If computers have rebooted since you changed group membership
- If WinRM is started on the source computers
- But the biggest influencer is the Refresh interval specified in the collector string in step 2
Arbitrary and Empirical
If the subscription policy you selected is Arbitrary or Empirical you will see computers appear as they check in with the collector and see the new subscription. Such computers will immediately show up as Healthy.
Deterministic
If the subscription policy you selected is Deterministic, then as soon as the Forwarder Analysis command completes (automatically submitted when you create a subscription) you should see all the computers in the group you specified for this subscription. If Current Forwarders doesn’t populate yet after Forwarder Analysis completes it is likely because the domain you created the group on has not replicated to the domain controller queried by the collector. Time will resolve this.
Most if not all of these computers will initially show up as Problem status in the Health column and Absent in the WEC column. But as these computers individually check in with the collector and discover the new subscription to which they are assigned their health status will change to Healthy and their WEC status to Active. You may also see some computers as Ignore health status because of their computer account in Active Directory. For more information see Health Assessment Basis at Subscription Policies.
To diagnose forwarders that refuse to send events see Troubleshooting a Problem Forwarder.
2.4. Audit Policy for Active Directory Changes
Here is the minimum audit policy necessary to enable on domain controllers in order to generate all of the events included by the “Builtin - Security: Active Directory Changes” managed filter and needed by the Splunk App for LOGbinder if you are using that.
In the Default Domain Controllers Policy GPO make the following changes
|
Path |
Policy |
Setting |
|
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options |
Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings. |
Enabled |
|
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration |
Security System Extension Authorization Policy Change Authentication Policy Change Audit Policy Change User Account Management Security Group Management Other Account Management Events Other Policy Change Events Directory Service Replication Directory Service Changes |
Success (Its ok to include Failure but most of these categories don’t log any failures) |
You still need to configure other group policy settings to ensure your domain controllers connect to your collector and that winrm can access the Security Log. See
2.5. Configuring Email Alerts and Reports
To configure Supercharger to send alerts and reports, click on Settings and then the Email tab in the Manager and configure the following settings:
Email From Address: This is the email address that will be displayed as the sender in the alert and report emails.
Smtp Server: Enter the name of the mail server, for example, smtp.domain.com or smtp.gmail.com.
Smtp Port: Leave as default port 25 unless you are using TLS. (See next setting)
Smtp Use Tls: If TLS will be used check this box and change the above "Smtp Port" to 587.
Smtp Use Default Credentials: If this checkbox is enabled, Supercharger will attempt to login to the SMTP server with the service accounts username and password.
Smtp User Name: Enter a valid account name that can login to the mail server.
Smtp Password: Enter the password the "Smtp User Name" above.
Status Report Enabled: If this checkbox is enabled, Supercharger will send status reports at the specified times in the schedule below.
Status Report Email Recipients*: Enter the email address of the account that will receive Supercharger status reports. If left blank, all users and groups on the "Security" tab under Settings will be emailed.
Status Report Schedule: The default schedule is [7] which corresponds to 7AM. This setting uses a 24-hour format and you can send status reports at any time. For example, in the screenshot below, with the schedule [0, 8, 17] reports will be sent at midnight, 8AM and 5PM.
Alert Emails Enabled: If this checkbox is enabled, Supercharger will send alerts as they happen in the Manager.
Alert Email Recipient*: Enter the email address of the account that will receive Supercharger alerts. If left blank, all users and groups on the "Security" tab under Settings will be emailed.
Submit Changes: Clicking on this button will save the above changes to the settings.
Send Test Email: Clicking on this button will send a test email to the Report and Alert email recipients.
2.6. How To Purge Kerberos Ticket via Group Policy using Klist
NOTE: This article is applicable not only to WEC/WEF but also for normal Active Directory use when you want to force a computer to see that it has been added to a new group.
Our recommendation is to add forwarding endpoints in to an AD group and then add that group to the Allowed Forwarders in your subscription settings in Supercharger. It's much easier to manage a group with thousands of endpoints than to manage endpoints individually. The problem is a delay in AD. When a computer is added to a group in AD it doesn't know that it's been added until one of two things happen:
1. The computer is rebooted
2. The Kerberos ticket cache is cleared, which does not require a reboot.
Below are the steps to perform the clearing of the Kerberos ticket cache via Group Policy so that this does not have to be performed manually on each endpoint.
1. In Group Policy Management, right click on the target GPO and select "Edit".
2. Navigate to Computer Configuration\Preferences\Control Panel Settings\Scheduled Tasks
3. Right click and select "New" and then "Immediate Task (At least Windows 7)".
4. Name the task.
5. Click on "Change User or Group" and make sure "From this location" is using the correct domain. Type "system" in the name box and then click on "Check Names".
6. Make sure SYSTEM is selected and click "OK".
7. You should now have "NT AUTHORITY\System" as the user account. Also make sure "Run whether user is logged on or not" and "Run with highest privileges" are both selected.
8. Click on the "Actions" tab and select "New...". Enter "%systemroot%\system32\klist.exe" in the Program/script box. Add "-lh 0 -li 0x3e4 purge" in the "Add arguments(optional)" box. Click "OK".
9. Click on the "Common" tab and check "Apply once and do not reapply." and "Item-level targeting." Then click the "Targeting..." button.
10. Click on the "New Item" dropdown and select "Date Match".
11. Select "On date" in the dropdown and use today's date.
12. Click "OK" and click "OK" again to create the task.
13. The task will now be applied on the next Group Policy update.
TIP - If your domain controller is running on Windows 2012 R2 you should be able to right click on the OU in Group Policy Management and tell the DC to run a Group Policy Update.
2.7. Troubleshooting a Problem Forwarder
Problem: A computer shows up in the Current Forwarders tab for your subscription but is shown as None in the WEC column.
This means that your subscription’s policy’s health assessment basis is Deterministic and that the group(s) you’ve assigned in Allowed Forwarders include this computer as a member. Therefore we expect it to be forwarding events. Yet, WEC has never seen that computer for this subscription and therefore Supercharger reports Absent.
Here are the possible reasons why, with tips on how to investigate
|
Category |
Problem |
Action on Forwarder |
|---|---|---|
|
Collector targeting |
Forwarder is not targeted at collector |
Run a Group Policy Results report for that computer
|
|
Collector string for “Configure target subscription manager” is incorrect |
Are other computers successfully targeting this collector via the same group policy object? Check Microsoft-Windows-Forwarding/Operational (Microsoft-Windows-Eventlog-ForwardingPlugin/Operational) on forwarder for errors (see below) |
|
|
Group policy recently updated and forwarder has not applied or GPO has not replicated |
Run gpupdate on forwarder and verify with Group Policy Results report “GPRESULT /H GPReport.html” and check “Configure target subscription manager” |
|
|
Connectivity |
Connectivity problem |
Use this command with the DNS name in your collector string “winrm identify -r:http://winrm_server:5985” (or “winrm identify -r:https://winrm_server:5986”) |
|
WinRM on Forwarder |
Check these event logs for errors:
|
Event ID 102 with error 5004 can mean
Event ID 105 with error 2150859027 with full message "The forwarder is having a problem communicating with subscription manager at address http://COLLECTOR:5985/wsman/SubscriptionManager/WEC. Error code is 2150859027 and Error Message is <f:WSManFault xmlns:f="http://schemas.microsoft.com/wbem/wsman/1/wsmanfault" Code="2150859027" Machine="FORWARDER"><f:Message>The WinRM client sent a request to an HTTP server and got a response saying the requested HTTP URL was not available. This is usually returned by a HTTP server that does not support the WS-Management protocol. </f:Message></f:WSManFault>.
|
|
WinRM service not running on forwarder |
||
|
WinRM has not been configured on forwarder |
Run “winrm qc” |
|
|
Collector |
Collector side problem |
Check following logs
|
| WinRM issue on Collector |
Run "winrm get winrm/config". In the results of this cmd is "AllowRemoteAccess = true". Check HKLM\Software\Policies\Microsoft\Windows\WinRM\Service
|
|
|
Active Directory |
Computer was recently added/removed from group and Supercharger collector and source computer are talking to different domain controllers |
Force replication between domain controller if practical |
|
Computer has not been rebooted since being added to the group |
Reboot or Run this command on the forwarder: klist -lh 0 -li 0x3e4 purge This purges the Kerberos ticket cache and the computer will pick up the new group when it obtains a new ticket. See this article for steps to perform this. |
2.8. Granting Permissions for Security Log Forwarding
If your subscription collects events from the Security Log you must configure permissions on all forwarder computers to all the WinRM service read access. WinRM runs as NETWORK SERVICE so that’s who we’ll be granting access to. There are 2 ways to do this via group policy. We recommend the first so that you can avoid rebooting forwarders.
Option 1: Configure Log Access
Enter the following string into these 2 group policy settings. The portion in bold is what is being added to the default permissions preceding it.
O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;NS)
Option 2: Membership in Event Log Readers
Note: this requires reboot of the forwarder computer
Add NETWORK SERVICE to the Event Log Readers local group using Restricted Groups policy
2.9. Install Supercharger with Splunk Free and the Splunk App for LOGbinder
Note: Select a computer to run Supercharger and Splunk
Installing and Configuring Supercharger
Create Custom Log for Domain Controller Forwarded Events
Create a Subscription to Forward Domain Controller logs
Preparing Active Directory
Group Policy
Add Collector as a Targeted Subscription Manager
Configure Permissions for Security Log Access on Domain Controllers
Active Directory Users and Computers
Configure Object Level Audit Policy
Install Splunk App for LOGbinder
Installing and Configuring Supercharger
Installing Supercharger
- Download Supercharger from LOGbinder.com.
- Run the installation file.
- Perform a default installation.
- For further information go to this Installing Supercharger KB article.
- The installer will install IIS if it is not installed and will reboot the server. The installation will resume upon login.
- Supercharger will automatically open the web browser upon completion of the installation.
***Please note that if your DC's are Win2008r2 then you will need to run "winrm qc" on each DC in an elevated cmd prompt.***
Create Custom Log for Domain Controller Forwarded Events
- Click on your collector in the dashboard.
- Click on the "Subscriptions and Logs" tab and then on the "Create Event Log" button.
- Configure the new event log and click "Submit".
- The log must be named ADChanges
- The log path can be customized
- The maximum log size can be customized but must be at least 511,967,232 bytes.
Create a Subscription to Forward Domain Controller logs
- On the "Subscriptions and Logs" tab click on the "Create Subscription" button.
- On the “Create Subscription” screen enter a name and description. Select the previously created log, “Supercharger-Destination-ADChanges/Log”. Select “Builtin Deterministic 100% for High Value Servers” from the “Subscription Policy” dropdown.
- Click on the “Add forwarder” button and then search for “domain controllers”. Select “Domain Controllers” in the “Results” window and then click “OK”.
- For "Subscription Filter" select "Builtin – Security: Active Directory Changes” from the dropdown then click “Submit”.
Preparing Active Directory
Group Policy
Add Collector as a Targeted Subscription Manager
- Connect to the Domain Controller.
- Right click on “Start” then run and run “gpmc.msc”.
- Expand the "Domain Controllers” OU and right click on "Default Domain Controllers Policy" and select “Edit"
- In Group Policy Management Editor, navigate to the following location: Default Domain Policy\Computer Configuration\Policies\Administrative Templates\Windows Components\Event Forwarding
- Double click on “Configure target Subscription Manager” on the right.
- Select “Enabled” and then click the “Show” button.
- Add the collector to the “SubscriptionManagers” list. This string can be found in Supercharger by clicking on "Quick Start" then expanding the "Configure potential source computers with Group Policy" section. Under #2 you will the collector strings syntax. Copy and paste this string. Do not copy the bullet point. Use the following syntax:
Server=http://<FQDN of the collector>:5985/wsman/SubscriptionManager/WEC,Refresh=900 where FQDN equals the “servername.domain.abc”.
Configure Permissions for Security Log Access on Domain Controllers
- Connect to the Domain Controller.
- Right click on “Start” then run and run “gpmc.msc”.
- Expand the "Domain Controllers” OU and right click on "Default Domain Controllers Policy" and select “Edit"
- Perform one of the two steps from this KB article: Granting Permissions for Security Log Forwarding
Audit Policy
- Connect to the Domain Controller.
- Right click on “Start” then run and run “gpmc.msc”.
- Expand the "Domain Controllers” OU and right click on "Default Domain Controllers Policy" and select “Edit"
- Navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options and in the list of options in the right window click on "Audit: Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings.”
- Set this setting to "Enabled" and click "Apply
- Next, navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies.
- Select the following policies and enable "Success"
- Account Management
- Audit Other Account Management Events
- Audit Security Group Management
- Audit User Account Management
- DS Access
- Audit Directory Service Changes
- Audit Directory Service Replication
- Policy Change
- Audit Audit Policy Change
- Audit Authentication Policy Change
- Audit Authorization Policy Change
- Audit Other Policy Change Events
- System
- Audit Security System Extension
- Account Management
Active Directory Users and Computers
Configure Object Level Audit Policy
- On the Domain Controller open "Active Directory Users and Computers.
- Right click on root of the domain and select "Properties".
- Select the Security tab and click on "Advanced".
- Select the Auditing tab and click "Add".
- Set Principal to "Everyone". Leave Type as "Success" and Applies to "This object and all descendant objects".
- Scroll to the bottom of the list and click on "Clear All". Scroll back to the top and select the following options:
Permissions\Modify Permissions
Properties\Write gPLink
Properties\Write gPOtions - Click "OK" and then click "Add" again.
- For this second entry set Principal to "Everyone". Leave Type as "Success". Set "Applies to: Descendant groupPolicyContainer objects".
-
Scroll to the bottom of the list and click on "Clear All". Scroll back to the top and select the following options:
Permissions\Write all properties
Permissions\Modify Permissions
Install Splunk Free
- Download Splunk Enterprise from splunk.com
- Run the installation file.
- Perform a default installation.
- Login to Splunk and change the default admin password.
- When the Splunk Enterprise license expires, the license will convert to a perpetual free license. You can also change this now by clicking on Settings then Licensing and changing the license group to Free.
Install Splunk App for LOGbinder
- Go to LOGbinder.com and click on the “Resources” tab and look in the “SIEM Integration Resources” section for the “Splunk App for LOGbinder”. Download, extract and save the file.
- Login to Splunk and click the Gear Icon next to Apps.
- Click on the “Install app from file” button.
- Browse to the file you saved in step 1 and then click the green “Upload” button.
Tips
Supercharger
1. Dashboards should begin to populate with data within 15 minutes usually.
2. Check Windows Event Collection
a. In Supercharger check the subscription. If it's yellow or red click on the subscription for an explanation.
b. After the Domain Controllers apply the updated Group Policy, the subscription should eventually go green.
c. Shortly thereafter, events will begin to show up in the ADChanges log in Event Viewer.
d. Remember that Domain Controller replication, application of Group Policy, Refresh Interval and Subscription settings can all introduce some initial latency.
3. This article provides extensive steps to troubleshoot problem forwarders.
4. To speed up the sending of events:
a. In Supercharger edit the Default Subscription Policy (Under Settings\Subscription Policies) and change the Configuration Mode setting to "MinLatency".
b. Also click on the Collector and run the "Collector Analysis" command.
c. Another option is to run gpupdate and restart the WinRM service.
Splunk
We are assuming that the Active Directory data will be either in the index=main (the defualt) or index=wineventlog (used by the Splunk for LOGbinder App). The second assumption is that the sourcetype will be WinEventLog:Security. So be sure to either set those when setting up new inputs or to change the props.conf and macros to accommodate the different values.
If the Active Directory dashboards are not populating you may wan to check the following:
1. Check which index the events are sending as by running this search:
index=* source="WinEventLog:Supercharger-Destination-ADChanges/Log" | stats count by index
The app expects the data to be in one of these indexes: index=wineventlog OR index=main. If it is indexed in some other index, then it can be added to this macro: select_winseclog_events
2. Check if the sourcetype is changed to WinEventLog:Security by running this search:
index=* source="WinEventLog:Supercharger-Destination-ADChanges/Log" | stats count by sourcetype
If that is not the case then props.conf should be copied to %SPLUNK_HOME%/etc/apps/logbinder/local and this should be added to it:
[source::WinEventLog:Supercharger-Destination-ADChanges/Log]
TRANSFORMS-change_host = WinEventHostOverride
EXTRACT-TargetAccountDomain = (?ms)^(New Logon|New Account|Target Account|Account Whose Credentials Were Used|Account For Which Logon Failed|Account That Was Locked Out):.+?(Account Domain|Old Account Domain):\s+(?<TargetAccountDomain>[^\v]+)
EXTRACT-ObjectDN = (?ms)^Object:.+?DN:\s+(?<ObjectDN>[^\v]+)$
EXTRACT-ObjectGUID = (?ms)^Object:.+?GUID:\s+(?<ObjectGUID>[^\v]+)$
EXTRACT-ObjectClass = (?ms)^Object:.+?Class:\s+(?<ObjectClass>[^\v]+)$
EXTRACT-DirectoryServiceName = (?ms)^Directory Service:.+?Name:\s+(?<DirectoryServiceName>[^\v]+)$
EXTRACT-DirectoryServiceType = (?ms)^Directory Service:.+?Type:\s+(?<DirectoryServiceType>[^\v]+)$
EXTRACT-MemberAccountName = (?ms)^Member:.*?Account Name:\s+(?<MemberAccountName>[^\v]+)
EXTRACT-SourceAccountName = (?ms)^Source Account:.+?Account Name:\s+(?<SourceAccountName>[^\v]+)EXTRACT-SubjectAccountName = (?ms)^Subject:.+?Account Name:\s+(?<SubjectAccountName>[^\v]+)
EXTRACT-TargetAccountName = (?ms)^(New Logon|New Account|Target Account|Account Whose Credentials Were Used|Account For Which Logon Failed|Account That Was Locked Out):.+?(Account Name|Old Account Name):\s+(?<TargetAccountName>[^\v]+)
EXTRACT-ChangedAttributes = (?ms)^Changed Attributes:(?<ChangedAttributes>.*)Additional Information:
EXTRACT-MemberSecurityID = (?ms)^Member:.*Security ID:\s+(?<MemberSecurityID>[^\v]+)
EXTRACT-NewTargetAccount = (?ms)^Target Account:.+?New Account Name:\s+(?<NewTargetAccount>[^\v]+)
EXTRACT-SubjectAccountDomain = (?ms)^Subject:.+?Account Domain:\s+(?<SubjectAccountDomain>[^\v]+)
EXTRACT-SubjectLogonGUID = (?ms)^Subject:.+?Logon GUID:\s+(?<SubjectLogonGUID>[^\v]+)
EXTRACT-SubjectLogonID = (?ms)^Subject:.+?Logon ID:\s+(?<SubjectLogonID>[^\v]+)
EXTRACT-SubjectSecurityID = (?ms)^Subject:.+?Security ID:\s+(?<SubjectSecurityID>[^\v]+)
EXTRACT-TargetLogonGUID = (?ms)^(New Logon|New Account|Target Account|Account Whose Credentials Were Used|Account For Which Logon Failed|Account That Was Locked Out):.+?Logon GUID:\s+(?<TargetLogonGUID>[^\v]+)
EXTRACT-TargetLogonID = (?ms)^(New Logon|New Account|Target Account|Account Whose Credentials Were Used|Account For Which Logon Failed|Account That Was Locked Out):.+?Logon ID:\s+(?<TargetLogonID>[^\v]+)
EXTRACT-TargetSecurityID = (?ms)^(New Logon|New Account|Target Account|Account Whose Credentials Were Used|Account For Which Logon Failed|Account That Was Locked Out):.+?Security ID:\s+(?<TargetSecurityID>[^\v]+)
EXTRACT-AttributeLDAPDisplayName = (?ms)^Attribute:.+?LDAP\sDisplay\sName:\s+(?<AttributeLDAPDisplayName>[^\v]+)$
3. Functionality
3.1. Subscriptions
When you open a Subscription’s viewer, Supercharger surfaces all attributes of the subscription in WEC as well as additional attributes Supercharger maintains about the subscription. You never need to resort to logging into the Collector and opening the subscription in Event Viewer. You can manage your entire Windows Event Collection environment from your PC or mobile device using Supercharger’s web interface. In fact, Supercharger exposes settings omitted from Event Viewer and only accessible via API or scripting.
That being said, Supercharger gracefully handles subscriptions created, modified or deleted outside of Supercharger. When you initially install the Supercharger Controller (aka agent) on a Windows event controller, the agent discovers any pre-existing subscriptions and creates their associated records in Supercharger. Thereafter, very 5 minutes or so Supercharger re-analyzes WEC and updates the manager with each subscription’s current state. This is all accomplished with the recurring CollectorAnalysisCommand command. If you wish Supercharger to re-analyze on demand just submit a ForwarderAnalysisCommand from the collector’s viewer dialog; the ForwarderAnalsyisCommand immediately triggers a CollectorAnalysisCommand.
When you modify a subscription in Supercharger, the change is submitted to the agent on that collector. After the agent updates WEC it immediately runs a CollectorAnalysisCommand and within seconds the changes are reflected in Supercharger. This cycle also ensures that Supercharger always reflects what’s the actual state of WEC with no danger of getting “out of synch”.
Subscription Viewer Dialog
When you click a Subscription's name on the dashboard Supercharger displays the viewer dialog for that subscription with the following tabs:
Overview
This tab displays description, status, status reasons, forwarder statistics and the subscription policy assigned. You can enable/disable the subscription, edit or delete it.
WEC
This tab displays the actual settings taken directly from the Windows Event Collection API for this subscription. Most of these settings controlled by Supercharger via the assigned subscription policy.
Current Forwarders
This tab displays all of the forwarders WEC reports as having ever forwarded events for this subscription. In addition, if the assigned subscription policy is Deterministic, Supercharger also includes any computer accounts from Active Directory that should be forwarding events but are not yet reported by WEC. See Forwarder Analysis to understand the status columns on this tab. Other columns:
- Computer: DNS name of the forwarder
- Health: See Forwarder Analysis
- WEC: See Forwarder Analysis
- Last Heartbeat: This is the last heartbeat reported by WEC which represents the last time the computer checked in with the collector to say "I'm here and I'm subscribed" whether it had any events to forward or not.
- AD: See Forwarder Analysis
- Last Logon: LastLogonTimeStamp from computer account in Active Directory
- AD Group: For Deterministic subscription policies, this shows the AD group assigned in Allowed Forwarders that indicates this computer should subscribe to this subscription
Allowed Forwarders
See the "Allowed Forwarders" heading below.
Filters
See the "Filters" heading below.
Edit/Create Subscription Wizard
When you edit or create a subscription, Supercharger presents a wizard with the following pages:
Description
In addition to description you can disable the subscription on this page. The subscription remains in WEC but after disabling it, forwarders will stop sending events until it’s re-enabled. Supercharger will also stop analyzing the health of the subscription.
This is also where you configure which Event Log receives the events sent by forwarders as a result of this subscription. This is usually the Forwarded Events log.
Supercharger uses this page to display the subscription’s type which is normally source-initiated. Supercharger only allows you create source-initiated subscriptions but it gracefully handles any collector-initiated created outside of Supercharger. Protocol will normally be HTTP and port is normally blank unless explicitly configured with different settings outside of WEC.
Policy
Allowed Forwarders
This is where you add groups from Active Directory to define which computers in the domain should forward events to this subscription. This dialog allows you to search for groups in the Collector’s domain. Supply any portion of the beginning of the group’s name.
Groups can be added as Included (Is Included checked) or Excluded (Is Included unchecked). This allows you to include large groups with many members but exclude a subset of the computers by adding another group as Excluded. If a computer is both Excluded and Included, Excluded takes precedence.
Windows Event Collection supports nested groups and so does Supercharger’s deterministic health analysis. While Windows Event Collection technically supports groups from other trusted domains we do not recommend it and Supercharger’s deterministic health does not attempt to analyze groups from other domains. To use only a subset of the forwarders, with deterministic policies you can also specify LDAP filters.
Note: If you are new to Windows Event Collection please note that adding a computer’s group here does not cause the computer to immediately begin sending events. You must also define this collector as a “target subscription manager” on the desired computers via group policy which is explained here.
Filters
This is where you define which Event Logs and which events within those logs should be forwarded by source computers. You can either enter an XPath query or select a Managed Filter. Discovered subscriptions display the XML XPath query previously defined on the subscription.
3.2. Subscription Policies
Subscription Policies allow you to ensure consistent configuration of WEC settings across multiple subscriptions (even on different collectors and domains) similar to how Group Policy works in Windows.
Most WEC subscription settings are not directly accessible when you edit a subscription. Instead they are managed by the Subscription Policy assigned to that subscription. You can create and edit Subscription Policies via Settings on the main navbar. Supercharger comes with 2 pre-built subscription policies:
- Discovered Subscriptions Policy – This is read only policy automatically assigned whenever Supercharger discovers a subscription created outside of Supercharger. “Enforce WEC settings” is always unchecked on this policy which means that Supercharger makes no Subscription Policy based changes to discovered subscriptions unless you explicitly assign a different policy to the subscription. Other settings like Pruning Old WEC Sources is disabled as well. Basically, Discovered Subscriptions are treated as hands-off by Supercharger until you assign another policy. Health Assessment Basis is Deterministic (for more information see Forwarder Analysis).
- Default Subscription Policy - This is the system-wide default subscription policy. Other policies you create start out with all settings simply pointing to this policy. This allows you to “configure by exception”. Use this default policy for all your general settings that should apply to most subscriptions. Then create additional policies for those subscriptions requiring an exception and then only configure those settings that actually need to be different.
Normally, most settings will be left configured to the default settings shown below:
- Forwarder Analysis
- Health Assessment Basis - This setting allows you to change the way Supercharger will analyze forwarders that use this subscription policy. In addition to WEC settings, Subscription Policies also are where you configure health analysis for subscriptions. The health status of a subscription is really all about its forwarders (aka “sources” in WEC) which is described under Forwarder Analysis.
- Min Percentage Healthy - This setting is a numerical value 0 through 100. It specifies what health percentage level must be reached when comparing Problem Forwarders to Healthy Forwarders in order for the subscription icon to display green in Supercharger's dashboard.
- Arbitrary Forwarder Qty - This is the expected forwarder quantity if the Health Assessment Basis setting is set to Arbitrary. For more information read the "Arbitrary" section under Forwarder Analysis.
- Days Till Dormant - This specifies how many days pass until a forwarder is listed as Dormant in the Current Forwarders tab of the subscription.
- Ignore No Heartbeat (Hrs) - This setting specifies how many hours can pass until a forwarder is considered Ignored.
- Prune WEC Sources - This setting can be enabled or disabled. The "Days Since Last Heartbeat" can also be set here. To learn what this setting does please read the Pruning Old WEC Sources KB article.
- Health Assessment Basis -
- WEC Settings
- Enforce Wec Settings - Enabling this setting allows Supercharger to make Subscription Policy changes based on discovered subscriptions.
- Configuration Mode - This is a WEC setting which specifies how to optimize the delivery of collected events.
- Normal - This option does not conserve bandwidth. When Normal is selected events are delivered by being pulled 5 items at a time with timeout of 15 minutes.
- Custom - This setting enables the Heartbeat Interval, Delivery Max Latency Time and Delivery Max Items settings in the box below this setting.
- MinBandWidth - This option conserves bandwidth. A push delivery method is used with both a timeout and heartbeat interval of 6 hours.
- MinLatency - This option is the fastest delivery option for events. It pushes events every 30 seconds. This options is recommended for most environments but especially where high priority events are being collected.
- Custom Configuration Mode Settings
- Heartbeat Interval - Default value is 3,600,000 milliseconds or 60 minutes. The heartbeat interval specifies how often a forwarder checks in to report that it is active and healthy but has no events to send.
- Delivery Max Latency Time - Default value is 900,000 milliseconds or 15 minutes. This setting configures how long a forwarder will keep an event before it sends it to the collector.
- Delivery Max Items - Default value is 50,000 items. This setting specifies how many events are batched together before being sent to the collector.
- For example, the default values listed above would create a situation where either 50,000 events are available to send or 15 minutes is reached. Which ever value is reached first will cause the events to be send from the forwarder to the collector.
- Other WEC Settings
- Content Format - Default and recommended value is RenderedText. This setting specifies how events are formatted.
- Locale - This setting is a language/country culture identifier.
- Read Existing Events - If turned on, when forwarders subscribe to the subscription, they will send all matching existing events to the collector.
3.3. Forwarder Analysis
In Supercharger, Forwarders are the computers sending (or should be sending) events to a Windows Event Collector as part of a subscription. In WEC, forwarders are referred to as “source computers”.
The most complex aspect of Windows Event Collection is ensuring that all computers that should be sending events are really doing so. Many things can potentially go wrong resulting in events not being forwarded
- Group policy
- Group membership
- WinRM status on forwarders
- Security log permissions on forwarders
- WinRM status on collectors
- WEC service status on collectors
- DNS
- Domain controller replication
- Network
- Kerberos tickets
- Forwarder’s power status and physical location
This creates security, compliance and operational risks and drives up the care and feeding costs of Windows Event Collection. To help you eliminate these risks and efficiently manage WEC we’ve put a lot of work into forwarder analysis which is the foundation of WEC health monitoring in Supercharger.
Forwarder Analysis compares the current status of each source computer reported by WEC to what we expect based on the
- relevant Subscription Policy
- computer’s status in Active Directory
- groups included/excluded on the subscription
Supercharger determines how many computers should actively be sending events to compute the percentage of “healthy” forwarders. If that percentage is lower than minimum defined in the relevant Subscription Policy, the subscription is classified as unhealthy and reflected in the subscription’s status color on the dashboard and is rolled up to the Collector and Domain’s health status as well. Optionally Supercharger can alert you via events logged on the manager or by email.
Supercharger provides 3 different ways to analyze forwarders called Health Assessment Basis. For the most value and greatest accuracy, we usually recommend Deterministic, but your situation may require one of the alternatives.
Deterministic
|
Expected Forwarder Quantity |
Supercharger queries AD and enumerates each computer or computer account in the groups included/excluded on the subscription (or a subset of them using an LDAP filter). Supercharger considers the computer’s account status and LastLogonTimeStamp to identify dormant or disabled computers which do not count. |
|
When to Use |
You use AD groups or individual computers included/excluded on the subscription’s Allowed Forwarders to define which computers should be sending events to this subscription. This is the recommended approach since it provides a quantitative way to control and measure Windows Event Collection. Do not use this method if
|
Empirical
|
Expected Forwarder Quantity |
Supercharger queries WEC for all the computers which have ever targeted the subscription as a source, and counts those computers that are reasonably expected to still be sending events:
Supercharger ignores the AD groups included/excluded on the subscription. |
|
When to Use |
You don’t want to base expected forwarders on the AD groups include/exclude on the subscription. You use group policy to control which computers forwarder events to this collector. We don’t recommend this approach but we’ve seen implementations where Domain Computers is added as an included group to a subscription but then only a subset of computers is configured via Group Policy with this Collector as “target subscription manager”. This subscription has forwarders from other domains. |
Arbitrary
|
Expected Forwarder Quantity |
An arbitrary number you specify |
|
When to Use |
For smaller subscriptions where you know the exact number of computers that should be sending events. For large subscriptions managed on a “best effort” basis where you know roughly how many source computers exist and just want to know if active forwarders fall significantly below that number. The number of forwarders is stable or you are willing to update it as necessary. This subscription has forwarders from other domains. |
Supercharger performs all of this in the ForwarderAnalysisCommand, which each controller (agent) runs by default every 15 minutes. (If you want to get an update without waiting, you can submit a ForwarderAnalysisCommand on demand from the Collector viewer dialog.)
Forwarder analysis determines up to 3 different statuses for each forwarder explained below. You can view Forwarder status on the Current Forwarders tab of a subscription’s viewer dialog.
|
Health Status |
Status in the view of Supercharger taking into account the forwarder’s status in WEC and Active Directory and according to the Health Assessment Basis. This is the determining factor for computing the % of health for the subscription. |
Possible values
|
|
WEC Status |
“Runtime status” as reported by WEC for the source |
|
|
AD Status |
Status of the computer’s account and LastLogonTime stamp in Active directory |
|
3.4. Collectors
Collector objects in Supercharger correspond directly to the Windows servers where you use Windows Event Collection. To add such a server to Supercharger, simply install the Controller (aka agent) service. See how to article. The Master server is always listed as a Collector even though in large environments you may not use it as such.
Controller (aka Agent) Service
The Supercharger controller (aka agent) service reports all status data regarding Windows Event Collection to the manager and processes any commands submitted from the manager or you, the user, through the web interface. Some of the work the Controller handles includes:
- Executes subscription creation, deletion and modification as requested from the manager and web application
- Periodic analysis of local WEC subscriptions
- Performance analysis including CPU and Events Logged per Second. This data is reflected in near real time and compared to 7 day peak and average on the collector and subscription tiles of the dashboard. Internally Supercharger also records these statistics each hour for longer term analysis which will be surfaced in future versions.
- Monitors and manages the state of critical services including WinRM and Windows Event Collection. Normally Supercharger ensures the services are always started unless you change the desired state from the Collector’s viewer dialog.
- Enforces Subscription Policy configuration on assigned subscriptions.
- Deletes outdated WEC sources. See Pruning.
- Queries the local Active Directory domain on behalf of the web application and manager
The controller communicates strictly via SQL (TCP 1433) and uses SQL Service Broker functionality to avoid constant polling. The only exception to SQL communication is when a controller learns that the manager has been upgraded; the controller then uses HTTPS or HTTP to download the latest version of the controller installer and proceeds to upgrade itself. If automatic upgrade should fail for any reason you can manually upgrade the controller by following the same method as installation.
From the collector’s viewer dialog you can submit commands to run on demand including:
- Forwarder analysis
- Restart the Controller Service
- Reboot the Collector
- Prune Old WEC Sources
The Supercharger Manager monitors the status each controller service. If it detects the controller has not reported in for recently it will alert you to the health status change and reflect it in the status color of the collector’s tile on the dashboard. As will all objects in Supercharger you can see the reason(s) for a given health status color by opening the controller’s viewer dialog.
If a collector will be down for maintenance or if you prefer Supercharger, for purposes of health monitoring, to ignore a collector you can mark it as “Exclude from health monitoring” on the collector’s viewer dialog.
3.5. Collector Policies
Supercharger allows you centrally manage all WEC related settings in Windows based on the Collector Policy you assign. Each area of configuration settings can be disabled so that Supercharger leaves the collector configured as is. Supercharger automatically assigns new collectors to the pre-built Default Collector Policy which defaults to all settings disabled.
If you decide to fine tune any collector settings, we recommend you create a new Collector Policy and assign it initially to one collector for testing purposes until you are confident your settings work as intended.
Collector Policy settings are defined as XML structures, please contact support if you need help editing the XML.
3.6. Domains
Domains in Supercharger correspond directly to the Active Directory domains of your Windows event collectors. Supercharger does not depend on AD trust relationships or forest boundaries. Whenever you add a new collector, Supercharger automatically creates a new domain object if necessary and presents all collectors under their appropriate domain.
Supercharger is aware of domains for coordinating Load Balanced Subscriptions.
When you click on a Domain, Supercharger will display all properties in its Domain page.
Load Balancers Tab
This tab displays all Load Balancers in the Domain and allows you run Load Balancer Maintenance on demand.
Status Tab
Master Collector
Supercharger automatically designates the first collector in a domain as the “master collector” for that domain. This collector processes any Active Directory related tasks. The domain page's Status tab identifies the current master collector for that domain.
If your master collector needs to be decommissioned or will be down for an extended period you can promote a different collector in the domain; look for the Promote button in that collector’s viewer dialog. There is no need to promote a new collector if the current master will only be down for less than a day, but be aware that you will not be able to make any Load Balanced Subscription related changes during that time in the affected domain.
Group Policy
As explained in Implementing Windows Event Collection you must use Group Policy to target forwarder computers at your collectors. Group Policy requires a specially formatted string each collector that you wish to target. Supercharger provides this string for each controller in the domain, in that domain page's Status tab; the list is labeled as Subscription Manager strings.
3.7. Managed Filters
When creating subscriptions you must create a filter on each subscription to filter the incoming collected events from your forwarders. Many customers are using the same filters repetitively with the only difference on the subscription being the assigned forwarders. To expedite the subscription creation we recommend you create your own managed filters in Supercharger. This will allow you to reuse the filter on any subscription by selecting it from a drop-down menu when you create the subscription.
To create managed filters in Supercharger:
- Click on Settings in the left menu.
- Then click on the "Managed Filters" tab.
- Next click on the green "Add" button.
- In the Raw Xpath String box, enter the Xpath of the filter you want to use. If you're not an Xpath expert there is no need to worry. Simply go to Event Viewer, select the appropriate log and click filter on the right. Create your filter as you normally would and when you are finished click on the XML tab. Copy the Xpath query from there into Supercharger.
- Now when you create subscriptions you will see this new filter in the list of Manage Filters in the subscription creation GUI.
3.8. Pruning Old WEC Sources
Windows Event Collection creates a registry key and several child values for each source computer that ever sends events to a given subscription. However, WEC never deletes these registry objects even after sources are no longer valid. This can create 2 issues:
- In environments with heavy forwarder turnover, this results in an ever-growing glut of old source records which slows down WEC and makes Event Viewer unresponsive.
- Supercharger cannot accurately determine health of subscriptions where you choose the Empirical health assessment basis. Empirical health assessment bases its expected forwarder count on the WEC sources found in the registry. If you have many outdated WEC sources, Supercharger will rate the health of the subscription lower than what it should be.
Supercharger solves this problem with the optional pruning feature which you can enable/disable in Subscription Policy objects. When you enable Prune WEC sources, you must specify how many days must elapse with no heartbeat being reported by a given WEC source before it is pruned. By default, Supercharger runs the PruneWecSourceComputersCommand at midnight, but you can run the command on demand from a collector's viewer dialog.
When a WEC source is pruned, the registry key is simply deleted. If the WEC source becomes active again in the future, WEC will automatically recreate the key.
3.9. Performance Monitoring
Supercharger monitors the CPU of each collector and the Events-perp-second counter on each destination log. Supercharger maintains a 7-day-average for both counters and a 7-day peak for Events-per-second. These values are displayed in the tiles for each respective object.
The collector tile below indicates the current CPU with the darker arrow on the bottom and the 7-day average with the ligher arrow on top. The collector name in bold indicates that it is the Supercharger Manager server. We also see a status of the general health of the collector.
Windows is inconsistent with reporting event log counters. If available Supercharger tracks events per second with the 7-day-peak defining the scale of the chart, the dark arrow on the bottom indicating current EPS and the lighter arrow on top showing the 7-day average.
Internally, Supercharger captures these same statistics at the top of every hour for long term trending and capacity planning. Each collector in Supercharger also has a performance chart showing WEC Health vs CPU vs EPS. There is also a second chart for WSMan Quota Statistics.
To assist with environment planning and collector health across your entire WEC implementation, we also populate the following charts for all collectors on a single pane of glass.
3.10. Health and Alerting
Supercharger makes a determination about the health of each object in your WEC environment beginning at the Forwarder level. Beginning at the subscription level Supercharger indicates the object’s health by the icon’s color on the dashboard.
Each subscription has an assigned Subscription Policy whose health assessment basis defines against what criteria the forwarders on that subscription should be judged.
You can find out the reasons behind any object’s health opening its viewer dialog.
You goal should be to maintain your environment with all objects showing as green. Supercharger allows you to adjust subscription health criteria so that whatever situation you define as nominal will be recognized as such by Supercharger.
If you have a collector where health cannot be obtained for whatever reason you can elect to exclude that collector from health analysis by indicating such in its viewer dialog.
Automatic Health Report via Email
If you configure Supercharger with SMTP information you do not necessarily need to visit the dashboard to know about your WEC environment’s health. Supercharger report (by default, daily, at 7AM) that lists each domain, distributed subscription, collector and subscription along with its health status color and the reasons for that status.
Alerting
Supercharger can also alert you in near real-time to changes in health on any object from Subscription up to domain. You can receive alerts via your systems management solution or directly from Supercharger by email.
The Manager checks for any health status changes across all collectors by default every 15 minutes. If the health status color of an object has changed Supercharger logs an event to the manager’s local Application event log with the following event IDs:
|
New status color and severity |
||||
|
Gray |
Green |
Yellow |
Red |
|
|
Information |
Warning |
Error |
||
|
Domain |
103 |
102 |
101 |
100 |
|
Collector |
203 |
202 |
201 |
200 |
|
Subscription |
303 |
302 |
301 |
300 |
|
Load Balanced Subscription |
403 |
402 |
401 |
400 |
You can monitor these events and create incidents using your systems management solution or you can configure Supercharger to email you alerts.
3.11. Troubleshooting
The web application can only start if the Supercharger Controller service is running on the Manager and reports that the database is in ready state. If any of these conditions are not true the Web application will automatically display an error page with all available diagnostics information which you should supply to support. In addition, you can access the Log pages from the main navigation bar.
Log Pages
Supercharger maintains an internal log of all events from all collectors with severities
- Information
- Warning
- Error
- Fatal
You can view this log on the eponymous page via the main navigation bar.
Other tabs on this same page allow you to view the Manager’s application log or event download its trace log. Supplying this information when opening a support ticket will dramatically speed up case resolution.
Trace Logs on Each Collector
Each collector normally reports all Informational and above events to the Manager as described above provided the database is available and the collector is registered. In case the controller can’t report events to the manager, Collectors always log the same informational and above events to their local Application event log.
In addition, collectors maintain a text trace log in the “logs” subfolder of the Supercharger Controller service directory. By default, Debug and above severity messages are logged to this folder. When a log grows to 100mb, Supercharger rolls over to a new log and compresses it to about 7mgb. Supercharger keeps no more than 10 such logs before deleting the oldest. To customize this behavior contact support. Support may request these logs or ask you to enable a higher level of Trace logging.
3.12. Security
NOTE: In addition to the security level assignments described below, any members of SuperchargerSuperUsers, a local Windows group on the Manager, automatically Administrator level authority but are not shown in on the Settings\Security Tab. This local group facilitates initial access for the user who installs Supercharger and is a failsafe method for local Administrators to re-gain access if the users or groups assigned below are deleted from Active Directory.
Supercharger has 3 security levels which you can configure via the Settings\Security page.
|
Level |
Authority |
|
Administrators |
|
|
Operators |
|
|
View Only |
|
The interface does not support them adding users or groups from another domain. To add users from other domains, simply create a group in the manager's domain and add that group under Security settings. Then selected users can be made members of that group.
3.13. Overrides
Overrides and Global Settings should only be used when working with our technical support team. Adjusting or modifying these settings without the direction from our support staff may have adverse effects to Supercharger in your environment.
3.14. Licensing
Supercharger can be installed and will run fully functional in Enterprise mode for 30 days from the installation day. Once the expiration date is reached, Supercharger will run with a 45 day grace period. If a new license is not applied during this 45 day grace period, it will not function properly once the grace period expires.
If you are testing Supercharger and need to purchase licensing, please contact sales@logbinder.com.
Permanent license keys are not issued until an invoice payment has been received. If you are an existing customer pending payment and your temporary license key will expire, please request an extended temp key from our support team.
If you are an existing customer customer and the follow prerequisites have been reached:
- Your invoice is paid
- You have already installed Supercharger
Then please open a support ticket and request the license key. Please include in the ticket the Licensee and/or End User and the Thumbprint from the "Settings" page under the "Licensing" tab in Supercharger. It would expedite the request if a screenshot of the entire licensing screen is attached to the support ticket as well.
3.15. Event Logs
Supercharger allows you to create custom events logs to use as target logs for incoming forwarded WEC events.
Benefits:
- Analyze EPS per subscription going to each unique log
- Many SIEMs spool one thread per incoming log. By using multiple custom logs you can boost the input of many SIEMs.
- Many others
From the GUI you can create a single custom log on one collector as shown below:
This log would then show up in Event Viewer and be ready to receive forwarded events.
When creating a Load Balanced subscription, you can also create a custom log on multiple collectors with a single click. As shown below, you first give the log a name. Supercharger will then check to see if the log currently exists on any of the collectors. You can then click on the "Create log where missing" button and Supercharger will submit commands to create the custom log on the collectors.
3.16. Stalled Subscription Watchdog
We have received reports that WEC subscriptions for some yet undiscovered reason will stall. The subscription will remain active but just stops working. The svchost.exe process running EventLog shows 0% CPU usage. Microsoft has been made aware of the issue but there is no fix for it yet.
With the release of Supercharger 21.8.4 a new feature has been added, Stalled Subscription Watchdog. This feature is enabled by default after installation by the StalledSubWatchdogEnabled override. There are two override settings to configure this feature:
- StalledSubWatchdogThresholdPercent (default 3)
- StalledSubWatchdogMinSecondsBetweenRetries (default 3600)
A subscription is considered stalling, if meets the following criteria:
- it is enabled
- it doesn't meet the number of healthy forwarders specified by its subscription policy
- the percentage of healthy forwarders is lower than StalledSubWatchdogThresholdPercent
If the watchdog is enabled by StalledSubWatchdogEnabled and the subscription has been stalling for at least StalledSubWatchdogMinSecondsBetweenRetries seconds, a retry will be initiated on the subscription and an Info message will be posted.
3.17. Stalled Event Log Watchdog
As we all know Event Viewer is very reliable but is not very robust. Often after clicking on Event Viewer you must wait for the MMC snap-in to respond and populate the logs. With the increase usage of Windows Event Collection logs are filling faster and getting bigger. One of our larger customers noticed a troubling situation. Logs used as destination logs for WEC subscriptions were stalling. There was no alert, no error, no warning and no other notification. The only way to determine that the log was indeed stalled was to have a set of eyes looking at the log in Event Viewer and noticing that no new events were being received.
With the release of Supercharger 21.8.4 a new feature has been added, Stalled Event Log Watchdog.
This feature is turned on by default in Supercharger by the EventLogStalledCheckingEnabled override. There are two customizable override settings to configure it:
- EventLogStalledSecondsBeforeResetting (default 90)
- EventLogStalledSecondsBeforeRepeatingReset (default 3600)
An event log is considered stalled if it meets the following criteria:
- It is in use (i.e. it is part of at least one subscriptions)
- Its EPS is lower than expected compared to the average EPS and taking into consideration the standard deviation (i.e. current EPS < average EPS - (std deviation EPS2))
If the watchdog is enabled by EventLogStalledCheckingEnabled and the event log has been stalling for at least EventLogStalledSecondsBeforeResetting seconds, but has not been reset within EventLogStalledSecondsBeforeRepeatingReset seconds, a reset will be initiated on the event log and an Info message will be posted.
Event log reset can also be submitted manually through the UI under Event Log Status.
3.18. Continuity Tracing
Supercharger remediates many WEC issues, often times without the end user knowing an error has occurred. For example, our watchdog for stalled subscriptions and stalled event logs does this. WEC has proven itself to be very robust. From the endpoints to the collectors WEC is very reliable but sometimes issues lie beyond the control of WEC. One thing that has come to our attention is an issue of dropped events upstream of WEC and to the downstream consumer (think SIEM) losing events because they are down or not ingesting events as fast as they are coming to to the WEC collector - and thus the event log wraps before the SIEM consumes some events. This is where Supercharger's Continuity Tracing feature plays a roll.
What is Supercharger's Continuity Tracing?
We inject tracer events into your WEC subscription event flow so that you can determine if your downstream consumer is receiving all of the events you are collecting.
How does it work?
Supercharger logs event ID 42031 to the Application Log on your WEC collector with log source "Supercharger Continuity Tracing". Then for each destination log (ForwardedEvents or a Supercharger custom destination log) Supercharger creates a Supercharger managed subscription. This subscription subscribes the local collector as the only source computer and "Supercharger Continuity Tracing" as the only event log source to collect in to the destination log. The custom "Builtin ContinuityTracing Subscription Policy" is configured so that tracer events are forwarded immediately.
These subscriptions will be displayed on the dashboard of the collector with the naming convention "ScContinuityTracing###".
How to use event 42031?
Event ID 42031 is logged at the correct time within a few hundredths of a second at the max. For instance, if you configure it to inject a tracer event every minute, then it will log a 42031 at the top of the minute. Here is an example of the event:
Supercharger tracer event.
Collector: lab-sc2-2.lab.local
TraceStart: 5/11/2024 5:34:17 AM -07:00
Sequence: 167
Scheduled: 5/11/2024 8:22:00 AM -07:00
SecondsBetweenTracers: 60
Use this event to ensure downstream pipeline components (e.g. SIEM) are keeping up with event flow and to measure lag. Sequence is a counter that re-starts at 0 with Supercharger service startup (see TraceStart above). Scheduled should be very close to Event.TimeCreated. Disable this tracing by setting ContinuityTraceLoggerDisable to true. Adjust SecondsBetweenTracers by setting ContinuityTraceLoggerSeconds to a factor of 60 between 5 and 60. Change EventId with ContinuityTraceLoggerEventId. Compare this event along with event ID 42032 to intake statistics from your downstream logging pipeline consumers to make sure they are keeping up with the rate of events.
The event details are explained in the event itself. The sequence above restarts at zero when the service is restarted. So in the your downstream consumer (Splunk, LogRhythm, ArcSight, Qradar, etc...) analytics you need to either look for 42031 being received at every sequence (default 60 seconds) or look for gaps in the sequence number. To help identify the sequence starting back at zero (when the service restarts or server restarts), the event content also includes a start time which is static per sequence.
You can use overrides in Superchargers settings to control and customize continuity tracing:
- ContinuityTraceLoggerSeconds
- This controls how often 42031 is generated. It is displayed as SecondsBetweenTracers in the event details. If modified the number of seconds must be in increments of 60 seconds. If you save the setting and it defaults back to 60 then you used an invalid value. The default setting is 60 seconds.
- ContinuityTraceLoggerDisable
- If set to "True" continuity tracing is disabled. The default setting is "False".
- ContinuityTraceLoggerEventId
- You can customize the event ID. The default is 42031.
- InboundEpsLoggingEventId
- You can customize the event ID. The default is 42032.
3.19. EPS Tracking
Supercharger remediates many WEC issues, often times without the end user knowing an error has occurred. For example, our watchdog for stalled subscriptions and stalled event logs does this. WEC has proven itself to be very robust. From the endpoints to the collectors WEC is very reliable but sometimes issues lie beyond the control of WEC. One thing that has come to our attention is an issue of dropped events upstream of WEC and to the downstream consumer (think SIEM) losing events because they are down or not ingesting events as fast as they are coming to to the WEC collector - and thus the event log wraps before the SIEM consumes some events. This is where Supercharger's Continuity Tracing feature plays a roll. In addition to Continuity Tracing, we have added EPS tracking to Supercharger.
What is Supercharger's EPS Tracking?
Supercharger generates event ID 42032 to the collectors native Application log. This event data can be used in conjunction with continuity tracing event ID 42031 to ensure that your downstream consumer is keeping up with the rate of events.
How does it work?
Supercharger logs event ID 42032 to the Application Log on your WEC collector with log source "Supercharger EPS". One event is generated every minute (this interval can be modified) for each destination log (ForwardedEvents or a Supercharger custom destination log).
How to use event 42032?
Event ID 42032 is logged at the correct time within a few hundredths of a second at the max. For instance, if you configure it to inject a tracer event every minute, then it will log a 42032 at the top of the minute. Here is an example of the event:
Destination log events per second.
Collector: lab-sc2-2.lab.local
DestinationLog: ForwardedEvents
TimePeriodStart: 5/31/2024 8:46:00 AM -07:00
TimePeriodEnd: 5/31/2024 8:47:00 AM -07:00
Seconds: 60
AverageEPS: 1
LogWillWrapInHours: 1.94
MaxFileSizeBytes: 20971520
CurrentFileSizeBytes: 20975616
EstimatedMaxRecordCount: 6971
CurrentRecordCount: 6971
AverageEventSizeBytes: 3008
PercentFull: 100%
Compare this event along with continuity tracing event ID 42031 to intake statistics from your downstream logging pipeline consumers to make sure they are keeping up with the rate of events. Disable these events by setting override InboundEpsLoggingDisabled to true. Change the frequency of this event with InboundEpsLoggingSeconds. Change this event ID with InboundEpsLoggingEventId.
Event details:
Collector: This is the FQDN of the collector hosting the destination log receiving the forwarded events from the endpoints.
Destination Log: This is the log on the collector receiving forwarded events from the endpoints.
TimePeriodStart: Start of the time period that the calculations below are based on.
TimePeriodEnd: End of the time period that the calculations below are based on.
Seconds: Time (in seconds) period analyzed for the below calculations.
AverageEPS: Average events per second for the time periods above.
LogWillWrapInHours: Amount of time in which the oldest events will be overwritten if the above "AverageEPS" is sustained.
MaxFileSizeBytes: Maximum log size as specified in the event logs properties.
CurrentFileSizeBytes: Current size of the log at time of analysis. Unless this is a new log this metric will be near or equal to "MaxFileSizeBytes".
EstimatedMaxRecordCount: The number of events that the log can hold before wrapping if the "AverageEventSizeBytes" is sustained.
CurrentRecordCount: The quantity of events in the log.
AverageEventSizeBytes: The average size per individual event in the log.
PercentFull: Percentage of "MaxFileSizeBytes" being used.
You can use overrides in Superchargers settings to control and customize continuity tracing:
- InboundEpsLoggingSeconds
- This controls how often 42032 is generated. It is displayed as "Seconds" in the event details. If modified the number of seconds must be in increments of 60 seconds. If you save the setting and it defaults back to 60 then you used an invalid value. The default setting is 60 seconds.
- InboundEpsLoggingDisabled
- If set to "True" EPS tracking is disabled. The default setting is "False".
- InboundEpsLoggingEventId
- You can customize the event ID. The default is 42032.
3.20. Configuring Supercharger for Entra
Supercharger supports not only on-prem windows event forwarders but also Entra/Intune joined forwarders. There are multiple steps in this process. In the video at the bottom of this article we will be demonstrating:
Installing and Configuring Supercharger
Adding an Optional Second Windows Event Collector
Configuring Entra Tenant
Enter Entra Tenant ID and Create App Registration
Installing and Configuring Supercharger
Installing Supercharger
- Download Supercharger from LOGbinder.com
- Run the installation file
- Perform a default installation
- For further information go to this Installing Supercharger KB article
- The installer will install IIS if it is not installed and will reboot the server. The installation will resume upon login.
- Supercharger will automatically open the web browser upon completion of the installation
***Please note that if your DC's are Win2008r2 then you will need to run "winrm qc" on each DC in an elevated cmd prompt.***
Adding an Optional Second Collector to Supercharger
- You can follow along with the video or follow the steps in this KB article.
Enter Entra Information and Create App Registration
The following steps will require access to your Entra tenant. You will copying information from the tenant and inputting it on the "Add Entra Tenant" page in Supercharger.
- On the tenant overview page copy the "Tenant ID" and the "Primary Domain" and paste this information into Supercharger.
- On tenant overview page click on "App Registrations" and then "New Registration".
- Enter a name for the app registration and leave the other fields default.
- After saving, copy the "Application (client) ID" and paste it into Supercharger.
- On your new app registration click on "API permissions" in the side menu.
- Remove the "User.Read" permission.
- Then click on "Add a permission" and on the "Request API permissions" window navigate to Microsoft Graph\Application permissions\Device and select "Device.Read.All". Then click on the "Add permissions" button.
*NOTE: If you will be using groups with devices in them then you will also need to add the "GroupMember.Read.All" permission.
In the screenshot above you can see that the permissions are granted but consent has not be given, hence the orange warning sign. You will need to click on the check mark to grant admin consent. - Next choose how you want Supercharger to authenticate to MS Graph. There are 3 options available.
- Certificate in Local Machine Store of the Designated Collector
- Azure VM Managed Identity
- Secret stored in Supercharger (This is the option we are using in this example so select it in the dropdown.
- Back in Entra in your app registration click on "Certificates & Secrets" in the left menu and then click on "New client secret".
- In the "Add a client secret" window type in a description and select the longest expiration available and click on "Add".
- Copy the Value and paste this in to Supercharger. Also change the expiration date in Supercharger to what is show next to your value.
- Lastly, in Supercharger select which collector will run the MS Graph queries.
4. Resources
4.1. Supercharger Version History
(For upgrade instructions, see 5.27. How To Upgrade Supercharger)
Supercharger 25.3.15 (3/27/2025)
- FEATURE: Added support for certificate-based WEC over the internet forwarding and Entra joined devices
- FEATURE: Option to omit healthy (green items) from health report emails
- Fixes to logging issues; specially errors containing "RefreshEventLogAverages"
- Fix a bug where a custom named event log has a name similar to a native system event log
- Add optional setting for minimum ignore heartbeat duration when assessing forwarder WEC status
- Fix for issues with EPS history
- Fix for issues with adding a license key to Supercharger when no email was setup in settings
- Fix for handling WEC Error 15081
- Fix for a unique issue in some environments where duplicate SIDs exist
- Fix to delete unneeded registry values at uninstall
Supercharger 25.1.3 (1/7/2025)
- No code changes. New version/installer due to reissued code signing certificate
Supercharger 24.11.7 (11/25/2024)
- Upgrade to .NET 8
- Fix a bug where not able to select custom event logs named like some Windows event logs, such as Application, Security
- Increase the timeout for updating event log averages stored by Supercharger
Supercharger 24.9.2 (9/11/2024)
- Fixed bug related to missing computers in Active Directory now marked "Deleted"
- "Run Projection" button now runs a Full AD Computer Projection
- Fixed "Enable" button on the Group Policy tab under Domains
- Fixed issue related to error message "Controller Id should be filled in by now"
- Added logic to ignore marking a destination log as used if it is used on a disabled subscription
- Stalled Subscription Watchdog now warns once a day then logged as an "Informational" message
- Added an extract for ADComputers
- Fixed bug causing high CPU usage after a login session expires (if enabled)
- Following Microsoft's recommendation we now set Authenticated Users read access to the logs folder to "This folder and subfolders"
- Added support for moving custom event logs to another folder
- Added decimal places to EPS counters so that low EPS stats do not result in showing zero EPS
- Trim whitespace on LDAP filters that could result in an error
- Adjusted when we install GPMC (if necessary)
- Fixed change alert emails from being sent if nothing changed
- Fixed loading indicators not working
- Fixed not being able to delete subscriptions
Supercharger 24.5.4 (5/11/2024)
- Enhancement to code for Session Expiration when disabled
Supercharger 24.4.11 (4/30/2024)
- Fixed regression bug related to modified values not saving in settings fields and search fields
Supercharger 24.4.1 (4/12/2024)
- Fixed infinite loop bug introduced in previous versions session timeout feature
Supercharger 24.3.1 (3/25/2024)
- Added override to enable a login session timeout
- On new installs, removed "User" permissions from the 'C:\Program Files\Supercharger\Manager\logs' folder
- Added additional details to the domains "Trust" tab for clarification
- Display deterministic criteria on the Subscription Status page
- Fixed bug related to email warnings enabled if no email address is specified and a license key is submitted
- Correct typo on coordinates page
- Display entire "Base DN" in the LDAP list
- Bug fix for errors displaying "Cannot insert duplicate key row"
- Added WarnOnRecurringCommandAlreadyRunning override
- Update .NET Hosting Bundle to version 6.0.24
- Upgraded SQL Server to SP3 for new installs
- Disable Group Policy checks by default
- Fixed bug where last controller of domain cannot be decommissioned
Supercharger 23.11.2 (11/14/2023)
- Fix UI freezing under Settings, when no "To" email addresses are specified in email settings
- Fix timeout errors related to SQL execution strategy
Supercharger 23.8.4 (8/22/2023)
- Upgraded .NET hosting bundle
- Fixed bug resulting in "same key has already been added" error message
Supercharger 23.4.4 (4/12/2023)
- Upgrade to .NET 6
- Enhancement to deletion of files in wecXml folder
- Purge now happens when service starts
- Hide "Copy to clipboard" if not browser supported
- Updated help links to new support/kb portal
- Require "Allowed Forwarders" when editing a subscription
- Fix to delete load balanced subscriptions if no controllers exist in domain
- Remediate KeyNotFoundException error
- Fix to limit subscription name lengths (197 characters)
- Fix to allow a deleted controller to be re-added if not decommissioned
- Fix to allow more characters in Managed Filters (increased from 32k to 64k characters)
- Fix graphs no displaying correctly for certain time formats in regional settings
- Bug fix of case sensitivity in override settings
- Highlight master server on Log page
- Display if Group Policy setting is enabled
- Allow sorting on various tables
Supercharger 22.8.9 (9/2/2022)
- Log page defaults to "All" if there are no Errors/Warnings to acknowledge
- Validate (and fix, if possible) values when adding or editing overrides
- Fix bug with upper/lowercase issue in target subscription manager url
- Fix bug where http://localhost//supercharger would give a 404 error
- Various code smells and security hotspots remediated
Supercharger 22.8.2 (8/26/2022)
- NEW FEATURE: Add Cross Domain Forwarding
- Upgrade .NET Core
- Add additional trace logging
- Add and enabled DB compression for some tables in SQL
- Remove duplicate domain components from LDAP queries
- Bug fix addressing "Error uploading the controller setup to the database" error message
- Bug fix addressing "Cannot insert duplicate key row in object" error message
- Bug fix related to using SQL Server HADR
- Make licensing checks quicker
Supercharger 22.1.8 (1/13/2022)
- Fix for bulk updating of DB values
- Fix for tools tips stuck behind menus
- Update to purging of records
- Upgrade to .NET Core
- Update to table size reporting
- Add delay in subscription update to help preventing WEC service overload
Supercharger 21.11.10 (12/6/2021)
- Add feature to see which event logs are used on more than one load balanced subscription
- Increased timeout for controller setup installer to upload to DB
- Retry controller setup installer downloading if could not download latest version from DB
- Reset related subscriptions after automatic event log reset
- Add option to event logs to set threshold for low EPS
- Filter out outliers before standard deviation calculation for low EPS detection
- Bug fix to standard deviation formula
- Bug fix for newly created load balancers freezing GUI
- Bug fix to suppress noise message related to Load Balancers with no subscriptions in logs
- Bug fix for group not found during Load Balancer Maintenance
- Bug fix to certain filters in subscription editor
- Bug fix for to allow longer names to work with auditing
- Bug fix where performance charts displayed data from other collectors
- Add option to not warn if EPS is zero if expected
- Bug fix to new subscriptions using LDAP queries
- Add feature to display load balanced subscriptions on event log status pages
- Display full name of event log on its Status tab
- Move status of services to collector Status tab
- Redesign of internal log details
- Upgrade .NET Core
Supercharger 21.10.6 (10/6/2021)
- Add feature to rearrange domains on Explorer page
- Add more details for subscriptions related to current forwarders
- Add feature in Load Balancer editor to create missing event logs
- Enforce recovery options for controller services to restart on failure
- Include domain name in name of current forwarders exported CSV file
- Add option to filter list of managed filters
- Fix for log names that contain spaces in the name
- Bug fix for built-in event logs enabled flag reset issue
- Bug fix for scheduled time come up with the same time twice in a row
- Bug fix for migration issue with ErrorText
- Bug fix for registry error during collector analysis
Supercharger 21.9.5 (9/5/2021)
- Add filtering to Managed Filters list
Supercharger 21.8.4 (8/23/2021)
- NEW FEATURE - Stalled Subscription Watchdog
- NEW FEATURE - Stalled Event Log Watchdog
- Fixed bug that classified subscriptions with zero forwarders as unhealthy
- Fixed bug with incorrect event log health color
- Logic to make event log gray if not in use
Supercharger 21.7.12 (7/31/2021)
- Correct typo in EULA
- Fixed issue with crashing if a custom DB is being used and login coordinates need to be entered manually
- Fixed EPS standard deviation algorithm
- Added HTTPS protocol option to Subscription Policy settings
- Fixed informational message related to Jumbo History Tracking
- Fixed informational message related to Load Balancer Nodes
- Added logic to trim unwanted characters from Target Subscription Manager entries
- Added logic to ensure latest controller setup file is uploaded to the DB
- Fixed issue with SC not loading after install; installer now runs iisreset
- Added logic to prevent invalid characters from being used for subscription names in load balanced subscriptions
- Added feature to force reboot of a controller server if WEC or WinRM is unhealthy
- Added tooltip for load balanced subscription titles
- Fixed issue with SQL Server user account remnant left behind after a controller is decommissioned
- Upgraded .NET Core hosting bundle
- Fixed broken "Reboot" command
Supercharger 21.6.6 (6/21/2021)
- Fixed issue with extending temporary license keys
- Added logic to prevent bad subscription names that use invalid characters
- Added screen splitter adjustment bar in GUI
- Added which domain Subscription Policies and Managed Filters are used in when viewing settings
- Added Subscription tab as the default tab when clicking back button in browser from Subscription settings
- Added name to tooltips for Event Logs and Subscriptions
- Bug fixes related to upgrading from 20.1.53 and older to current version
Supercharger 21.6.1 (6/1/2021)
- Split Custom Supercharger logs from Native windows logs during destination log selection
- Resize log selector dropdown
- Fix bug when decommissioning controller
- Fix bug when creating a new custom event log
- Fix bug with expand/collapse buttons in managed filters
- Fix bug for creating subscriptions with Free Version
- Improve user interface speed and responsiveness
- Add option to exclude non-Windows computers
Supercharger 21.4.3 (4/9/2021)
- Bug fix when editing subscriptions
Supercharger 21.3.16 (3/31/2021)
- DB retrieval optimization
- Add refresh count down
- Event log name comparisons case insensitive
- Add performance tab to Event Log
- Add Managed Filter Security Log Wizard
- Subscription Policy editor bug fix
- Add loader to license key submission
- Improved performance of license key submission
- Performance enhancement to Settings pages
- Purging refactored
- Enhancement to Group Policy collection process
- Optimized Refresh Collector, Collector Analysis and Forwarder Analysis command
- Enhancement to multiple pending commands
- Redesign Command Engine Worker
- Refactor promotion auditing
- Tripwire event filtering
- Redesign Trace log page
- Update NLog
- Adding filtering nonactive controllers
- Internal Log grid improvements
- Performance improvement
- Trimming data fields
- Add Info Only filter
- Improved export of log
- GUI improvement
- Modification to forwarders grid filtering
- Add authorization requirement to all pages
- Add option to delete shard subscriptions
- Purge audits after one year
- Purge Volume Leveling Scorecards older than 30 days
- Add loader to Group and User searches
- Allow users to authenticate in a multi-domain environment
- Bug fix for DST time change
- Forwarder license count fix
- Bug fix in Group Policy Services
- Enhancement to update controllers from the DB, not through HTTP
- Bug fix - If email address field is blank send to all security users and groups
- Bug fix for View Only users
- Bug fix to custom log name displaying in dropdown list
- Bug fix for an exception during scheduled task processor
- Bug fix for duplicate data in Forwarder Criteria table
- Enhancement to cache Health Statement List
- Bug fix for disposed repo
- Bug fix to internal log download directory access
- Bug fix to division by zero in Average Since Last Call
- Upgrade .NET Core hosting bundle to latest version
Supercharger 20.12.2 (12/2/2020)
- Fixed some issues with slow user interface
Supercharger 20.11.8 (11/28/2020)
- Added Jumbo balancing
- Added audit trail tied to every object in Supercharger
- Added group policy analysis to highlight possible problems with Target Subscription Manager entries, security log permissions etc.
- Added throttling to reduce repetitious warnings and errors and a clear criteria for what’s a warning vs error
- Added managed filters from Palantir
- Added feature to exclude small system drives from health check with an override
- Added links to KB articles
- Bug fix for naming custom event logs
- Bug fix to menu tooltips
- Updates to reporting charts
- Improvements to log downloads
- Performance tabs added to event logs
- Controller installer is now signed
- Many other enhancements
Supercharger 20.9.1 (9/3/2020)
- Load Balanced Subscription 2.0
- All new UI
- Performance Tracking
- much, much, more
Supercharger 20.1.53 (2/10/2020)
- Add Trace Log Management from Web UI
- Make restart controller more reliable
- Improve Collector Analysis needlessly processing forwarders by using WecUtil
- Split Up Collector Analysis for better performance
- Fewer Restarts of the Controller Service on WEC errors
- Make WEC API access externalized to ScWecUtil
- Add automatic setting of URLACL fix (see KB article on All subscriptions have 0 active forwarders; System Event IDs 10128, 10129)
- Make SQL timeout and execution strategy parameters soft coded
- Enable easy copying logs to clipboard
- When creating Load Balanced Subscriptions, put SC logs at top of Destination Log Names dropdown
- Improve Internal Log search
- Fix slow UI when there are many distributed subscriptions
- Efficiently get Comprehensive Forwarder Details for large number of records
- Other small fixes and enhancements
Supercharger 19.10.35 (10/20/2019)
- Fix a bug related to registry access
Supercharger 19.10.34 (10/15/2019)
- Add report: Comprehensive Forwarder Details
- Add report: Collector History (CPU, EPS)
- Include the destination log in the Overview tab of subscriptions
- Add a maintenance button to individual subscriptions of a distributed subscription to run maintenance on-demand (normally run daily)
- Add ability to change SQL Server connection timeout values
- Retry running wecutil.exe commands if hung
- Validate group SID when trying to create or update a distributed subscription
- Improve saving distributed subscription groups, especially when many forwarders are added
- Improve the way changes are saved to AD
- Improve calling forwarder analysis after updating distributed subscriptions or LDAP filters
- Use the same DC as much as possible to avoid replication issues
- Fix bug related to recreating a custom event log with same name but different capitalization
- Handle "A recipient must be specified" error when sending emails
- Limit the number of AD items displayed in the search dialog (to avoid the search taking too long)
- Close subscription dialog after deleting subscription
- Fix bug where perfmon counters would get purged if licensed, but license was expired
- Fix bug where error was wrongly reported if the WEC status was Inactive and AD status was NotFound
- Fix bug in setting up Builtin managed filters, such as filter for Security log with noise suppression
- Fix some bugs that caused a SID mixup when going AD group search
- Fix a bug that made subscriptions stop working if the related managed filter was changed (this was related to setting the wrong value for PublisherName when the sub was updated)
- Fix the sidebar flickering on Chrome
- Remove Events Lost counter
Supercharger 19.7.3 (7/30/2019)
- During upgrades, does not overwrite service account if "Local Service" is changed to custom user
Supercharger 19.7.1 (7/17/2019)
- Revised and removed reporting on lost events
- Fix a bug when a subscription was deleted outside of Supercharger
Supercharger 19.5.3 (6/3/2019)
- Update SQL Server to SQL Server 2016 SP2 Express
- Change implementation of counting servers for licensing
- Update SQL version in the installer
- Servers with Ignore health status are no longer counted
- Fix bug related to denied subjects
- Add Exabeam UEBA filter
- Add partner licensing option
- Run forwarder analysis after updating managed filters
- Fix bug when unable to create managed filter if event log didn't exists on master
- Display buttons not after but before subscription and distributed subscription name
- Display short name instead of full name of event log name in details title
- Fix bug related to distributed subscriptions and LDAP filters
- Enable empty LDAP BaseDN
- Display DCs in UI for LDAP BaseDN
- Add button to display license info for easier license key request
- Fix bug when domain has no more controllers
- Add instructions to analysis takes too long warning message on how to override frequency of collector and forwarder analysis
Supercharger 19.1.4 (1/11/2019)
Supercharger 18.12.2 (12/5/2018)
Supercharger 17.6.19 (6/14/2017)
Supercharger 17.2.54 (2/17/2017)
4.2. End User License Agreement
IMPORTANT. PLEASE READ THIS LICENSE AGREEMENT BEFORE LOADING THE SOFTWARE ONTO YOUR COMPUTER/SERVER.
This End-User License Agreement (“EULA”) is a legal agreement between you (a single entity) and Monterey Technology Group, Inc. (“Licensor”) for the license of the Software from Licensor accompanying this EULA. If you have entered into an agreement with Licensor, this EULA supplements and is a part of your agreement and is incorporated into your agreement. If you have not yet entered into any other agreement or contract with Licensor, this EULA is a binding, independent legal agreement between you and Licensor. By clicking “I agree,” or by installing, copying, modifying, registering, or otherwise using the Software, you agree to be bound by the terms of this EULA.
If you do not agree to accept all of the terms of this EULA, without any changes, additions or subtractions, please promptly click “I do not agree,” uninstall and remove the Software from your system, all of your computer(s), server(s), and/or your network, and return the Software to Licensor.
DEFINITIONS:
The following definitions apply to terms as they appear in this EULA:
- “EULA” means this End-User License Agreement.
- “Software” means the software accompanied by this EULA.
- “Licensor” means Monterey Technology Group, Inc.
- “You” means you, a single entity.
- “computer” and “server” each mean a single computer server.
THE SOFTWARE:
The Software is owned by and the property of Licensor. The Software is protected by the copyright laws of the United States of America, as well as international treaties protecting copyrights, as well as other intellectual property laws and treaties. While Licensor continues to own the Software, you will be granted, under this EULA, certain limited rights only to use the Software after your acceptance of this EULA.
LICENSE GRANT:
This EULA grants you the following rights:
- For any Microsoft Exchange environment where this software is used, this software must be licensed for the total active user accounts with mailboxes.
- Notwithstanding the foregoing, You may make one copy of the Software for archival purposes, or copy the Software onto the hard disk of your server as a single copy and retain the original for archival purposes. In the event that you make such a copy, you must ensure that the proprietary, copyright, trademark or other such notices contained in or placed on the Software are affixed to any such copy in the same location and manner as it appears in or on the Software.
- You may, after prior written notice to Licensor and Licensor’s consent, which shall not be unreasonably withheld, transfer the Software on a permanent basis to another person or entity, provided that you retain no copies of the Software and that the transferee agrees to all of the terms of this agreement and provides written notice of its agreement to Licensor.
- You may only use the Software for commercial purposes, and not for personal or household use.
DESCRIPTION OF OTHER RIGHTS AND LIMITATIONS:
- You may not copy any documentation which accompanies the Software.
- You may not sublicense, rent, or lease the Software, in part or in whole, or host the Software on your server for others to use. You may not allow the use of the Software as a service bureau.
- You may not reverse engineer, decompile, disassemble, modify, adapt, alter, integrate, translate, convert into human readable form, or make any attempt to discover, view or read the source code of the Software. You may not create derivative works, modifications or improvements to, of, from or on the Software.
- The Software is a single product. It may not be separated into its individual parts for use on any other server or computer.
- You may not transfer the Software to any third party without the prior written consent of Licensor.
- You may not use a previous version or copy of the Software after you have received a replacement or an upgraded version as a replacement of the Software. All copies of any prior version must be destroyed.
- Software installation, setup and maintenance is your sole responsibility. Licensor shall have no obligation or responsibility for software installation, setup or maintenance.
- You agree and grant Licensor the right to enter your premises and to access electronically at any time your server/computer as installed in order to verify your compliance with this EULA.
- All rights not expressly granted are reserved by Licensor. This EULA does not grant you any rights in connection with any copyrights, trademarks or service marks of Licensor.
- The Software may include copy protection or sunset technology to prevent the unauthorized copying or use of the Software. You agree that you will not circumvent any copy protection technology in the Software.
- This EULA does not require Licensor to provide to you any maintenance, updates, new versions, or support services related to the Software. The Licensor may or may not support the Software or any particular versions of the Software. Any services provided by Licensor, if any, may be described in the governing services agreement. Any supplemental software code, updates, modifications, or upgrades provided to you, whether as part of any support services or otherwise, are considered part of the Software and subject to the terms and conditions of this EULA. You acknowledge and agree that Licensor may use for its business purposes, including product support and development, any information you provide to Licensor whether the provision occurs during any support services, warranty claim or otherwise.
- Without prejudice to any other rights, Licensor may immediately terminate without notice this EULA if you fail to comply with any terms or conditions of this EULA.
- Returns and refunds are not accepted.
- You agree that you will not use the Software for any non-commercial purposes. You agree that you will not use the Software for personal or household purposes.
- You represent that you are authorized on behalf of your business or enterprise to enter into this EULA.
- You agree that you will not, during or after the termination of this EULA, contest or challenge Licensor’s ownership of, or interest in, the Software.
- You may not remove any copyright or other proprietary rights notices on any label of disks or other storage media containing the Software or in any documentation for the Software. You shall ensure that Licensor’s copyright and proprietary rights notices are not disabled and remain conspicuously displayed as provided in the Software.
UPGRADES:
Any are subject to all terms and conditions of this EULA.
INTELLECTUAL PROPERTY RIGHTS:
The Software, including but not limited to any and all source code, object code, software product, images, audio files, photographs, animations, macros, applets, video, music, text, the accompanying printed materials, related instructional material (whether in the Software, provided with the Software, or available concerning the Software), and documentation, is copyrighted with all rights reserved. You agree that Licensor, or third parties where appropriate, own(s) all rights to and in the Software, including without limitation all copyrights, proprietary rights, trademarks, service marks, patents, patent rights and trade secrets, as well as any and all such things for any modifications, derivatives, or improvements of the Software, or any part thereof, which you, Licensor, or others may make (in whole or in part), whether authorized or not.
NO WARRANTY:
The Software is provided as is and without any warranty.
DISCLAIMER OF WARRANTIES:
Licensor does not warrant any specific level of system functionality, availability or up-time.
LICENSOR HEREBY DISCLAIMS, AND DOES NOT MAKE, ANY AND ALL EXPRESS, IMPLIED, AND STATUTORY WARRANTIES, INCLUDING WITHOUT LIMITATION ANY IMPLIED WARRANTIES, DUTIES OR CONDITIONS OF MERCHANTABILITY, OF FITNESS FOR A PARTICULAR PURPOSE, OF ACCURACY OR COMPLETENESS OF RESPONSES, OF RESULTS, OF WORKMANLIKE EFFORT, OF LACK OF VIRUSES, OF LACK OF NEGLIGENCE AND OF NON-INFRINGEMENT. WITH RESPECT TO THE SOFTWARE, THERE IS NO WARRANTY OR CONDITION OF TITLE, QUIET ENJOYMENT, QUIET POSSESSION, CORRESPONDENCE TO DESCRIPTION OR NON-INFRINGEMENT. On occasion, all software has glitches or unforeseen errors, and consequently, Licensor makes no warranties and disclaims any and all warranties that the Software will function without interruption.
EXCLUSION OF INCIDENTAL, CONSEQUENTIAL AND CERTAIN OTHER DAMAGES:
TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, IN NO EVENT SHALL LICENSOR BE LIABLE FOR ANY SPECIAL, INCIDENTAL, INDIRECT, OR CONSEQUENTIAL DAMAGES WHATSOEVER (INCLUDING, BUT NOT LIMITED TO, DAMAGES FOR LOSS OF PROFITS OR CONFIDENTIAL OR OTHER INFORMATION, FOR BUSINESS INTERRUPTION, FOR PERSONAL INJURY, FOR LOSS OF PRIVACY, FOR FAILURE TO MEET ANY DUTY INCLUDING OF GOOD FAITH OR OF REASONABLE CARE, FOR NEGLIGENCE, FOR LOSS OF DATA, AND FOR ANY OTHER PECUNIARY OR OTHER LOSS WHATSOEVER) ARISING OUT OF OR IN ANY WAY RELATED TO THE USE OF OR INABILITY TO USE THE SOFTWARE, THE PROVISION OF OR FAILURE TO PROVIDE SUPPORT SERVICES, OR OTHERWISE UNDER OR IN CONNECTION WITH ANY PROVISION OF THIS EULA, EVEN IN THE EVENT OF THE FAULT, TORT (INCLUDING NEGLIGENCE), STRICT LIABILITY, BREACH OF CONTRACT OR BREACH OF WARRANTY OF LICENSOR, AND EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
LIMITATION OF LIABILITY AND REMEDIES:
NOTWITHSTANDING ANY DAMAGES THAT YOU MIGHT INCUR FOR ANY REASON WHATSOEVER (INCLUDING, WITHOUT LIMITATION, ALL DAMAGES REFERENCED ABOVE AND ALL DIRECT OR GENERAL DAMAGES), THE ENTIRE LIABILITY OF LICENSOR WHETHER UNDER ANY PROVISION OF THIS EULA, OR FROM ANY OTHER SOURCE OF LIABILITY, WHETHER IN CONTRACT OR IN TORT, INCLUDING NEGLIGENCE, AND YOUR EXCLUSIVE REMEDY FOR ALL OF THE FOREGOING (EXCEPT FOR ANY REMEDY OF REPAIR OR REPLACEMENT ELECTED BY LICENSOR WITH RESPECT TO ANY BREACH OF THE LIMITED WARRANTY), SHALL BE LIMITED TO THE AMOUNT ACTUALLY PAID, WITHIN THE ONE (1) CALENDAR YEAR PRECEDING THE TIME YOU MAKE A CLAIM TO LICENSOR OF SUCH DAMAGES, BY YOU TO LICENSOR FOR THE SOFTWARE THAT CAUSED THE DAMAGES OR THAT IS THE SUBJECT MATTER OF OR DIRECTLY RELATED TO THE CAUSE OF ACTION. IN NO EVENT WILL LICENSOR BE LIABLE FOR ANY DAMAGES CAUSED, IN PART OR IN WHOLE, BY YOUR FAILURE TO PERFORM YOUR OBLIGATIONS, OR FOR ANY LOSS OF DATA, PROFITS, SAVINGS, OR ANY OTHER CONSEQUENTIAL OR INCIDENTAL DAMAGES, OR FOR ANY CLAIMS BY YOU BASED UPON A THIRD-PARTY CLAIM.
SOME STATES DO NOT ALLOW THE LIMITATION OR EXCLUSION OF LIABILITY FOR CERTAIN TYPES OF DAMAGES, SO THE ABOVE LIMITATIONS OR EXCLUSIONS MAY OR MAY NOT APPLY TO YOU. THE PROVISIONS IN THIS PARAGRAPH WILL APPLY REGARDLESS OF WHETHER YOU ACCEPT THE SOFTWARE.
YOUR EXCLUSIVE REMEDY:
Licensors sole obligation and entire liability, if any, shall be, at Licensors option from time to time exercised subject to applicable law, to repair or replace the Software, so long as you return the original Software. If such a remedy is elected by Licensor, you are responsible for any expenses you may incur (e.g. cost of shipping Software to Licensor). Any replaced parts shall become the property of Licensor. Any replaced Software will be warranted with the same limited warranty set forth above for the longer of the amount of time left in the original warranty period or thirty (30) days. To exercise your remedy, contact Licensor at the address listed below.
CONFIDENTIALITY:
You acknowledge the Software, including its source code and know-how relating to such things, constitute confidential information of Licensor (collectively, “Confidential Information”). You (“Disclosee”) will therefore: (a) will take reasonable steps (including those steps that the Disclosee takes to protect its own information that it regards as confidential) to keep the Confidential Information confidential; and (b) will not disclose or otherwise make available, except as otherwise provided by law, the Confidential Information of the other party to any third party except to such directors, officers, employees and agents of the Disclosee who have a need to have access to the Confidential Information of the other party to perform their obligations to the other party under this EULA. The confidentiality provisions of this paragraph will not apply to Confidential Information that: (a) is in the public domain other than as a consequence of a breach of the obligations contained in this EULA to maintain the confidentiality of such Confidential Information; (b) is established by Disclosee’s documents as being known by the Disclosee prior to its disclosure to the Disclosee hereunder or is independently developed by the Disclosee without breach of the obligations contained in this EULA; or (c) has been received by the Disclosee from a third party who is not subject to obligations similar to the obligations contained in this EULA. In the event that the Disclosee receives notice indicating that it may or will be legally compelled to disclose any of the Confidential Information, it will provide Licensor with prompt notice so that the Licensor may at its sole discretion seek a protective order or other appropriate remedy and/or waive compliance with the provisions of this EULA. In the event that such protective order or other remedy is not obtained for whatever reason, or that such other party waives compliance with the provisions of this EULA, the Disclosee may furnish only that portion of the Confidential Information that he or she is legally required to disclose. The foregoing agreements and covenants set forth in this paragraph will be construed as being an agreement independent of the provisions in this EULA. The existence of any claim or cause of action of either party against the other party, whether predicated on this EULA or otherwise, shall not constitute a defense to the enforcement by such other party of any of the covenants and agreements of this paragraph. Each of the parties acknowledges that its failure to comply with the provisions of this paragraph will cause irreparable harm to the other party which cannot be adequately compensated for in damages, and accordingly acknowledges that the other party will be entitled, in addition to any other remedies available to it, to interlocutory and permanent injunction relief to restrain any anticipated, present or continuing breach of this paragraph.
In the event you breach this EULA, Licensor shall have the right, at its sole option, to terminate this EULA or any portion of this EULA, in addition to any other available remedies.
Upon Termination of this EULA. Upon the termination of this EULA: (a) Your confidentiality obligations, as well as any accrued payment obligations to Licensor, shall survive such termination; (b) your license right to the Software shall immediately cease, and (c) you shall: (i) return to Licensor all copies of and media bearing the Software within 10 business days; (ii) delete and erase any copy of the Software copied onto any computer/server pursuant to this EULA; (iii) erase all backup and archival copies of the Software; and (iv) certify in writing to Licensor within ten (10) business days of the termination of this EULA that all copies of the Software have been returned to Licensor or have been erased. You further authorize Licensor, in the event of termination of this EULA, to remotely and/or electronically disable, delete and/or remove the Software from your computer(s), server(s), and system(s). Termination of this EULA shall not limit either party from pursuing other remedies available to it, including injunctive relief, nor shall such termination relieve you from your obligation to pay fees accrued prior to the termination.
MISCELLANEOUS:
If applicable and unless overridden by a separate agreement, this EULA is incorporated into the agreement you have reached with Licensor for the Software, and in the event of any conflict between the terms of such agreement and this EULA, the terms of this EULA shall prevail and govern.
You acknowledge that the Software is of U.S. origin. You agree to comply with all applicable international and national laws that apply to the Software, including the U.S. Export Administration Regulations, as well as end-user, end-use and destination restrictions issued by the U.S. and other governments.
This EULA is governed by the laws of the State of North Carolina. This EULA may only be modified by a writing signed by both you and Licensor.
Disputes concerning or arising out of this EULA shall be submitted to confidential binding arbitration in Greensboro, North Carolina before the Judicial Arbitration and Mediation Service (“JAMS”) pursuant to the Streamlined JAMS Arbitration Rules and Procedures. Each party hereto submits to the jurisdiction of JAMS at the location so indicated above. Any process served in connection with any proceeding arising out of or relating to this EULA may be served upon the party to be served by registered or certified mail at the address listed above. Any such service will have the same effect as personal service within the states so indicated above. The foregoing shall not preclude any party hereto from seeking enforcement outside the relevant state of the arbitration of any order or judgment rendered by any court upon the JAMS award.
Except as expressly provided in this EULA, no amendment or waiver of this EULA shall be binding unless executed in writing by the Customer and Licensor. No waiver of any provision of this EULA shall constitute a waiver of any other provision nor shall any waiver of any provision of this EULA constitute a continuing waiver unless otherwise expressly provided.
If any provisions of this EULA shall for any reason be held illegal or unenforceable, such provision shall be deemed separable from the remaining provisions of this EULA and shall in no way affect or impair the validity or the enforceability of the remaining provisions of this EULA.
This EULA constitutes the entire agreement between the parties pertaining to the subject matter hereof. There are no warranties, conditions, or representations (including any that may be implied by statute) and there are no agreements in connection with such subject matter except as specifically set forth or referred to in this EULA.
Should you have any questions concerning this EULA, or if you desire to contact Licensor for any reason, please send a written communication to: rsmith@montereytechgroup.com.
4.3. Annual Support and Maintenance Terms and Conditions
Coverage
Purchase of an Annual Support and Maintenance Agreement (Agreement) covers:
- Updates. Availability announcements of updates are sent to the email address on the Certificate.
- Technical support (excluding consulting). Support is initiated by creating a ticket at https://logbinder.helpspot.com. Subsequent phone or web conferences will be arranged as deemed necessary by our support. Licensee may be asked for certificate number before being provided support.
- Support is available 9am-5pm Eastern US time Monday – Friday.
- 24 hour response time. Failure: 1 month of PSM refunded for each day missed. If not solved within 48 hours, customer can request to escalate the issue to LOGbinder's Development Triage Team who will classify the issue as:
- LOGbinder product defect
- Environment specific issue
- Microsoft product defect
Regardless of the classification we will make our best effort to solve or create a work around at which time a case-specific patch or product update will be provided. (To date we've only classified one issue as environment specific and we solved it in the next release of the software.)
- Credit towards the purchase of a higher-level license and Support and Maintenance Agreement. This includes the original software cost and the unused portion of this Support and Maintenance Agreement (pro-rated and applied to the maintenance fee for the higher-level license).
Pricing
Annual Support and Maintenance Agreements can be purchased in 1, 2 or 3 year increments.
| Years | Amount |
| 1 | 20% of software list price |
| 2 | 38% of software list price |
| 3 | 54% of software list price |
Terms and Conditions
Renewal: We will email the technical contact and business contact we have on record at least 30 days prior to expiration to arrange renewal. (We will likely begin reminding you 90 days before expiration as well as send a fax to your main office.) Unless you renew, this Agreement automatically expires on midnight of the expiration date.
The cost of the Support and Maintenance Agreement will be based on the list price of the software at the time of the purchase. After that period, the cost to renew the Support and Maintenance Agreement will be based on the list price of the software at the time of each renewal.
Please note that lapses in Support and Maintenance Agreements are not allowed. In the case where a Support and Maintenance Agreement expired, any future renewals of said agreement will begin on the day following the original expiration date.
Cancellation: The Agreement can be canceled at any time in writing by e-mail, fax or letter. In case of cancellation, Monterey Technology Group, Inc. will not pro-rate or issue any refunds for any unused time on this agreement.
4.4. "Real Training for Free" Webinars
Click here for access to some of Randy Franklin Smith's "real training for free" webinars.
5. How To
5.1. How to Find Frequently Ran EXEs Causing Event ID 4688 Noise
Event ID 4688 is valuable because it allows us to track EXEs running on our endpoints and even detect unrecognized programs such as those in WannaCry. But 4688 is noisy. Supercharger includes noise filters for the most common EXEs executed by the system (Logon ID 0x3e7) but you can cut down the noise even more in your environment by analyzing 4688s. Here are some Log Parser scripts to help you do that
logparser "select EXTRACT_TOKEN(Strings,5,'|') AS Program, count(*) from security where EventID=4688 group by program order by count(*) desc" -o:tsv > CountsByProgram.txt
logparser "select EXTRACT_TOKEN(Strings,5,'|') AS Program, EXTRACT_TOKEN(Strings,3,'|') AS logonId, count(*) from security where EventID=4688 and logonid='0x3e7' group by program, logonid order by count(*) desc" -o:tsv > ProgramsRanBySystem.txt
logparser "select EXTRACT_TOKEN(Strings,5,'|') AS Program, EXTRACT_TOKEN(Strings,1,'|') AS theuser, count(*) from security where EventID=4688 group by program, theuser order by count(*) desc" -o:tsv > ProgramsByUser.txt
Each command creates a tab delimited file you can view in Excel.
Here a link to a video about putting this information to work.
5.2. Collecting Process Start Events (4688) Without the Noise
If everyone monitored security event ID 4688 (New process) on each computer, we would know within seconds whenever a EXE showed up on the network. If we knew that, we would be able to stop so many more intrusions – so much sooner in the process – before damage is done. This one security measure would catch so many ransomware, APT and information theft attacks.
Sound like a lot of work? It was, before Supercharger…
In 5 minutes Supercharger can configure Windows Event Collection so that your endpoints start sending this to a central Windows event collector. Which you then monitor with the SIEM of your choice. No agents, no polling, no remote access credentials to setup, no firewall rules to configure. It just works.
Worried that collecting every process start event from every Windows system would be overwhelming? Turn on Supercharger’s built-in Common System Process noise filter and suddenly all those endpoints reduce traffic to a fraction. That’s because the lion’s share of process start events (4688) are just noise in terms of attack detection. We know for instance that Windows runs C:\Windows\System32\svchost.exe all the time. As long as the Logon ID is 0x3e7 there’s really no point in analyzing the event.
Supercharger was designed by Randy Franklin Smith – no one knows the Windows Security Log better – and you get to leverage his knowledge built-in to Supercharger. Check out this video where Randy demonstrates the steps in less than 7 minutes.
You might need to right-click and select Play or Show Controls on the video below.
5.3. After installation Supercharger displays "Please provide credentials to an existing Supercharger database or location where a new Supercharger database will be created"
After installation Supercharger displays a Database State page with "Please provide credentials to an existing Supercharger database or location where a new Supercharger database will be created"
This usually indicates on of the following reasons. Please use the suggested steps to resolve. It will help to install SQL Server Management Studio to perform most of the steps.
SQL Server 2016 is already installed
- Enable SQL Authentication (mixed mode) https://docs.microsoft.com/en-us/sql/database-engine/configure-windows/change-server-authentication-mode
- Run the following commands to create a user account for Supercharger. Specify a secure password in place of ????????????????
USE MASTER
CREATE LOGIN ScManagerDbUser WITH PASSWORD=N'????????????????', CHECK_EXPIRATION=OFF
GRANT CONNECT ANY DATABASE TO ScManagerDbUser
ALTER SERVER ROLE [sysadmin] ADD MEMBER ScManagerDbUser
- Open Supercharger in your browser
- Provide the name SQL Server (localhost) including instance if applicable. If default instance just put localhost. (If SQL Server certificate is used, provide the same FQDN as in the CN of the certificate.)
- Specify the username and password from above
- Click Continue
SQL Server 2016 was installed, uninstalled
- Uninstall Supercharger
- Open Registry Editor
- Delete HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\130
- Re-install Supercharger
Another version of SQL Server is installed which is using port 1433
If the other version of SQL Server isn't needed stop the service.
If the other version of SQL Server is required then
- Enable and start SQL Browser service
- Re-configure SQL Server 2016 Express instance of SUPERCHARGER to use dynamic ports by setting the IPAII Dynamic Port to 0 (zero). https://docs.microsoft.com/en-us/sql/database-engine/configure-windows/configure-a-server-to-listen-on-a-specific-tcp-port
- Restart SQL Server 2016 Express
- Restart Supercharger Controller service
- Open Supercharger in your browser. After creating the database, the application should come up as normal
5.4. Customer Installed SQL Server
NOTE: The instructions below apply if you are setting up a new installation of Supercharger and want to use your own SQL Server and not the SQL Server that installs by default with Supercharger. If you already have Supercharger installed and configured and need to migrate Supercharger data (load balancers, load balanced subscriptions, performance history, etc...) to another SQL Server, then please see this article.
We strongly recommend that you use the SQL Server that installs by default with Supercharger.
Supercharger does not use SQL Server in the traditional sense as a relational database nor does it store the organization’s business data or data normally considered to be specifically scoped into compliance regulations. Supercharger’s use of SQL server is for storage of system information and as a inter-process communication facility between manager and controllers.
Supercharger is designed to use a local instance of SQL Server Express 2016 to store:
- Status of Windows Event Collectors
- Performance monitoring data
- Windows Event Collection configuration settings
Supercharger automatically installs, secures and configures SQL Server Express on the manager. For Free Edition, we do not offer support for using a different installation of SQL Server. For Enterprise Edition customers with an active support contract, we may support, on a case-by-base basis at our sole determination, to support a customer installed instance of SQL server on another system. These are instructions related to such a scenario.
Requirements:
- Mixed Mode Authentication
- SQL Server login with sysadmin role membership which is used to: creates database, back up database, creates logins for each collector, alters database to single/multi user etc, connect to any database
We believe Supercharger will work OK on a day-to-day basis without sysadmin but it is required whenever you register a new Windows Event Collector or upgrade Supercharger to a new version. Supercharger should also work with most earlier versions of SQL Server including 2014.
- Make sure SQL Authentication is enabled (mixed mode) https://docs.microsoft.com/en-us/sql/database-engine/configure-windows/change-server-authentication-mode
- Run the following commands to create a user account for Supercharger. Specify a secure password in place of ????????????????
USE MASTER
CREATE LOGIN ScManagerDbUser WITH PASSWORD=N'????????????????', CHECK_EXPIRATION=OFF
GRANT CONNECT ANY DATABASE TO ScManagerDbUser
ALTER SERVER ROLE [sysadmin] ADD MEMBER ScManagerDbUser
Installing Supercharger:
- If you already installed Supercharger and it installed SQL Server 2016 Express, to cause Supercharger to prompt you for new SQL coordinates and credentials, uninstall SQL Server Express 2016 and proceed to the next step. If you have not already installed Supercharger, create this registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server\130. This will make the installer think SQL Server 2016 is already installed and will skip it.
- Open Supercharger in your browser. //server/supercharger. Eventually it will display a page saying it cannot connect to the SQL Server and it will give you an opportunity to enter SQL Server coordinates and credentials. It may take a couple minutes for this page to appear but it will. (If for some reason it does not appear, you can open the database coordinates settings page by opening http://localhost/trouble/credscoords in your browser.)
See next steps for guidance on server and credentials but note there is a slight chance in some browser versions that it will interrupt you while entering the information and you will have to start over. We are working to address this but be aware for now. - Provide the name SQL Server (localhost) including instance if applicable.
- If using a default instance of SQL Server installed locally just put localhost
- If SQL Server certificate is used, provide the same FQDN as in the CN of the certificate
- If the appropriate SQL Server instance uses a custom port number append a comma and the port number to the server name. There is no need to specify the instance. So if your server name is lab-scsql-70 and port is 1521 you would simply enter lab-scsql-70,1521
- Specify the database name, which should be Supercharger by default
- Specify the user name (ScManagerDbUser) and password from above
- Click Continue
- If the coordinates and credentials work, the manager will now connect to the SQL Server and, if not present, create the Supercharger database. Finally the dashboard will be displayed.
5.5. Collecting PowerShell Logs
Here's a 4 minute video showing you how to setup a custom destination log and subscription for PowerShell events.
5.6. All subscriptions have 0 active forwarders; System Event IDs 10128, 10129
None of the subscriptions on a collector have any active forwarders (sources). Everything appears to be correct. Events were forwarding before. System event log shows error events 10128 and 10129. This also helps when the eventforwarding log has error 105 with code 2150859027.
Samples
- The WinRM service is not listening for HTTP requests because there was a failure binding to the URL (http://+:5985/wsman/SubscriptionManager/WEC) in HTTP.SYS.
- The WS-Management client is not listening for pushed events because there was a failure binding to the URL (http://+:5985/wsman/subscriptions/C66628DA-E0B8-43BF-A210-C4B685C23608) in HTTP.SYS.
Run netsh http show urlacl and find the URL mentioned in 10128. Take note of the SDDL for that URL.
Go to another collector that is working correctly. Run the same command. Compare the SDDL to that from the problem collector.
In our case the problem collector (Win2016) was
Reserved URL: http://+:5985/wsman/
User: NT SERVICE\WinRM
Listen: Yes
Delegate: No
SDDL: D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)
But on a functioning collector (happened to be Win2012r2) it was
Reserved URL: http://+:5985/wsman/
User: NT SERVICE\WinRM
Listen: Yes
Delegate: No
User: NT SERVICE\Wecsvc
Listen: Yes
Delegate: No
SDDL: D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)(A;;GX;;;S-1-5-80-4059739203-877974739-1245631912-527174227-2996563517)
Also, the default for Win2016 and 2019 is:
Reserved URL: http://+:5985/wsman/
User: NT SERVICE\WinRM
Listen: Yes
Delegate: No
SDDL: D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)
We ran from administrator command prompt (cmd, not PowerShell) the following
netsh http delete urlacl url=http://+:5985/wsman/
netsh http add urlacl url=http://+:5985/wsman/ sddl=D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)(A;;GX;;;S-1-5-80-4059739203-877974739-1245631912-527174227-2996563517)
and that fixed it immediately. Maybe we restarted the winrm and wec.
5.7. How to Keep Subscriptions in Healthy State Even Though Some Workstations Are Shut Down Outside of Work Hours
Each subscription policy has a Heartbeat Interval (3,600,000 milliseconds by default) to monitor its forwarders' health status. For more information on this, please refer to the article on Forwarder Analysis.
However, workstations might be shut down for the night or for the weekend. During this time, no heartbeat is received from these forwarders, which will show their WEC status inactive, indicating that there is a problem with these forwarder. This, in turn, can put a subscription into an unhealthy state, even though all running computers are actively forwarding.
If these workstations should not be seen unhealthy just because they don't report in during the night or over the weekend, the Ignore No Heartbeat (Hrs) option can be set in the subscription policy. This option is zero by default, which means that it will be ignored. If set to a number greater than zero, the forwarders in that subscription will be considered healthy for the specified number of hours, even if no heartbeat is received from them. For example, if this option is set to, let's say, 16 hours, the forwarders will be considered healthy by Supercharger, even though the workstation is shut down for the night.
This setting can be modified in Supercharger by clicking on Settings then Subscription Policies and then Editing the subscription policy you are using.
5.8. How To Use LDAP Filters in Deterministic Subscription Policies
Deterministic subscription policies normally use the groups in Allowed Forwarder on the subscription to figure out the set of "expected" forwarders. However, one might only want to use only a subset of these computers at the collector.
For instance, some customers specify Domain Computers as Allowed Forwarders but then only point a subset of those computers at the collector with a group policy object linked to an organizational unit containing those computers. This means that deterministic forwarder analysis will always report all other computers outside that OU as problem status. This is a situation where you could use an LDAP filter to specify which computers should really be expected for a given subscription.
This subset can be defined using an LDAP filter. Setting the LDAP filter for a deterministic policy will tell Supercharger not to enumerate the members of all the groups on this subscription, only those defined by the LDAP filter.
To use LDAP filters in a subscription:
- Select a deterministic policy under the Policy tab.
- Using the slider that appears, change the Deterministic Criteria from Group Name to LDAP Query.
- Select a predefined LDAP query (see below how to define LDAP queries).
To use LDAP filters in a load balanced subscription:
- Under Cohort based on, select LDAP Query.
- Select a predefined LDAP query (see below how to define LDAP queries).
To define LDAP queries:
- Go to Settings.
- Select the LDAP Queries tab, and click on the Add button.
- Specify a name, the domain, a base DN, and the LDAP filter.
For the full syntax of LDAP filters, see, for example, the Search Filter Syntax MSDN article and the Active Directory: LDAP Syntax Filters TechNet wiki article. In Supercharger, of course, only filters in the following format can be used: (&(objectCategory=computer)_________) You can test LDAP filters in Powershell with the Get-ADComputer cmdlet, using the LDAPFilter parameter.
Some examples of LDAP filters:
- To include all computers under that base DN:
(&(objectCategory=computer)(name=*)) - To include all computers with name starting with "desktop":
(&(objectCategory=computer)(name=desktop*)) - To include all computers with a description:
(&(objectCategory=computer)(description=*)) - To include all computers with no description:
(&(objectCategory=computer)(!(description=*))) - To include all computers with a description and with name including the word "desktop":
(&(objectCategory=computer)(name=*desktop*)(description=*)) - To include all computers with name including either "desktop" or "laptop":
(&(objectCategory=computer)(|(name=*desktop*)(name=*laptop*))) - To include all computers with operating system Windows Server 2012 R2:
(&(objectCategory=computer)(operatingSystem=Windows Server 2012 R2*)) - To include all servers:
(&(objectCategory=computer)(operatingSystem=*server*))
To test LDAP queries there are many ways. One way is using Active Directory Users and Computers. Right click on the domain, select Find then click on "Custom Search" in the dropdown and then Advanced. You can paste in your LDAP query by clicking "Find Now' and seeing if AD finds any results. If you get no items, it doesn't necessarily mean that your LDAP is incorrectly formatted. On the other hand, if you do get results then you can be certain the LDAP is formatted correctly.
5.9. Controlling Which Computers Subscribe to a WEC Subscription
The simplest and most direct way to control which computers subscribe to a subscription on your Windows Event Collector is to use an Active Directory group that has those computers as members. Just make sure that a group policy object (GPO) that applies to at least those computers (it's fine if the GPO hits other computers in the domain) includes an entry in the Target Subscription Managers policy that points to Windows Event Collector server where you subscription resides. Then assign that group under Allowed Forwarders on the subscription and all computers belonging to that group will subscribe to the subscription after applying the group policy.
For most environments except perhaps very large enterprises, we recommend that you simply target all the computers in your domain to all of your WEC collectors. This is easy to do. Just add an entry in Target Subscription Managers policy for each Windows Event Collector. (see Target Computers at the Collector) Then use groups to assign computers to appropriate subscriptions on any collector. The Refresh interval defaults to 15 minutes (900 seconds) which keeps bandwidth and other resource utilization low even if you have many computers and collectors.
If, for whatever reason, you can't use a group to control which computers subscribe to your subscription, you can use an alternative approach which relies on Organizational Units and more group policy objects. In this case you define a set of computers that should subscribe to a given subscription with one or more OUs. Create a GPO and link it to the OU(s) and add just one entry to the Target Subscription Managers policy that points to the Windows Event Collector where your subscription resides. Then on the subscription, under Allowed Forwarders, you assign Domain Computers. If you wish to monitor the health of the subscription with Deterministic Health Analysis, you will need to define an LDAP filter that corresponds to the computers in the OU(s). Following this model consistently means basically that a computer subscribes to all the subscriptions on whichever collector it is pointed to by group policy based on the OU where the computer currently resides. Move the computer to another OU and will re-subscribe to the subscriptions on the collector where that OU is pointed.
5.10. How To Backup and Restore Supercharger for Disaster Recovery
Manager
How To Backup the Manager
(If using the SQL Server installed by Supercharger, you can use any account in the BUILTIN\Administrators group, as that group is added to the sysadmin role for the SQL Server installation.)
- Backup the master database (see Back Up and Restore of System Databases)
- Backup the Supercharger database (see Back Up and Restore of SQL Server Databases)
How To Restore the Manager
- Install Supercharger manager on the new server
- Stop the Supercharger service
- Restart the SQL Server in single-user mode
- Restore the master database that was backed up (see Back Up and Restore of System Databases)
- Start the SQL Server without single-user mode
- Restore the Supercharger database that was backed up (see Back Up and Restore of SQL Server Databases)
- Run the following SQL commands to reset the user account for Supercharger. (You can put the commands in a text file and run from admin command prompt: sqlcmd -H localhost -i TextFileName)
Specify a secure password in place of ????????????????USE MASTER;
DROP LOGIN ScManagerDbUser;
CREATE LOGIN ScManagerDbUser WITH PASSWORD=N'????????????????', CHECK_EXPIRATION=OFF;
GRANT CONNECT ANY DATABASE TO ScManagerDbUser;
ALTER SERVER ROLE [sysadmin] ADD MEMBER ScManagerDbUser - Configure the new password in Supercharger
- Open Supercharger in your browser. It will complain about bad credentials
- Click on the Configure button to go to the database coordinates settings page
- If you get an HTTP error message instead of the database connection Supercharger error page, you can open the database coordinates settings page by opening http://localhost/trouble/credscoords in your browser
- Provide the name of the SQL Server including instance if applicable. If using default instance, just put localhost. (If SQL Server certificate is used, provide the same FQDN as in the CN of the certificate.)
- Specify the database name, which should be Supercharger by default
- Specify the user name (ScManagerDbUser) and password from above
- Click Continue
- Reconnect collectors
- If the new manager has same DNS name as old manager, then collectors should just reconnect automatically
- If the new manager has a different DNS then before, then the Server name of the manager needs to be changed in registry for each collector under the following key
- HKEY_LOCAL_MACHINE\SOFTWARE\MTG\Supercharger\Controller\Db
Collectors
How To Backup a Collector
Collectors do not need to be backed up.
How To Restore a Collector
- Install the Supercharger agent
- Re-register with Supercharger manager
Frequently Asked Questions
What data is lost when you restore a Manager?
When you restore the Supercharger SQL database, you will lose any changes to Supercharger objects (as opposed to WEC objects) since last backup. This includes policies, managed filters, security permissions, overrides, performance statistics, etc. This does not include Windows objects on collectors such as Subscriptions and Event Logs. This is because Supercharger always updates these objects in Supercharger to reflect Windows current state of each collector.
Can I use the above steps to migrate the Manager to another server?
Absolutely. Just make sure to rename the new server to the DNS of the original server sometime before restoring the Supercharger database (that is, before step 6 above).
Additional Useful References:
5.11. Ports used by Supercharger
- For all SQL commands between Supercharger Manager and Controllers
- Port 1433
- Prior to version 21.3.16: The only exception to this is when the collectors download a new version of the collector installer. In this case HTTPS (port 443) is tried first and if that doesn't connect then HTTP (port 80) is used.
- Starting from version 21.3.16: The new version of the collectors is downloaded from the database, so no additional port is required, unless downloading from the database failed for some reason.
- Port 1433
- All communication between web browsers and the Supercharger Manager
- Port 80 http
- The only exception is if a certificate has been configured to be used then port 443 https would be used.
- Port 80 http
All communication between the manager and controllers is initiated by the controllers. No connections are initiated from manager to controllers.
5.12. Troubleshooting Load Balanced Subscriptions
Occasionally an error may occur during the creation of a load balanced subscription. The overall CreateUpdateDistSubCmd (not exact name) failed at some point leaving the DistSub record in the DB with at least some of the Collectors attached to it. Then the daily MaintainDistSubCmd kicked off. This command compares the DB to what it finds on each assigned collector and it also checks groups and members and repairs anything that isn't match correctly.
All DistSub commands execute on the master collector for the domain (This is the first collector in the domain unless the role was moved. Please don’t confuse this with the manager). It submits commands to other collectors and waits for them to complete. It sees if one of those subcommands fails or doesn’t complete in a reasonable time. If this happens it fails the DistSub command.
The MaintainDistSubCmd runs at least every day. It compares the DistSub records and assigned subscriptions and groups in AD. It’s possible that something that didn’t get done earlier in the original CreateUpdateDistSubCmd could be completed in MaintainDistSubCmd at 1AM. For example, maybe the superset group of all forwarders for the DistSub had just been created in AD and not replicated to the DC used by the master collector due to a reboot or other issue. Or the member additions to the group had not replicated but the group was there. In the latter case the DistSub would be created but no forwarders assigned to each subscription’s group. Later when MaintainDistSubCmd runs and replication had occurred, the members would be there in AD and be distributed.
If you are having issue with a Load Balanced Subscription due to the DistSub command failing here are some common things to look for:
- One of the collectors is down
- AD OU permission or OU or replication problems
Here are some steps to help:
- From the master logs, please determine: Did the CreateUpdateDistSubCmd (not exact name)
- Complete successfully?
- Fail?
- Hang? (unlikely) but log would show neither a or b above
- If it failed – what reason?
- An exception within the logic of the CreateUpdateDistSubCmd itself, or
- A failure of a command it submitted to another collector?
- Timeout waiting on commands to be executed by another collector?
If 1.b or 1.c, get the logs from the other collectors associated with the Distributed Subscription. Should be a failed CreateUpdateSubCmd in one of them. What’s the error?
When CreateUpdateDistSubCmd fails it does not reverse out what it accomplished so far (for good reason). MaintainDistSubCmd will fix whatever didn’t complete – except one type of chance: the addition or deletion of a collector. Examples of what this means:
- You issue a CreateUpdateDistSub to create a NEW sub with 3 collectors assigned a, b ac. Everything goes well except one collector (c) is down or the local CreateUpdateSubscription command fails for whatever reason. What do you end up with? The command will fail but you will have a DistributedSubscription with 2 collectors assigned. Forwarders distributed between collectors a and b. To solve: edit the dist sub and add collector C
- You issue a CreateUpdateDistSub to remove or add one collector. But that collector is down or the command fails for whatever reason. No change to the DistSub is made. Just resubmit the command.
Because of the distributed nature of both AD and load balanced subs, failures like this can occur. But Supercharger is designed so that nothing becomes corrupted or inconsistent. The MaintainDistSubCmd command will always ensure that actual WEC subscriptions and the DB match. You can add or remove collectors that failed to be changed earlier.
5.13. Subscriptions are inactive
In Supercharger you may receive an error showing error 2144108374 and 2150858922.
The 2144108374 error is coming from the Runtime status of the WEC subscription having issues. In Event Viewer if you check the runtime status you may see this error code or you may see 0x803380AA. These codes are one in the same. The confusing part is WEC says the reason is to "Enable the WinRM firewall exception." You may waste countless hours checking and rechecking your firewall rules but this is most likely not the issue.
In the EventCollector\Operational log you will also see event id 2 saying that the subscriptoin could not be activated and that the error code is 2150858922. You will notice that on the subscription in Event Viewer that there is no option to activate the subscription.
Both of these errors are reported to the subscriptions status in Supercharger. The fix is very easy. In Supercharger open the subscription having the issue. Click on the green "Edit" button. Then click on the "Submit" button. This will, in effect, Activate the subscription. You will notice that the subscription should now turn green (or yellow if there are other issues) on the Supercharger dashboard. It will also now show as Active under Subscriptions in Event Viewer.
5.14. WinRM says "Unable to check the status of the firewall"
You may notice various errors such as:
Possible error #1
Error location: In Log -> Eventlog-ForwardingPlugin/Operational
Error code is 2150859027 and Error Message is <f:WSManFault xmlns:f="http://schemas.microsoft.com/wbem/wsman/1/wsmanfault" Code="2150859027" Machine="server.domain.org">
<f:Message>The WinRM client sent a request to an HTTP server and got a response saying the requested HTTP URL was not available. This is usually returned by a HTTP server that does not support the WS-Management protocol. </f:Message></f:WSManFault>.
Possible error #2
Error location: Powershell when running "WinRM QuickConfig"
D:\>winRm quickConfig
WinRM service is already running on this machine.
WSManFault
Message
ProviderFault
WSManFault
Message = Unable to check the status of the firewall.
Error number: -2147024894 0x80070002
The system cannot find the file specified.
Possible error #3
Error location: In Log -> Eventlog-ForwardingPlugin/Operational
The forwarder is having a problem communicating with subscription manager at address http://server.domain.org:5985/wsman/SubscriptionManager/WEC.
Error code is 5 and Error Message is <f:WSManFault xmlns:f="http://schemas.microsoft.com/wbem/wsman/1/wsmanfault" Code="5" Machine="server.domain.org">
<f:Message>Access is denied. </f:Message></f:WSManFault>
Solution
The default firewall rule may be corrupted or not functioning as expected.
Solution #1
Run the following command to create a new firewall rule for WinRM:
netsh advfirewall firewall add rule name="Windows Remote Management (HTTP-In)" dir=in action=allow service=any enable=yes profile=any localport=5985 protocol=tcp
Solution #2
Open the Windows Defender Firewall with Advanced Security MMC snap-in and use the Restore Default Policy action.
After the above, you might need to Retry your subscriptions in Event Viewer.
5.15. Using HTTPS with Windows Event Forwarding and Supercharger
We do not provide consulting for using WEC over HTTPS as part of Supercharger support contracts. The following information is provided as a courtesy and may not cover every detail or situation in your environment because of the complexity of PKI.
We will provide support on configuring the Supercharger IIS website to use HTTPS in terms of the local configuration of IIS. It is your responsibility to enroll the server with a valid server certificate and private key and import it. We do not provide support on PKI issues or certificate enrollment.
The following information may be of help.
There are two different areas where HTTPS may be used:
- Forwarding events with WEC using a https:// URL for the target subscription manager when you target computers at the collector
- Accessing the Supercharger GUI/Dashboard through HTTPS, for example, https://localhost/Supercharger
For #1 above there are a few things you have to do:
- Install a certificate for the server along with its private key. This can easily be done using an Enterprise CA in AD.
- The signing CA of the server certificate must be trusted by the forwarder computers.
- Make sure permission on the private key allow WinRM to access it.
- Create a firewall exception rule to allow data over port 5986.
- You may have to run "winrm qc -transport:https". This would have to be ran after the cert is installed and configured.
- Change the URL in target subscription manager to be https using port 5986
For #2 above there are many options to complete this. Configuring Supercharger to use HTTPS is the same as configuring HTTPS for any website. Your organization will have to determine which process meets its security requirements. Because of this, we do not provide a guide for setting up websites using HTTPS for every scenario as this is fully documented online from multiple resources. Below, though, are a few points to keep in mind. Here is a link to one scenario for "How To Setup Supercharger Web GUI for HTTPS".
- (You can use the same certificate as #1 above)
- Install a certificate for the server along with its private key. This can easily be done using an Enterprise CA in AD.
- The signing CA of the server certificate must be trusted by the client computers.
- The signing CA of the server certificate must be trusted by the forwarder computers.
- Make sure permission on the private key allow WinRM to access it.
- Create a firewall exception rule to allow data over port 443.
- Configure IIS to use the certificate for the Supercharger site.
5.16. Overriding global settings
Supercharger allows some of its global parameters to be overwritten by the user. Although these parameters have been carefully selected, at times it may be necessary to adjust them to your circumstances. For example, when the forwarder analysis or the collector analysis takes too long, you might want them to run less frequently.
These values can be changed under Settings / Overrides.
The following table contains some of the most frequently used settings:
| Setting | Explanation | Default | Units |
|---|---|---|---|
| AutomaticRebootEnabled | When set to True, automatically reboot a controller if WEC service on it has been unhealthy for AutomaticRebootAfterWecUnhealthyMinutes minutes. | False | |
| AutomaticRebootAfterWecUnhealthyMinutes | After the set minutes, automatically reboot a controller if WEC service on it has been unhealthy and AutomaticRebootEnabled is True. | 60 | minutes |
| DisableGroupPolicyChecks | When set to True, group policy information will not be collected. Group policy information is used to advise you on potential problems in the group policy settings that might influence event forwarding. | False | |
| DisableTrialLicenseEmails | When set to True, no warning emails will be sent about expired trial license. | False | |
| ExcludeDrivesWithCapacityBelowGb | Exclude from health checks hard drives below this capacity. If 0, don't exclude any. | 0 | GB |
| RecurCollectorAnalysisSeconds | How often collector analysis will run. | 900 | seconds |
| RecurForwarderAnalysisSeconds | How often forwarder analysis will run. | 900 | seconds |
| RecurMaintainLoadBalancersCommandSeconds | How often maintain load balancers command will run. | 3600 | seconds |
| WaitForRemoteCommandsToRunSeconds | How long to wait to complete remote commands for distributed subscription operations. | 5 | seconds |
5.17. How To Setup Supercharger Web GUI for HTTPS
There are many different ways to configure Supercharger to use HTTPs for its website. Configuring Supercharger to use HTTPS is the same as configuring HTTPS for any website. Your organization will have to determine which process meets its security requirements. Because of this, we do not provide a guide for every possible way on setting up websites using HTTPS. This is fully documented online from multiple resources. Below is one possible solution of many.
1. Install the "Active Directory Certificate Services" role on a domain server.
2. After installing the role perform the post-configuration steps.
3. Be sure to select Enterprise CA.
4. Select Root CA.
5. Create a new key. If you already have an existing key then you most likely don't need this article.
6. After configuration, open IE and go to http://localhost/certsrv and click on Request a Certificate.
7. Click on the "Submit a certificate request..." option. Leave this open. You will come back to it in a later step.
8. Open MMC and add Certificates add-in. Navigate to Personal and under actions go to All Tasks\Advanced Operations\Create Custom Report.
9. Click next and then select “Proceed without enrollment policy”.
10. Leave the defaults and click Next.
11. Expand the details and click properties. Give the certificate a friendly name and Description.
12. Click on the Subject tab and add the Common Name, OU, Organization, Locality, State and Country just as you would if you were requesting a normal certificate. The Common Name should be the hostname of the Supercharger Manager server. Then in the Alternative dropdown select DNS and add the FQDN of the Supercharger Manager server and also the hostname of the Supercharger Manager.
13. On the Extensions tab expand the Extended Key Usage section and add Server Authentication and Client Authentication and click Apply.
14. Click on Private Key tab and set the Key Options size to 2048 and set the key to be exportable.
15. Click Next and save the file name and set to Base 64.
16. Open the file that you just created using a text editor. Copy the Certificate Request content. Be sure to include the header and footer along with the request string.
11. Go back to the CA server from step 7. Paste in the request. Select Web Server from the dropdown.
12. You should get a Certificate Pending page.
13. Go back to the Certification Authority. In the Pending Certificates folder you should now see the cert. Go to tasks and issue the certificate.
14. Go back to IE and navigate to http://localhost/certsrv. Click on "View the status of a pending certificate request".
15. Select the certificate you just issued. On the next screen select "Base 64 encoded" and then download the certificate.
16. Save the certificate. Then copy the certificate to the Supercharger Manager server. Back in Personal\Certificates in MMC on the Supercharger Manager server, under Actions, click on All Tasks, then Import. Point the import to the certificate file you copied over and finish the import using default options.
17. Go to the Supercharger website in IIS under Sites. (Most likely named "Default Web Site"). Click on "Bindings" in the Actions menu. Add a binding for https. Select the new certificate in the dropdown. Save and then you may have to restart IIS service.
5.18. KerbPurge 101
KerbPurge - What is it?
When you add a computer to a group in Active Directory, the computer does not know that it has been added to the group until a reboot happens. There are many obvious reasons why this is a problem. For example, you can't just reboot production servers at any time. Most organizations have some sort process in place for scheduling server reboots which in itself can be a time consuming process. When it comes to Windows Event Collection there are many reasons for adding endpoint forwarders to groups, especially if you are using Supercharger. For example, Superchargers built-in load balanced or distributed subscription feature relies on group changes to keep forwarders balanced across the number of specified collectors. This is why Randy Franklin Smith of UltimateITSecurity.com designed and wrote KerbPurge.
Benefits and Features
- Safely and efficiently make Windows computers see group membership changes
- Tiny Windows service
- Installable via Group Policy's Software Installation feature
- Only purges tickets for the Network Service logon session and only when group membership has been changed for a computer
- No measurable resource usage
Installation and Configuration
- Download KerbPurge from the Utilities section at LOGbinder.com and copy to a folder on your domain controller.
- On your Domain Controller, open Group Policy Management.
- Create a GPO in the domain.
- Name the GPO and then Edit it.
- Expand Computer Configuration\Policies\Software Settings\Software installation. Right click on Software Installation, hover over New and select Package...
- Select the KerbPurge MSI from step 1. Click through the defaults and select "Assigned".
- Navigate to Computer Configuration\Preferences\Windows Settings\Registry\(null)\HKEY_LOCAL_MACHINE\SOFTWARE\
- Right click on Software and select New then Collection Item. Give it a name. In our example we did this twice so we have HKLM\Software\LOGbinder\KerbPurge.
- Right click on the new collection and select New Registry Item. Enter the Key Path to the New Collection you just created. For value name enter "IntervalMilliseconds". Select REG_DWORD for the value type and select decimal. In our example we entered 60000 for the Value data. This is the frequency at which KerbPurge will run which determines how quickly computers will see that they are a member in a new group and a member of a new subscription.
5.19. Eventlog-ForwardingPlugin Event ID 102 Error 5004 - subscription can not be created
From time to time you may create a subscription for an event log and the subscription is created, you see forwarders showing up as healthy but you get no events in the log. Checking the Eventlog-ForwardingPlugin log on the collector shows event ID's 102 as you see below:
This is normally due to the NETWORK SERVICE not having permissions to the log you are forwarding from the forwarders. First you need to get the full name of the log you are forwarding. This can be found in event viewer under the logs properties. For example, below is the full name for the Microsoft Windows AppID Operational log.
You will need to run the following command on the forwarders to give the access. You would most likely want to set this up via Group Policy.
wevtutil sl Microsoft-Windows-AppID/Operational /ca:O:BAG:SYD:(A;;0xf0007;;;SY)(A;;0x7;;;BA)(A;;0x1;;;BO)(A;;0x1;;;SO)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;S-1-5-20)
This gives the NETWORK SERVICE permissions to the log. Be sure that when you copy and paste it doesn't change the :( in SYD:(A to a sad face.
A breakdown of the above command:
wevtutil sl - this is the set log name for the wevtutil cmd
Microsoft-Windows-AppID/Operational - full name the log in our example
/ca:O:BAG:SYD - /ca is the channel to set the permissions
(A;;0xf0007;;;SY) - local system full access
(A;;0x7;;;BA) - Administrators read, write and clear access
(A;;0x1;;;BO) - Backup Operators read access
(A;;0x1;;;SO) - Server Operators read access
(A;;0x1;;;S-1-5-32-573) - Event Log Readers group read access
(A;;0x1;;;S-1-5-20) - NETWORK SERVICE read access
5.20. How to use a different user if already logged in with SSO
Supercharger is using the authentication by IIS. What if you are already logged in with one user in your browser, but you want to use Supercharger with another user?
The solution is simple. Open a new incognito / InPrivate window and navigate to the Supercharger page. You should now be prompted to log in. Here you can enter the user credentials you would like to use for Supercharger.
5.21. How to Install SQL Express manually with Supercharger
Install SQL Express
Download the latest version of SQL Express from Microsoft. In this article we are working with SQL Express 2019.
Run the installer. Click on Custom Install. Click next on Install Rules. For Feature Selection you can uncheck "SQL Server Replication" and "Machine Learning Services and Language Extension".
For "Instance Configuration" and "Server Configuration" you can choose any name or leave it default. For "Database Engine Configuration" be sure to select Mixed Mode and then enter a password that you will remember for the sa account.
SQL Server is now installed.
Create SQL Login for Supercharger
There are two ways to do this. Both are shown below.
Option 1
Open an administrator cmd prompt and run the following commands.
- Use a secure password in place of the ???????????????? as shown in the screenshot below. Obviously do not use the sample password we have used.
- During the SQL Server installation if you kept the default DB and instance names, then localhost\sqlexpress will work. If you create custom names these would be needed below.
sqlcmd -Slocalhost\sqlexpress
USE MASTER
CREATE LOGIN ScManagerDbUser WITH PASSWORD=N'????????????????', CHECK_EXPIRATION=OFF
GRANT CONNECT ANY DATABASE TO ScManagerDbUser
ALTER SERVER ROLE [sysadmin] ADD MEMBER ScManagerDbUser
exit
Option 2
As an alternative to the above step you can install SQL Server Management Studio and run the above cmd as a query as shown below:
Optional Step if using SQL Express 2019
Open Regedit. This step is only needed since we are installing SQL Express 2019.
- Navigate to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft SQL Server. Right click on the folder and create a new Key. Name it 130. It should show up in the list as shown in the inset of the image below.
Install Supercharger
Run Supercharger installer. On the setup screen you should see the following:
Click next on installer until it is complete.
Restart the server.
Configure Supercharger to use your custom SQL Server installation
Open a browser (Google Chrome is high recommended). Navigate to http://localhost/supercharger/explorer. It may take a couple of minutes but you should get a DB status screen similar to what's shown below. Click "Configure" next to where it says Bad Credentials.
Provide the name of the SQL Server using either localhost or the server name. (If SQL Server certificate is used, provide the same FQDN as in the CN of the certificate.)
The database name will be SUPERCHARGER.
The username is ScManagerDbUser and the password you specified in the steps above.
After you click Save, Supercharger should reload in the browser in a minute. If you see any errors that contain content related to SQL Server connection issues please perform the following additional step:
Configure port in SQL
Open "SQL Server Configuration Manager". Expand the configuration for this instance. Open the properties of the TCP/IP protocol. Click on the IP Addresses tab and scroll to the bottom section named IPAll. Next to TCP Port enter 1433. Apply and restart SQL Server service.
5.22. High Availability with Supercharger
With the use of Supercharger's Load Balanced Subscriptions, WEC can be setup and configured in a high availability environment. There are three areas that need to be configured for HA.
- Using VM replication for the VM where Supercharger Manager is installed
- There are various ways to configure this depending on your environment. This would be handled by your hypervisor administration team. They would configure replication of the VM where Supercharger Manager is installed. In the event of an outage, the hypervisor manages the failing and failover VM's.
- Modifying which WEC collectors are part of the Load Balancer in Supercharger
- In Supercharger there are load balanced subscriptions (LBS). One part of a load balanced subscription is the load balancer. The load balancer has multiple WEC collectors assigned to it. For HA configuration, there will be active and standby load balancers.
- Configuring the Target Subscription Manager to include the both active and failover collectors
- In your GPO (see #2 here) you would include your active and standby load balancers. This does not mean that all of these collectors will automatically start collecting events. Only collectors active in the load balancer will be collecting the events.
Use Case #1
An entire site goes down
In the diagram below, Hypervisor A contains the active Supercharger Manager server and active WEC collectors 1 through 3. The load balanced subscription exists on the active manager. Hypervisor B hosts the replicated Supercharger Manager server and 3 WEC collectors that are not yet part of the Load Balancer.
In the event of an outage of the entire site, hypervisor technology fails over to the standby Supercharger Manager server. The Supercharger admin will edit* the load balancer in Supercharger replacing collectors 1 - 3 with collectors 4 - 6. Since these collectors are also in the GPO's "Target Subscription Manager" setting the event forwarders will begin forwarding their events to these collectors at the next refresh interval.
Use Case #2
The Supercharger Manager server goes down
In the diagram below, Hypervisor A contains the active Supercharger Manager server and active WEC collectors 1 through 3. The load balanced subscription exists on the active manager. Hypervisor B hosts the replicated Supercharger Manager server and 1 WEC collector that is not yet part of the Load Balancer.
In the event of an outage of the Supercharger Manager, hypervisor technology fails over to the standby Supercharger Manager server. Since the hypervisor keeps the replicated server and its load balanced subscription up to date there is no need to modify the load balancer.
Use Case #3
A WEC collector goes down
In the diagram below, Hypervisor A contains the active Supercharger Manager server and active WEC collectors 1 through 3. The load balanced subscription exists on the active manager. Hypervisor B hosts the replicated Supercharger Manager server and 1 WEC collector that is not yet part of the Load Balancer.
In the event that a WEC collector has an outage (collector 3) the Supercharger admin will edit* the load balancer in Supercharger replacing collector 3 with collector 4.
Below is a screenshot showing a load balancer in edit mode. Assuming that collector 3 were to go down, your Supercharger admin would select Collector 4 and save/update the load balancer.
5.23. How to analyze where events are coming from and how many
Recently we had an issue with a Supercharger customer/ They had 40+ distributed subscriptions and two of their many collectors were having latency issues. After hours and hours of investigation, research and troubleshooting we identified the issue. Of their tens of thousands of forwarders, just a few (yes not few thousand or few hundred but a handful) were generating a huge amount of events in comparison to the rest. This resulted in an unbalanced load balanced subscription. As a result of this troubleshooting, our Event Count By Source utility was born. Just download the utility and run it on a collector against some of the logs. You will see how it totals events by source and sorts them in descending order.
This utility is intended to help you determine where forwarded events are coming from and in what quantity. It analyzes the specified log and counts events by source computer and source log. 3 tab delimited files are produced in the current directory named after the type of data, log name, and computer name allowing you to co-mingle output from multiple executions of the program.
The 3 files summarize event counts by source machine only, source log only and by log and machine. A 4th file simply documents the number of events in the log.
There is only one parameter - log name. For a list of logs run "get-winevent -listlog *".
Omit log name and it will default to ForwardedEvents.
Download Event Count By Source utility.
This is a free utility from LOGbinder (www.logbinder.com) which is a division of Monterey Technology Group, Inc.
(c) 2019 Monterey Technology Group, Inc (MTG). You are free to use and copy this program for lawful uses. Use at your own risk. By your use of this program you hold MTG harmless of any untoward results.
5.24. Why we don't use the global catalog or support domain-crossing for deterministic forwarder analysis or load balanced subscriptions
Domain boundaries in an AD Forest are far more complicated than people might think.
We cannot just simply change a port number and search the Global Catalog (GC) instead of a local domain controller because the GC, while it has a replica of each object, doesn’t have a replica of each property on that object. And a very important property missing is Last-Logon-Timestamp on computer accounts which we absolutely need in Supercharger for both load balanced subscriptions and deterministic forwarder analysis. Without that information we would not know about dormant computer accounts, which would result in very unbalanced subscriptions and bogus reporting of unhealthy forwarders.
We do not support load balanced subscriptions where the cohort group or LDAP query attempts to pull in computers from other domains as forwarders. This is because of related complexities. Because of the vast number of ways you can architect AD domains, trees and forests and trust relationships between them it is not feasible for us to build something that would work in every AD environment.
With the one requirement that collectors serve forwarders within their domain, we are able to support every AD architecture regardless of domains, trees and forests and trust relationships between them. It is rock solid, and it works in every AD environment.
Bottom line, if you need load balanced subscriptions and/or deterministic forwarder analysis, your collector needs to be in the same domain as its forwarders.
5.25. How to fix SqlException: Execution Timeout Expired errors
SQL Server connections timeout if the collectors are far from the manager.
Error:
You might get an error message like this:
An error has occurred. Windows will automatically restart the service. Supercharger Fatal Exception caught in:checkInWithManagerLoop C:\agent\_work\7\s\Mtg.Supercharger.Core\Controller\CommandEngine.cs line:105
System.Data.Entity.Infrastructure.RetryLimitExceededException: Maximum number of retries (3) exceeded while executing database operations with 'SuperchargerSQLExecutionStrategy'. See inner exception for the most recent failure.
---> System.Data.Entity.Core.UpdateException: An error occurred while updating the entries. See the inner exception for details.
---> System.Data.SqlClient.SqlException: Execution Timeout Expired. The timeout period elapsed prior to completion of the operation or the server is not responding. The statement has been terminated.
---> System.ComponentModel.Win32Exception: The wait operation timed out
Cause:
Supercharger uses SQL Server to store certain settings and other information and to communicate with the collectors. This communication happens through standard SQL Server protocols. If the network is slow, for example because of great geographical distance between the collector and manager, these communication connections could result in a timeout.
Solution:
Supercharger introduced some registry values to be able to control the timeouts. These are to be set in regedit on the respective collector under HKEY_LOCAL_MACHINE\SOFTWARE\MTG\Supercharger\Controller
Please remember that regedit defaults to hexadecimal values when entering the values. The values in this table are decimal values.
| Name | Type | Default value (decimal) | Sample value used by a customer between the USA and Europe (decimal) | Sample value used by a customer between the USA and Asia (decimal) |
| SqlConnectionTimeOutSeconds | DWORD | 15 | 30 | 60 |
| SqlExecutionStrategyDelaySeconds | DWORD | 10 | 10 | 40 |
| SqlExecutionStrategyRetryCount | DWORD | 3 | 3 | 9 |
5.26. Load Balancing with Jumbos
In addition to Load Balancing forwarders across collectors, Supercharger gives you the ability to analyze your environment and balance based on Jumbo Forwarders. What is a jumbo forwarder? A jumbo is an event forwarder (server/workstation) that generates an exponentially higher EPS rate than its cohorts. For example, let's say you have 10,000 forwarders with an average EPS of 500-1000. Of that 10,000 you have 10 file servers that are generating 5,000 EPS due to the authentication of users accessing its file shares. That is 5-10 times the average. This forwarder would fall in to the Jumbo Forwarder status.
In Supercharger on a Load Balancer there are three options on the Jumbos tab as shown in the screenshot below:
- Disabled: Jumbo Tracking and Balancing are not in use.
- Jumbo Tracking: This option will turn on analytics that Jumbo Balancing, if enabled, will use to move around high EPS producers.
- Once you enable Jumbo Tracking, Supercharger will begin to analyze the EPS of the event forwarders on the related Load Balancer. The default frequency is a rebalancing every 4 hours with the averages being analyzed over the past 24 hour period. These can be modified using the JumboLevelingFrequencyHours and JumboLevelingObservationHours found in the Global Setting Overrides in Supercharger's settings. This setting only enables analyzing of the statistical data, it doesn't perform any balancing of any kind. After enabling Jumbo Tracking and allowing a period of data to be created and analyzed, you can simulate Jumbo Balancing by clicking on the "Simulate Jumbo Balancing" button.
- Once you enable Jumbo Tracking, Supercharger will begin to analyze the EPS of the event forwarders on the related Load Balancer. The default frequency is a rebalancing every 4 hours with the averages being analyzed over the past 24 hour period. These can be modified using the JumboLevelingFrequencyHours and JumboLevelingObservationHours found in the Global Setting Overrides in Supercharger's settings. This setting only enables analyzing of the statistical data, it doesn't perform any balancing of any kind. After enabling Jumbo Tracking and allowing a period of data to be created and analyzed, you can simulate Jumbo Balancing by clicking on the "Simulate Jumbo Balancing" button.
- Jumbo Balancing: This option will cause Supercharger to balance or move around high EPS producers. Jumbo balancing uses the following metrics along with EPS to determine which forwarders need to be moved to which collectors:
- Volatility is the measure of how many Jumbo forwarders are re-allocated to a different collector by the balancing algorithm
- Churn is the measure of how much EPS fluctuates on forwarders causing them to move in and out of Jumbo status
- Balance is the measure of how close the worst balanced collector's EPS is to the ideal EPS per collector
5.27. How To Upgrade Supercharger
Please note that if any of the following situations apply, we advise you to contact our support team via our support portal prior to upgrading:
- you are upgrading from 20.1.53 or earlier and use Load Balanced Subscriptions or
- you are using a custom installation of SQL Server for Supercharger.
If you are upgrading to the latest version on our website and are currently on version 22.8.1 or earlier then you must do an incremental upgrade. Please download and install 22.8.2 first. After installation of that version, only then, you can proceed to install our current version.
When major updates are released you will receive a newsletter from us. To verify that your email is in our bulletins database you can check here: https://www.logbinder.com/Newsletter/
We also post Supercharger's version history here: Supercharger Version History
For standard installations, an in-place upgrade is all that is needed to upgrade Supercharger Manager. Simply download and run the latest installer on your existing install of Supercharger Manager. The installer will upgrade the manager. All of the WEC collectors that are managed by Supercharger will update themselves automatically. It's that simple.
If you would like to perform a backup on the Supercharger Manager prior to upgrading then please follow the steps in this article.
5.28. HTTP Error 500.31 after installation
It is possible that you may receive a 500.31 on the initial load of Supercharger after installation with the error message "The specified version of Microsoft.NetCore.App or Microsoft.AspNetCore.App was not found." after updating or installing Supercharger.
This can most likely be fixed with the following steps:
1. Uninstall .NET Core 3.X.X.
2. Run the Supercharger installer again to Repair the installation. In the pre-requisites screen during installation be sure that the .NET Core 3.X.X install is selected.
After the repair installation Supercharger should load without the HTTP Error 500.31.
5.29. Migrating Supercharger to Another SQL Server
NOTE: The instructions below apply if you already have Supercharger installed and configured. The steps below will migrate the Supercharger data (load balancers, load balanced subscriptions, performance history, etc...) to another SQL Server. If you are setting up a new installation of Supercharger and want to use your own SQL Server and not the SQL Server that installs by default with Supercharger, then please see this article.
We strongly recommend that you use the SQL Server that installs by default with Supercharger.
Supercharger does not use SQL Server in the traditional sense as a relational database nor does it store the organization’s business data or data normally considered to be specifically scoped into compliance regulations. Supercharger’s use of SQL server is for storage of system information and as an inter-process communication facility between manager and controllers.
Supercharger is designed to use a local instance of SQL Server Express 2016 to store:
- Status of Windows Event Collectors
- Performance monitoring data
- Windows Event Collection configuration settings
Supercharger automatically installs, secures and configures SQL Server Express on the manager. For Free Edition, we do not offer support for using a different installation of SQL Server. For Enterprise Edition customers with an active support contract, we determine on a case-by-case basis whether to support a customer-installed instance of SQL server on another system. These are instructions related to such a scenario.
We believe Supercharger will work okay on a day-to-day basis without sysadmin, but it is required whenever you register a new Windows Event Collector or upgrade Supercharger to a new version. Supercharger should also work with most earlier versions of SQL Server including 2014.
All steps below assume that the existing SQL Server is using a Default Instance.
Steps 1 through 5 are on the new and/or existing SQL Server.
- Install SQL Server 2016 or later.
- Mixed Mode Authentication
- Service Broker enabled
- TCP protocol enabled
- Open port 1433 in Windows Firewall for SQL Server using this cmd: netsh advfirewall firewall add rule name= "SQL Server 1433 Inbound" dir=in action=allow protocol=TCP localport=1433
- Create a folder for temporary import purposes. These instructions assume this folder is C:\SCMIG. This folder can be deleted after the migration. Create the folder using this cmd: md c:\SCMIG
- Create another folder where the migrated database files will be stored permanently by SQL Server. In these instructions we are using C:\ScDB. Create the folder using this cmd: md c:\ScDB
- Create a user account and database for Supercharger. Specify a secure password in place of ??? Run the following command to perform this step: sqlcmd -Q "USE MASTER; CREATE LOGIN ScManagerDbUser WITH PASSWORD=N'???', CHECK_EXPIRATION=OFF; GRANT CONNECT ANY DATABASE TO ScManagerDbUser; ALTER SERVER ROLE [sysadmin] ADD MEMBER ScManagerDbUser; CREATE DATABASE Supercharger"
If any errors are reported in this step, STOP, take a screen print and contact support. - Steps 6 through 8 are on the Supercharger Manager server. Stop the Supercharger Controller service and disable it using
- sc stop "Supercharger Controller"
- sc config "Supercharger Controller" start=disabled
- Create a folder for backup purposes by running md c:\SCMIG. These instructions assume this folder is C:\SCMIG. This folder can be deleted after the migration.
- Backup the Supercharger registry settings by running reg export HKLM\Software\MTG\Supercharger\Manager c:\scmig\Backup.reg
If any errors are reported in this step, STOP, take a screen print and contact support. - On the SQL Server, target Supercharger in the registry. Run reg add HKLM\Software\MTG\Supercharger\Manager /v Server /d ??? /f
Replace ??? with the new SQL Server's DNS name. If the existing SQL Server is a named instance, that must be added as sql.acme.com\instance.
If any errors are reported in this step, STOP, take a screen print and contact support. - On the Supercharger Server, backup the existing Supercharger DB. Run sqlcmd -Q "BACKUP DATABASE supercharger TO DISK = 'C:\scmig\sc.BAK'"
If any errors are reported in this step, STOP, take a screen print and contact support. - Shutdown SQL Services and disable it. Use these commands:
- sc stop "MSSQL$SUPERCHARGER"
- sc config "MSSQL$SUPERCHARGER" start=disabled
-
Copy the sc.BAK file from step 10 above to the new SQL Server. Again, these steps assume this folder is C:\SCMIG\ on both servers.
-
Restore the database to the new SQL Server. In these instructions we are using C:\SCMIG\ as our database backup location from step 3 above. We are also using C:\ScDB from step 4 above. Run these two commands on the new SQL Server:
- sqlcmd -Q "EXEC SP_ADDUMPDEVICE 'DISK', 'SCDUMP', 'C:\scmig\SC.BAK';"
- sqlcmd -Q "RESTORE DATABASE Supercharger FROM SCDUMP WITH REPLACE,MOVE 'Supercharger' TO 'C:\ScDB\Supercharger.mdf', MOVE 'Supercharger_log' TO 'C:\ScDB\Supercharger_log.ldf' "
If any errors are reported in this step, STOP, take a screen print and contact support. -
On the SQL Server create the special registration account for the collectors. This is a known password, but the account only has INSERT ONLY permissions to the registration request table as part of the secure admin-controlled collector agent registration process. Run this command:
sqlcmd -Q “CREATE LOGIN ScControllerRegistrationUser WITH PASSWORD='xR0oa5bB9Po98DS3jgz', CHECK_EXPIRATION=OFF; USE Supercharger; ALTER USER ScControllerRegistrationUser WITH LOGIN = ScControllerRegistrationUser;”
If any errors are reported in this step, STOP, take a screen print and contact support. -
Test connectivity to the new SQL Server. If this fails, you will have to diagnose this issue. The first to check is to make sure that the firewall is configured correctly according to step 2 above. The easiest way to test connectivity is to follow the steps in this blog post on the Supercharger Manager server.
-
On the Supercharger Manager server, set the Supercharger Controller service back to Automatic and Enable it.
- sc config "Supercharger Controller" start=auto
- sc start "Supercharger Controller"
- Open Supercharger and wait. You should receive the Supercharger Database and Manager and Service Status page. Click on "Configure".
- Enter the required information.
- Server = FQDN of the new SQL Server
- Database, Username and Password were set in Step 5 above.
- After clicking on "Save, if you receive the same previous "BadCredentials" screen, please verify that the SQL account (in our example ScManagerDbUser) is not locked.
-
Verify that the Supercharger service is running and that you can see the Explorer page. The manager collector should be yellow or green, not red. All other collectors will be red.
-
Open the Local Machine page and copy the current authenticator key to your clipboard.
-
On each collector you will have to perform steps 21 through 26. Stop the Supercharger Controller service. Run sc stop "Supercharger Controller"
-
Add the registration authenticator to the registry where ??? is the authenticator key. Run this command:
reg add HKLM\Software\MTG\Supercharger\Controller /v RegistrationAuthenticator /d “???” /f
If any errors are reported in this step, STOP, take a screen print and contact support. -
Modify the Server registry value for the collector. Run this command and for ??? use the FQDN of the new SQL Server:
reg add HKLM\Software\MTG\Supercharger\Controller\Db /v Server /d "???" /f -
On each collector you will also have to clear the login key in the registry. Run this command:
reg add HKLM\Software\MTG\Supercharger\Controller\Db /v Login /d "" /f -
Start the Supercharger service using this command: sc start "Supercharger Controller"
-
In Supercharger Manager, you will eventually receive an "Approve" button for each collector from the previous two steps. Click approve, confirm it and in a few minutes the collector should change from red to yellow or green.
5.30. How To Configure Windows Server Core as a WEF Collector in Supercharger
This article assumes that you have the Server Core collector:
- added to the domain
- added as a Target Subscription Manager in your GPO
- enabled with Remote Desktop
- In Supercharger Manager, click on Local Machine in the left menu.
- Click on the "Download and launch collector installer" link.
- Now we need to share a folder on Server Core so that we can copy the installer to the server. Connect to Server Core's cmd line and share your folder. Below we are just sharing the root.
- From Supercharger Manager server connect to the shared folder from step 3. Copy the installer to that folder.
- In Supercharger go back to the Local Machine tab on the left menu. Make a note of the SQL Server and the Authenticator.
- In Server Core, using cmd line or PowerShell run the installer. You will have to run this command from the folder where the installer is saved:
.\SuperchargerControllerSetup.exe /quiet /L*V C:\msi.log /qn SERVER_PROP="[insert SQL Server DNS name]" AUTH_PROP="[insert Authenticator]"
**Note we have added the "/L*V C:\msi.log" switch which is optional but will help if you have any errors during the install. - You should see some installer dialogues and then the C:\ prompt. The dialogues should disappear after a few seconds.
- In Supercharger Manager you should soon see the Approve button for the new collector.
You can now use this collector as you would with a regular server OS.
5.31. How to install Supercharger Manager on Windows Server Core
This article assumes that you have the Server Core server:
- added to the domain
- enabled with Remote Desktop
- Download the latest Supercharger Manager installer from LOGbinder.com.
- Now we need to share a folder on Server Core so that we can copy the installer to the server. Connect to Server Core's cmd line and share your folder. Below we are just sharing the root.
- From the server that has the Supercharger Manager installer, connect to the shared folder from step 2. Copy the installer to that folder.
- In Server Core, using cmd line or PowerShell run the installer. You will have to run this command from the folder where the installer is saved:
.\SuperchargerSetup.exe /quiet /L*V C:\msi.log
**Note we have added the "/L*V C:\msi.log" switch which is optional but will help if you have any errors during the install. - You should see various installer dialogues and then the C:\ prompt. The dialogues should disappear after a few seconds.
- Depending on the speed of your server and its resources it make take a few minutes for the entire installation to complete. Go to another server and open the address to Supercharger Manager in the browser. In the screenshot below the IP of the server core server is 10.42.1.159. The URL for your install will be http://[your server core IP]/supercharger
You can now use this Supercharger Manager for managing WEC in your environment.
5.32. Configure Cross Domain Forwarding
What is cross domain forwarding?
How does it work in Supercharger?
What to expect when you upgrade a current installation?
5.33. Delete a Corrupted Custom Event Log
Supercharger has the ability to create and delete custom event logs in Windows. If an event log gets corrupt and is not removable within Supercharger, you can remove it with the following steps.
1. Navigate to this location in the registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Channels\
2. Locate the corrupt log in this list. Please note that Supercharger created logs will be named "Supercharger-Destination-CustomNameHere/Log". Make a note of the following two items:
GUID value of the "OwningPublisher" string name. You will need this in step 4.
File location of the "File" string. You will need this in step 5.
3. Delete the key in step 2.
4. Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers\ and delete the key matching the GUID from Step 2.
5. Navigate to the file location from Step 2 and delete the evtx file. (In case of "File in use" error, try rebooting the computer for the file to get released.)
6. Most Used
6.1. Download Supercharger
Click here to download Supercharger.
See 5.27. How To Upgrade Supercharger for further instructions.
6.2. Request Instant Quote
Supercharger Enterprise - Pricing and Licensing
Pricing
Licensing
Supercharger Enterprise is licensed based on the number of different computers that send events to your Windows Event Collectors under management by Supercharger.
Deploy Windows Event Collecters and Supercharger Managers as you like, the number of Collectors or Managers doesn't matter.
How to Purchase
Click here for an instant price quote.
Contact our sales team to place an order.
6.3. LOGbinder Newsletter
Subscribe here to receive news, alerts and security bulletins for Supercharger.
7. FAQ: Frequently Asked Questions
7.1. Collector-Initiated (Pull) vs Source-Initiated (Push)
There are two types of WEC subscription methods: Source-Initiated (aka push) and Collector-Initiated (aka pull). Supercharger creates source-initiated subscriptions for various reasons, for example, performance and security reasons. Below is a comparison chart of each.
Collector vs Source-Initiated Windows Event Subscriptions
***In the chart below, all bold sections are not an issue when using Supercharger for WEC***
| Aspect | Collector-Initiated Subscriptions | Source-Initiated Subscriptions |
|---|---|---|
| Scalability | Less scalable in large environments due to the load on the collector. | Highly scalable as each source initiates the connection, reducing the load on the collector. |
| Ease of Management | Easier initial setup with centralized control. | Requires more complex setup but sources can dynamically discover collectors. |
| Configuration Complexity | Setup and maintenance overhead is complex due to each forwarder having to be manually added to each subscription. | More complex configuration due to the need for individual source settings. |
| Network Efficiency | Can generate more network traffic due to continuous polling by the collector. | More efficient as sources send data only when events occur, reducing unnecessary traffic. |
| Resilience | Event collection stops if the collector goes down, less resilient to network issues. | Sources can buffer events during network issues and send them when connectivity is restored. |
| Security | Collector needs a user account and password on each forwarder. The collector must handle multiple connections. Each forwarder has to be open to incoming connections from the collector(s). | Requires secure communication setup for multiple sources, more challenging to monitor traffic from all sources. |
| Dynamic Environments | Less suitable for environments with frequent changes in sources, manual updates needed for new or removed sources. | Well-suited for dynamic environments as sources can dynamically find and connect to collectors. |
| Performance Bottlenecks | Potential performance issues if the collector is overwhelmed by too many source connections. | Reduces the risk of performance bottlenecks at the collector as each source manages its own connection. |
| Network Overhead | Higher due to continuous polling of sources by the collector. | Lower as data is sent only when events occur, optimizing network usage. |
| Centralized Control | Provides centralized control over the subscription, simplifying management in very small environments. | Less centralized control, but offers flexibility and scalability. |